The genuine option is to buy a computer with Linux pre-installed. Why? Well, this allows you know that all the hardware is compatible, as the retailer has tested it beforehand. Not to state, you are supporting the Linux society this way. Buying a Windows PC even when you delete Windows […]
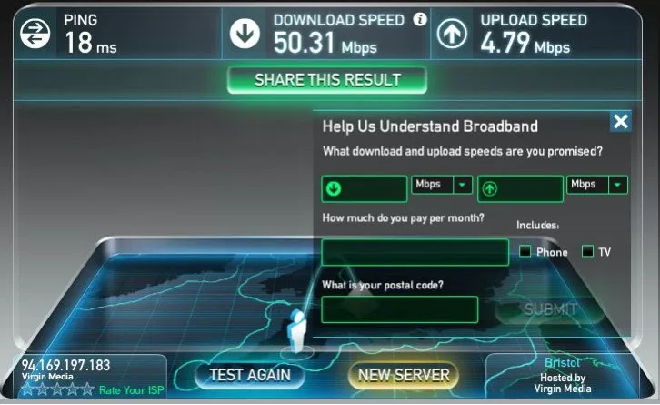
UK government has ordered telecom companies to stop using “upto” in their broadband speeds
In future, adverts must be based on what is possible to at least half of consumers at peak times. It follows study that suggested broadband broadcasting can be misleading for customers. The Advertising Standards Authority (ASA) examined into consumers’ perception of broadband speed claims and discovered that many were confused […]
Busy Browsers attract Black Friday Burglars
Black Friday 2017: time to fire up your charge cards and your PC for some online shopping! On second thought, first review the risks, then check your password hygiene and make sure your security solution is up to date. Have you ever thought about what is going on in your […]
Firefox to collaborate with HaveIBeenPwned to alert users on data breach
Mozilla is joining hands with popular data breach notification website HaveIBeenPwned.com (HIBP) to send an in-browser alert to Firefox browser users if they are visiting a site that was previously hacked and whether their login credentials have been involved in a data breach. “This is an addon that I’m going to be […]
Tips for Making Your Business Secure from Digital Crimes
Things may be going well for your business and if so great. But there’s always the threat of cybercrime looming over your online ventures. Whether it is to initiate a marketing campaign or to go about day-to-day communications through emails; today every business has an online presence as everything is […]
MS Office Built-In Feature Could be Exploited to Create Self-Replicating Malware
Earlier this month a cybersecurity researcher shared details of a security loophole with The Hacker News that affects all versions of Microsoft Office, allowing malicious actors to create and spread macro-based self-replicating malware. Macro-based self-replicating malware, which basically allows a macro to write more macros, is not new among hackers, […]
Trickbot Gang Evolves, Incorporates Account Checking Into Hybrid Attack Model
Individuals who reuse login credentials across multiple sites are more susceptible to account checking attacks, which occur when threat actors use credentials stolen from past database breaches or compromises to gain unauthorized access to other accounts belonging to the same victims. However, the process of mining compromised data for correct […]
Uber Hid 2016 Breach, Paying Hackers to Delete Stolen Data
Uber Hid 2016 Breach, Paying Hackers to Delete Stolen Data SAN FRANCISCO — Uber disclosed Tuesday that hackers had stolen 57 million driver and rider accounts and that the company had kept the data breach secret for more than a year after paying a $100,000 ransom. The deal was arranged […]
Troldesh Nabs Top Ransomware Spot
The most prolific ransomware strain these days is Troldesh, aka Crysis, which claims hundreds of sub-variants, according to analysis from Bitdefender. In its latest report, based on trends in its global network of more than 500 million sensors and honeypots, Bitdefender found that during 2017 alone, the number of new […]
ProtonMail bolts on an encrypted contacts manager and digital signing for contacts
Another neat addition to end-to-end encrypted email client ProtonMail: It’s added a zero-access encrypted contacts manager that also digitally signs the contact info you store in it. The new features have been added to v3.12 of ProtonMail’s web client, with the Swiss-based startup saying it’s working on also bringing the […]