A new Variant of Mirai Malware recently started recruiting devices IoT written by @mezy1337. This malware uses hosted servers to find and infect new victims . Samples were served from the IP 46.243.189.102 Malware Samples: 10f0429cee0a52a569c14bee727f3f66:VAMPWROTESATORI.x86 3672ec68839541e7263f491ce9407ec9:vermelho.i686 156e888c32c38677ae970b3a944e8e0e:vermelho.arm7 b125deca7501e13667eaf0804d44a5a7:vermelho.m68k 1406cf02d6af6c2a33f86f93feebdc55:cpuvuln.x86 11e887988687b66cb29a5d395797b0e6:vermelho.mips64 e524abeb037e5295d8341519883ec733:vermelho.mips fb926ee35a240e1bd6761c2d416ef392:vermelho.i486 f9e73ae79a618df43b3bf0ff06818979:vermelho.x86_64 b89870c84f62606b8c1337f120198362:vermelho.sh4 98c35212c42a39cac579afbfb271ba9c:vermelho.arm5 9229e931e806b30967863a1d0f78fb3e:vermelho.mipsel d54456cc11c710f6b4431e0e9593ac02:vermelho.arm6 93b642bb132f757617ff3221ebefab53:vermelho.powerpc-440fp 1da0c2b1c860c334b3220687b15c1e95:vermelho.powerpc c19c397f73adbb3a8247f8670a895e30:vermelho.x86 53b539f6f9824d538f5a28f29ba2e9c4:vermelho.arm4 fb94e136404fcd1de3ba95cb09d8f6ba:vermelho.sparc […]
Most Advanced Backdoor Obfuscation and Evasion Technique That used by Hackers
Cybercriminals are using the most sophisticated techniques to bypass the security controls in various organization such as IT, medical, manufacturing industries, energy sectors, even government entities. Sometimes developers are creating a backdoor for a legitimate purpose such as maintenance and easy accessibility during the technical issue via a remote location. But […]
Dark Web Malware Builder Allow Attackers To Create Malware That Steals Passwords & Credit Card Data
Researchers from Checkpoint spotted a free online builder for building customized binaries for the popular info-stealer Azorult malware that steals user passwords, credit card information, cryptocurrency related data. The Gazop service emerged as a result of the source code leak of Azorult’s panel version 3.1 and 3,2. the free Gazorp service […]
Phishing Attack Uses Azure Blob Storage to Impersonate Microsoft
Even though phishing attacks can be quite convincing, a give away is when diligent users notice that the login form is unsecured or the SSL certificate is clearly not owned by the company being impersonated. A new Office 365 phishing attack utilizes an interesting method of storing their phishing form […]
APT38: Details on New North Korean Regime-Backed Threat Group
Today, we are releasing details on the threat group that we believe is responsible for conducting financial crime on behalf of the North Korean regime, stealing millions of dollars from banks worldwide. The group is particularly aggressive; they regularly use destructive malware to render victim networks inoperable following theft. More […]
Experts found 9 NAS flaws that expose LenovoEMC, Iomega Devices to hack
Experts discovered nine vulnerabilities affecting NAS devices that could be exploited by unauthenticated attackers to access protected content. Nine flaws affecting NAS devices could be exploited by unauthenticated attackers to access protected content. The vulnerabilities are traked as CVE-2018-9074, CVE-2018-9075, CVE-2018-9076, CVE-2018-9077, CVE-2018-9078, CVE-2018-9079, CVE-2018-9080, CVE-2018-9081 and CVE-2018-9082. According to Lenovo, the flaws affect 20 models of network attached storage […]
New Danabot Banking Malware campaign now targets banks in the U.S.
According to malware researchers from Proofpoint, DanaBot attackers launched a new campaign aimed at banks in the United States. A couple of weeks ago, security experts at ESET observed a surge in activity of DanaBot banking Trojan that was targeting Poland, Italy, Germany, Austria, and as of September 2018, Ukraine. DanaBot is a multi-stage modular […]
INSTAGRAM DOWN: APP NOT WORKING AS IT REFUSES TO LOAD PEOPLE’S PICTURES AND PROFILES
UPDATE: Instagram is now back online after almost an hour-long outage. It’s still unclear what caused the problems but users are now able to access their account. ORIGINAL STORY: Instagram users are facing a morning without access to the popular social media service as both the app and website appear to be down […]
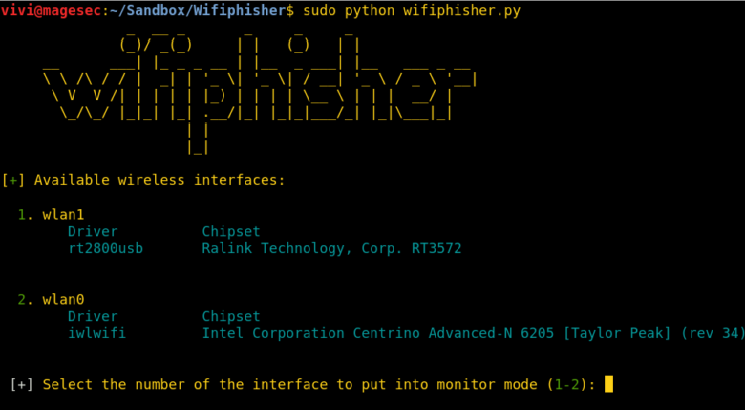
WifiPhisher – WiFi Crack and Phishing Framework
Wifiphisher is an open source framework that can be utilised for red team engagements for wireless networks through Man in the Middle attacks. The tool is capable of using the modern wifi association techniques, such as Known Beacons, KARMA, and Evil Twin. With the ‘Known Beacons’ technique, Wifiphisher broadcasts ESSIDs […]
Researchers associated the recently discovered NOKKI Malware to North Korean APT
Security experts from Palo Alto Networks have collected evidence that links the recently discovered NOKKI malware to North Korea-Linked APT. Researchers from Palo Alto Networks have spotted a new variant of the KONNI malware, tracked as NOKKI. that was attributed to North Korea-linked attackers. NOKKI borrows the code from the KONNI malware, the latter […]