Le cryptojacking consiste à utiliser secrètement les ressources de votre dispositif pour miner de la cryptomonnaie. L’idée du cryptojacking est née en mi-septembre lorsque CoinHive a proposé un script pour le minage de cryptomonnaies (monero en l’occurrence). Parmi les sites Web qui l’ont adopté, figure The Pirate Bay, le site […]
Le programme d’installation de Skype vulnérable aux attaques par injection DLL ?
Selon plusieurs sources, le programme d’installation de Skype serait vulnérable aux attaques par injection DLL. Même la toute dernière version 8 serait concernée. Le programme d’installation de Skype se comporte-t-il comme un cheval de Troie en permettant des attaques par injection DLL ? C’est en tout cas ce que semble […]
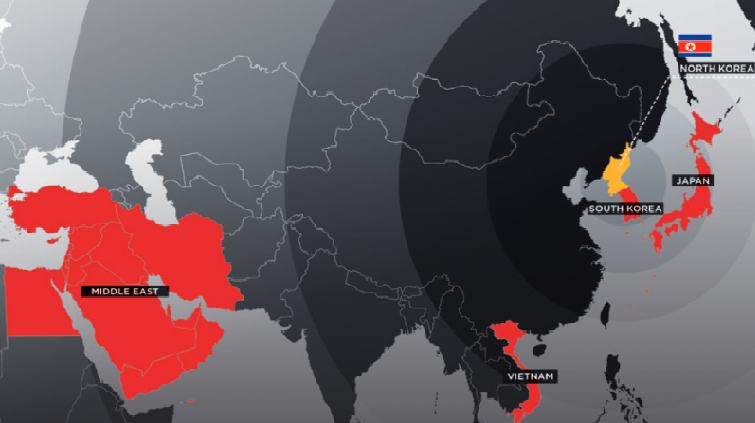
North Korean Hacking Group APT37 Expands Targets
A lesser known hacker group believed to be working on behalf of the North Korean government has been expanding the scope and sophistication of its campaigns, according to a report published on Tuesday by FireEye. The threat actor is tracked by FireEye as APT37 and Reaper, and by other security […]
Amazon AWS Servers Might Soon Be Held for Ransom, Similar to MongoDB
Amazon AWS S3 cloud storage servers might soon fall victims to ransom attacks, similar to how hacker groups held tens of thousands of MongoDB databases for ransom throughout 2017. The statement, made today on social media by infosec expert Kevin Beaumont, is nothing short of a prophecy of things to come, an […]
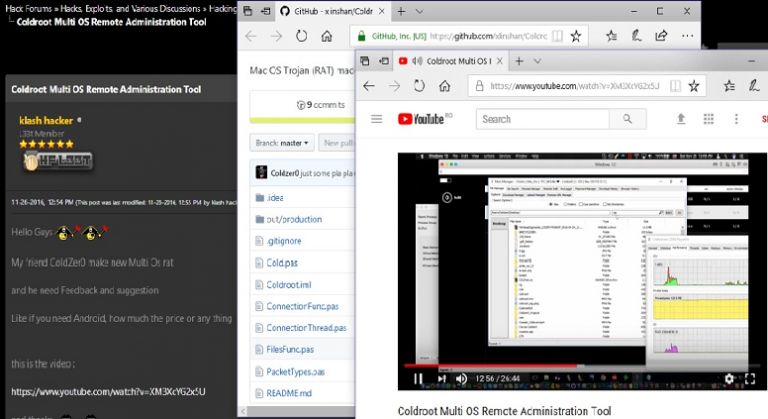
Coldroot RAT Still Undetectable Despite Being Uploaded on GitHub Two Years Ago
Coldroot, a remote access trojan (RAT), is still undetectable by most antivirus engines, despite being uploaded and freely available on GitHub for almost two years. The RAT appears to have been created as a joke, « to Play with Mac users, » and « give Mac it’s rights in this [the RAT] field, » but has […]
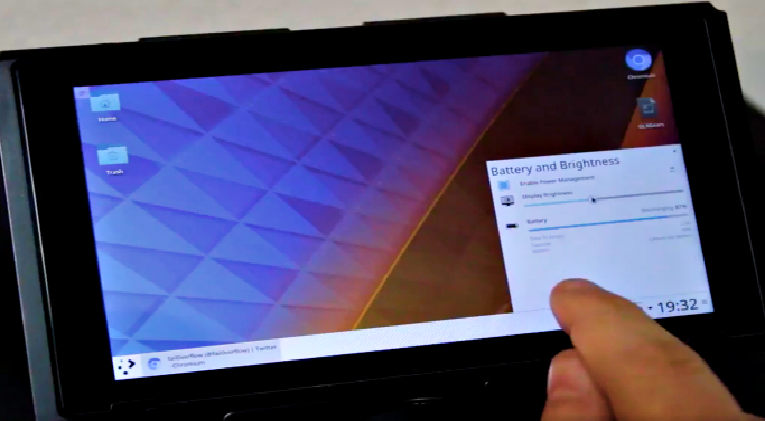
Hackers Exploite Tegra Chipset Flaw to Run Linux OS on Nintendo Switch
