L’ONU n’a pas divulgué publiquement une attaque de piratage majeure dans ses systèmes informatiques en Europe – une décision qui pourrait mettre le personnel, d’autres organisations et des individus en danger, selon les défenseurs de la protection des données. Le 30 août 2019, des responsables informatiques travaillant dans les bureaux […]
le ransomware Sodinokibi frappe encore, Travelex ammené à payer 3 M$
Le spécialiste en échanges de devises internationales Travelex a été touché par le ransomware Sodinokibi. Depuis le 31 décembre 2019 tous ses services en ligne sont inaccessibles. Le paiement d’une rançon de 3 millions de dollars aurait été demandée.
La grande compétition « Capture The Flag » de TT
La grande compétition « Capture The Flag » de TT TT et Keystone vous invitent à participer au grand challenge CTF qui aura lieu du 15 au 16 Janvier , 24 heures non-stop. Il s’agit d’une opportunité pour valoriser votre talent en matière de cyber-sécurité, s’affronter aux meilleures équipes tunisiennes et gagner […]
Citrix NetScaler/ADC Critical Flaw (CVE-2019-19781)
Vulnerability Description Citrix has indicated that an unauthenticated attacker can exploit this flaw to perform arbitrary code execution. Although details from Citrix are minimal, VERT’s research has identified three vulnerable behaviors which combine to enable code execution attacks on the NetScaler/ADC appliance. These flaws ultimately allow the attacker to bypass […]
Android’s January 2020 Update Patches 40 Vulnerabilities
Google on Monday published the first Android security bulletin for 2020, with patches for 40 vulnerabilities, including a critical flaw in the Media framework. The Android Security Bulletin for January 2020 was split into two parts: the first addresses 7 vulnerabilities in Framework, Media framework, and System, while the second includes fixes […]
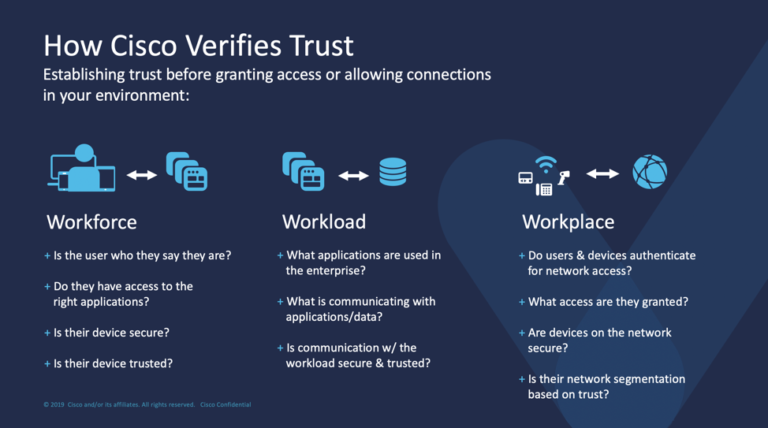
An Overview of Zero Trust Architecture, According to NIST
NIST recently released a draft publication, SP 800-207: Zero Trust Architecture (ZTA), an overview of a new approach to network security. While ZTA is already present in many cybersecurity policies and programs that sought to restrict access to data and resources, this document is intended to both “abstractly define” ZTA and […]
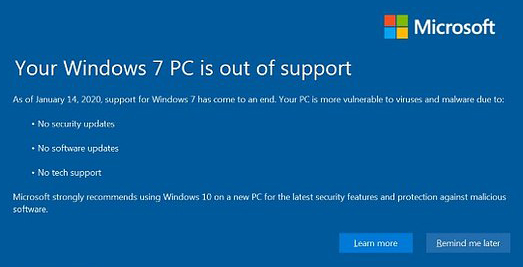
PCs still running Windows 7 will soon be significantly more at risk of ransomware
PCs still running when Windows 7 reaches end of life on the 14th of January will be significantly more at risk of ransomware, Veritas Technologies has warned. According to experts, 26% of PCs are expected to still be running the Microsoft software after support for patches and bug fixes end. The vulnerability […]
Microsoft Phishing Scam Exploits Iran Cyberattack Scare
An attacker is attempting to take advantage of the recent warnings about possible Iranian cyberattacks by using it as a theme for a phishing attack that tries to collect Microsoft login credentials. With the rising escalations between the United States and Iran, the U.S. government has been issuing warnings about possible cyberattacks by […]
Car Hacking Hits the Streets
The top-three carmakers sell only connected vehicles in the United States – and other manufacturers are catching up – creating a massive opportunity for attacks, which black-hat hackers are not overlooking. (image by Tomasz Zajda, via Adobe Stock) In 2020, the connected-car market will reach a tipping point, with the […]
Mozilla patches Firefox zero-day
Mozilla released today Firefox v72.0.1, a new version of the Firefox web browser that fixes a vulnerability that’s actively exploited in the wild. The vulnerability impacts IonMonkey, which is a JavaScript JIT compiler for SpiderMonkey, the main component at Firefox’s core that handles JavaScript operations (Firefox’s JavaScript engine). The vulnerability […]