Once again a large company has suffered a huge data breach, putting millions of innocent customers at risk. Customers of British popular high street stores Currys PC World, Carphone Warehouse, and Dixons Travel have been warned that a huge data breach has occurred involving 5.9 million payment cards and the […]
Two Critical flaws affect Schneider Electric U.motion Builder. Patch them now!
Schneider Electric has patched last week four flaws affecting the U.motion Builder software, including two critical command execution vulnerabilities. Schneider Electric U.motion Builder is a tool designed for creating projects for U.motion devices that are used in critical manufacturing, energy, and commercial facilities industries. “This exploit occurs when the submitted data of […]
Rootkit-Based Adware Wreaks Havoc Among Windows 10 Users in the US
When it was released back in 2015, one of the main perks of Windows 10 was the improved security features that made it harder for rootkits to get a foothold on Microsoft’s new OS. But three years later, security researchers from Romania-based antivirus vendor Bitdefender say they’ve discovered a new […]
Banco de Chile admits losing $10 million in disk-wiping malware attack
Banco de Chile, the second largest bank in the country, released a public statement confirming a major malware attack that breached its computer systems on May 24, shutting down bank operations. The hackers used a disk-wiping malware to cause the outage in order to distract attention from their original target – the […]
Quick Heal detects 2 banking Trojans targeting Indian Android users
IT company Quick Heal on Tuesday warned that two new banking trojans (malware designed to steal financial data) targeting Android are hitting users in India to access confidential data. The Trojans, named “Android.Marcher.C » and « Android.Asacub.T », operate by exploiting user behaviour of android mobile users and imitating notifications from leading banking […]
Satori botnet is back again, experts observed a surge in port scan activity associated with it
This week, security experts observed a surge in port 8000 scan activity, researchers at Qihoo 360 Netlab determined that the unusual activity was associated with Satori IoT botnet. Experts from Qihoo 360 Netlab discovered that the author of the Satori botnet have integrated a the proof-of-concept (PoC) code for the XionMai web server software package after it was […]
VMware addresses a critical remote code execution vulnerability in AirWatch Agent
VMware has found a critical remote code execution vulnerability in the AirWatch Agent applications for Android and Windows Mobile. The agent is installed by users on a mobile device in order to allow the AirWatch to manage it. The flaw, tracked as CVE-2018-6968, “may allow for unauthorized creation and execution of […]
Thousands of Android Devices Running Insecure Remote ADB Service
Despite warnings about the threat of leaving insecure remote services enabled on Android devices, manufacturers continue to ship devices with open ADB debug port setups that leave Android-based devices exposed to hackers. Android Debug Bridge (ADB) is a command-line feature that generally uses for diagnostic and debugging purposes by helping […]
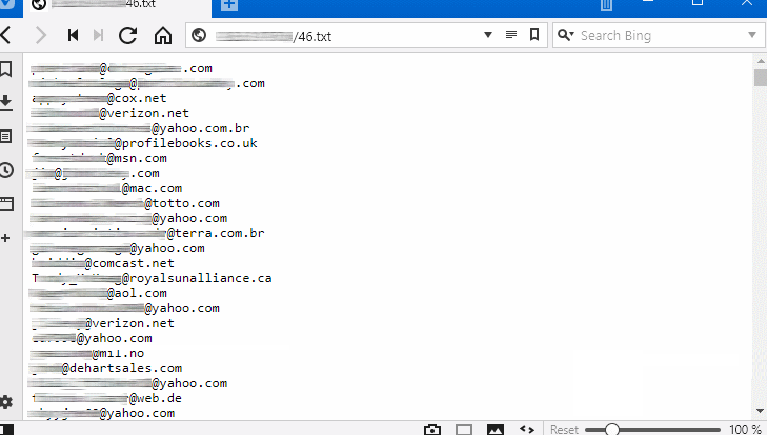
Trik Spam Botnet Leaks 43 Million Email Addresses
Over 43 million email addresses have leaked from the command and control server of a spam botnet, a security researcher has told Bleeping Computer today. The leaky server came to light while a threat intelligence analyst from Vertek Corporation, was looking into a recent malware campaign distributing a version of the […]
Chinese hackers stole 614 gigabytes of US Navy’s anti-ship missile data
In January and February 2018, the computers belonging to a U.S. Navy contractor were compromised by hackers backed by the Chinese government – As a result, highly sensitive data was accessed and stolen. The stolen data was related to undersea warfare and includes classified information on future plans regarding the development of supersonic anti-ship […]