The exploit is unpatched putting Nintendo Switch devices at risk. Usually, hackers compromise a gaming console to be able to play pirated versions or cracked copies of their favorite games, which has become quite difficult now, or they want to run the software of their choice. Perhaps this is the […]
Tesla Internal Servers Infected with Cryptocurrency Miner
Hackers have breached Tesla cloud servers used by the company’s engineers and have installed malware that mines the cryptocurrency. The incident took place last year when hackers gained access to Tesla’s Kubernetes server, an open-source application used by large companies to manage API and server infrastructure deployed on cloud hosting providers. Hackers […]
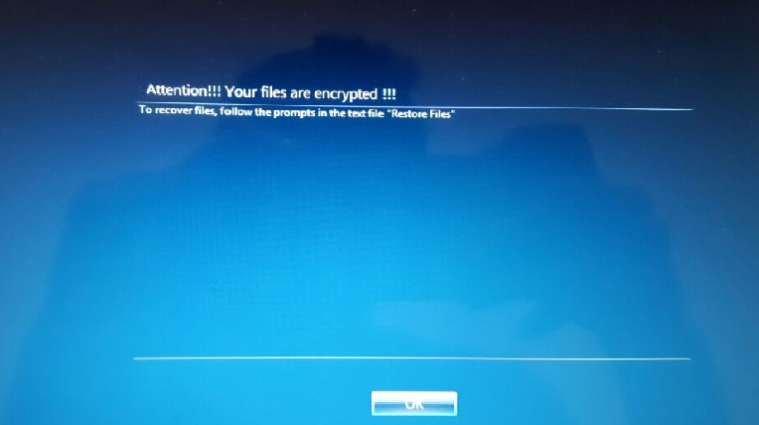
LockCrypt .1BTC Variant Installed Over Hacked Remote Desktop Services
Today a reader sent me info regarding the LockCrypt Ransomware being actively distributed over hacked remote desktop services. This variant, when installed, will encrypt a victim’s files and then append the .1btc extension to encrypted file names. For those not familiar with the LockCrypt Ransomware, AlienVault has a good writeup about an older […]
Triton, le nouveau malware qui s’est rapidement fait connaître
Dans le monde de la cybercriminalité, les attaques se font de plus en plus nombreuses et exceptionnellement impressionnantes. C’est dans cette nouvelle vision des malwares que Triton a vu le jour au mois d’août 2017 et s’est fait remarqué en causant des perturbations opérationnelles importantes dans l’infrastructure d’une gigantesque usine. […]
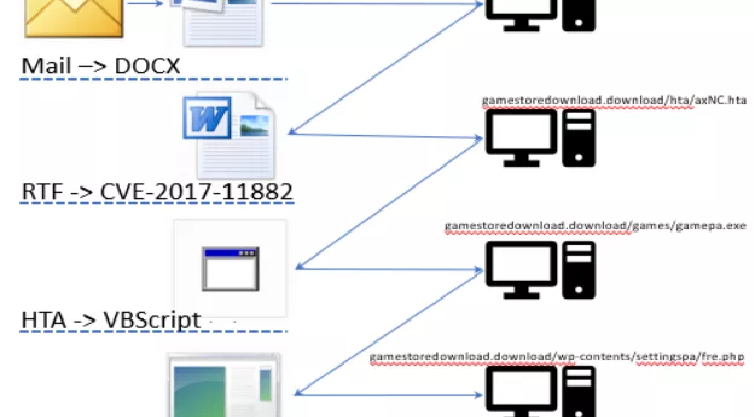
A new multi-stage attack deploys a password stealer without using macros
Security researchers at Trustwave spotted a new malicious campaign that uses a multi-stage attack to deploy a password stealer. Researchers at Trustwave have spotted a new malware-based campaign that uses a multi-stage infection to deploy a password stealer malware. Hackers leverage the infamous Necurs botnet to distribute spam emails delivering Microsoft Office documents […]