Researchers at CyberArk Labs have created a post-intrusion attack technique known as a Golden SAML that could allow an attacker to fake enterprise user identities and forge authentication to gain access to valuable cloud resources in a federation environment. “Using this post-exploit technique, attackers can become any user they want […]
Data release: list of websites that have third-party “session replay” scripts
Here’s the list of 1,239 popular websites using third-party “session replay” scripts to record your every keystroke and mouse movement. In a recent study we analyzed seven “session replay” services and revealed how they exfiltrate sensitive user data. Here we release the data behind our study, specifically, the list of […]
OVH choisit Ooredoo Tunisie pour un hébergement sécurisé et réglementaire des noms de domaines ».tn » et » تونس. » sur le territoire tunisien
Ooredoo Tunisie, opérateur-hébergeur leader, et OVH, leader européen du cloud, ont scellé un partenariat visant à rapatrier les serveurs DNS de l’ensemble des noms de domaine gérés par OVHportant l’extension «.tn » ou « تونس.» sur le territoire tunisien. Ces données seront recueillies dans le datacenter de l’opérateur situé à Mghira et […]
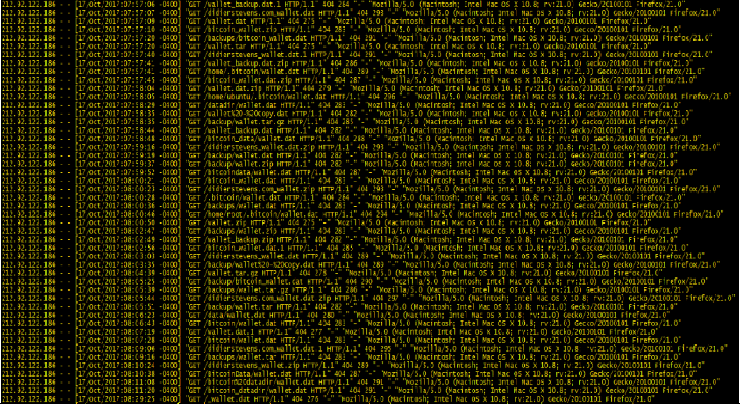
There’s Some Intense Web Scans Going on for Bitcoin and Ethereum Wallets
With both Bitcoin and Ethereum price hitting all-time highs in the past seven days, cyber-criminals have stepped up efforts to search and steal funds stored in these two cryptocurrencies. These mass Internet scanning campaigns have been recently picked up by various honeypots installed by security researchers across the Internet. Scans […]
Only 12% or organizations are likely to detect a sophisticated cyber attack
Organizations believe that today’s cyber threat landscape places them at high risk of cyber attacks. The EY survey of nearly 1,200 C-level leaders of the world’s largest and most recognized organizations examines some of the most urgent concerns about cybersecurity and their efforts to manage them. Findings show that […]
Dell has Launched Five New PC’s with Linux Pre-Installed
The genuine option is to buy a computer with Linux pre-installed. Why? Well, this allows you know that all the hardware is compatible, as the retailer has tested it beforehand. Not to state, you are supporting the Linux society this way. Buying a Windows PC even when you delete Windows […]
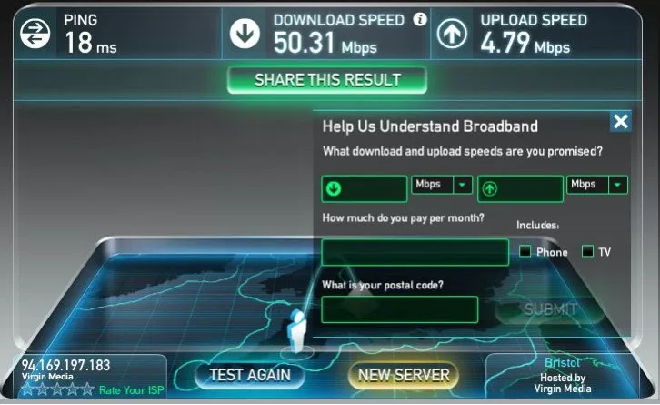
UK government has ordered telecom companies to stop using “upto” in their broadband speeds
In future, adverts must be based on what is possible to at least half of consumers at peak times. It follows study that suggested broadband broadcasting can be misleading for customers. The Advertising Standards Authority (ASA) examined into consumers’ perception of broadband speed claims and discovered that many were confused […]
Busy Browsers attract Black Friday Burglars
Black Friday 2017: time to fire up your charge cards and your PC for some online shopping! On second thought, first review the risks, then check your password hygiene and make sure your security solution is up to date. Have you ever thought about what is going on in your […]
Firefox to collaborate with HaveIBeenPwned to alert users on data breach
Mozilla is joining hands with popular data breach notification website HaveIBeenPwned.com (HIBP) to send an in-browser alert to Firefox browser users if they are visiting a site that was previously hacked and whether their login credentials have been involved in a data breach. “This is an addon that I’m going to be […]
Tips for Making Your Business Secure from Digital Crimes
Things may be going well for your business and if so great. But there’s always the threat of cybercrime looming over your online ventures. Whether it is to initiate a marketing campaign or to go about day-to-day communications through emails; today every business has an online presence as everything is […]