A piece of crypto-mining malware is using sophisticated tools for its operations, including a Windows exploit linked to the National Security Agency, security researchers warn. Dubbed WannaMine, the crypto-mining worm spreads using EternalBlue, the NSA-linked tool that became public in April 2017, just one month after Microsoft released a patch […]
Cisco: Crypto-Mining Botnets Could Make $100m Annually
Cyber-criminals are increasingly turning to stealthy crypto-mining malware to generate revenue rather than ransomware, according to a new Cisco Talos report. The security vendor claimed that while ransomware has made its authors healthy sums in the past, it is now very much in the sights of law enforcement and security […]
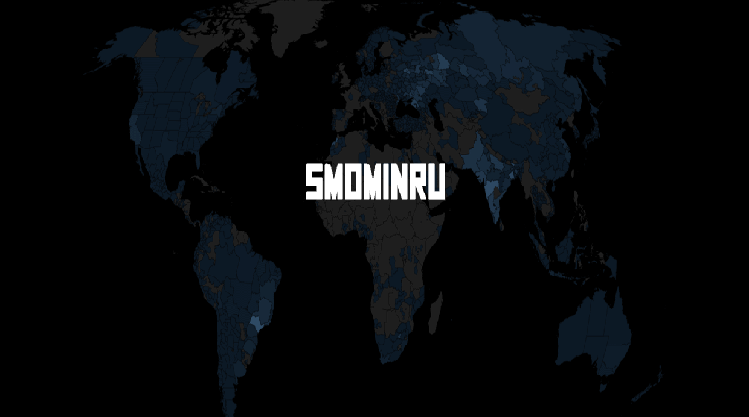
Smominru Botnet Infected Over 500,000 Windows Machines
Over 526,000 Windows computers —mainly Windows servers— have been infected with Monero mining software by a group that operates the biggest such botnet known to date. This group’s operations have been known to security researchers since last year, and various companies have published reports on its activity. Because the botnet […]
Cryptocurrency Mining Malware Infected Over Half-Million PCs Using NSA Exploit
2017 was the year of high profile data breaches and ransomware attacks, but from the beginning of this year, we are noticing a faster-paced shift in the cyber threat landscape, as cryptocurrency-related malware is becoming a popular and profitable choice of cyber criminals. Several cybersecurity firms are reporting of new […]
Alerte au « jackpotting »: les attaques au distributeur de banque
A propos du jackpotting Jackpotting, ou le « braquage 3.0″ ou encore »blackbox », les appellations se diffèrent mais la technique reste la même. Le jackoptting a fait son apparition en Europe et en Amérique en 2015 et a engendré la pertes de 50.000 euros en 2016.Mais ces derniers jours, au Etats Unis, […]
Les arnaques au président font de nouveau des ravages : PME
Alors que l’Office Central pour la Répression de la Grande Délinquance Financière (OCRDGF) avait constaté une baisse de ce type d’arnaques entre l’année 2015 et l’année 2016, il semblerait que ce phénomène revienne en force cette année. Cette hausse n’est pas due à une mauvaise sensibilisation, mais bel et bien […]
Oracle MICROS POS Flaw Affects Over 300,000 Payment Systems
The security issue of POS systems is nothing new. Breaches in point-of-sale payment terminals have already been highlighted in the media. Taking into consideration that this device is connected with personal information, orders and card details, small wonder that it often becomes a hacker’s coveted choice. What matters here is […]
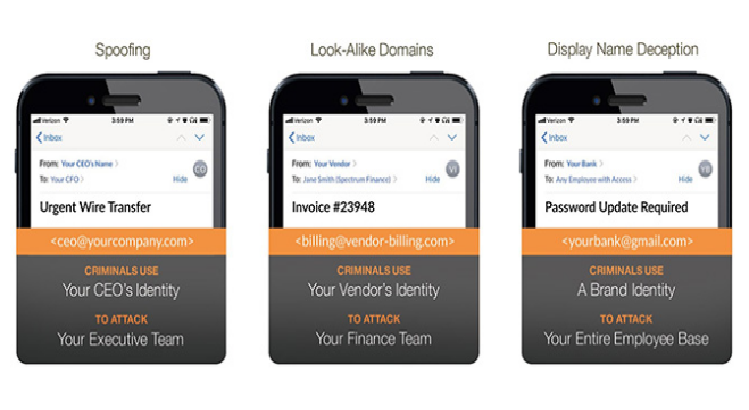
BEC scams surge, cybercriminals target nearly all organizations
96 percent of organizations have received business email compromise (BEC) emails during the second half of 2017, according to Agari. “BEC is a particularly effective attack vector because its lack of payload makes it nearly impossible for conventional email security solutions to detect and prevent,” said Markus Jakobsson, chief scientist, […]
Scarab ransomware: new variant changes tactics
The Scarab ransomware was discovered in June 2017. Since then, several variants have been created and discovered in the wild. The most popular or widespread versions were distributed via the Necurs botnet and initially written in Visual C compiled. However, after unpacking, we’ve found that another variant discovered in December […]
Positive Technologies partners with CriticalBlue to provide integrated protection from web and mobile application attacks
Strategic partnership provides automated defense against malicious bots and scripts for web and mobile applications by combining Approov and PT Application Firewall Positive Technologies and CriticalBlue today announced a strategic partnership to provide an integrated mobile and web application security offering for companies looking to defend against the growing threat […]