Ransomware Takes Georgia’s City of Hinesville Offline An unknown ransomware variant took down the City of Hinesville in late February. Initially, the ransomware attack was reported as an IT incident; however, city officials are now reporting their systems were indeed infected with ransomware on February 20th. The exact ransomware variant […]
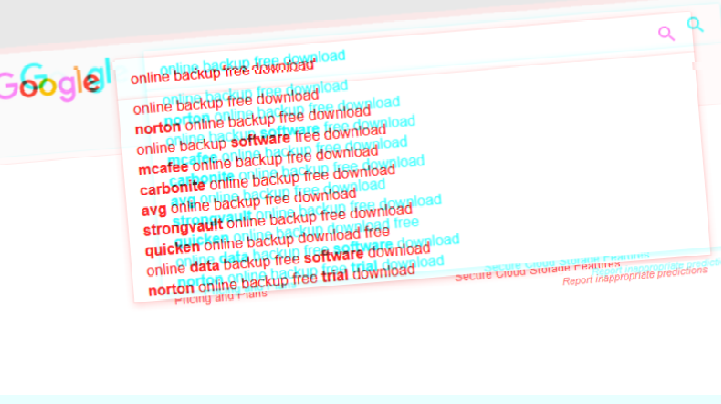
One Every 200 Google Search Suggestions Is Polluted
One of every 200 Google search autocomplete suggestions are poisoned and are used to drive traffic to misleading sites, to malware, or other malicious content, a team of academics from three US universities has discovered. This is one of the most recent types of blackhat search engine optimization (BHSEO) techniques […]
INTEL DETAILS CPU ‘VIRTUAL FENCES’ FIX AS SAFEGUARD AGAINST SPECTRE, MELTDOWN FLAWS
Intel introduced hardware-based protections to its new chips to protect against the Spectre and Meltdown flaws that rocked the silicon industry when the vulnerabilities were made public in early 2018. Spectre and Meltdown, which account for three variants of a side-channel analysis security issue in server and desktop processors, could […]
Preventing Business Email Compromise Requires a Human Touch
Human-powered Intelligence Plays a Critical Role in Defending Against Socially Engineered Attacks The FBI’s Internet Crime Complaint Center (IC3) declared Business Email Compromise (BEC) the “3.1 billion dollar scam” in 2016, an amount which then grew in the span of one year into a “5 billion dollar scam.” Trend Micro […]
Linux Foundation Announces ACRN —Open Source Hypervisor for IoT Devices
The Linux Foundation announced a new project called ACRN (pronounced « acorn ») that will provide generic code for the creation of hypervisors for IoT devices. A hypervisor is computer code for creating and running virtual machines. Project ACRN aims to provide a generic structure for an IoT-specific hypervisor component. The Linux Foundation says it built […]
Prevent bot traffic from ruining Google Analytics
Distil Bot Discovery for Google Analytics is a free offering that will give website owners the ability to understand the impact of bots on their business. The service is provided by Distil Networks, a company specializing in bot detection and mitigation services. How to differentiate a human website visitor from […]
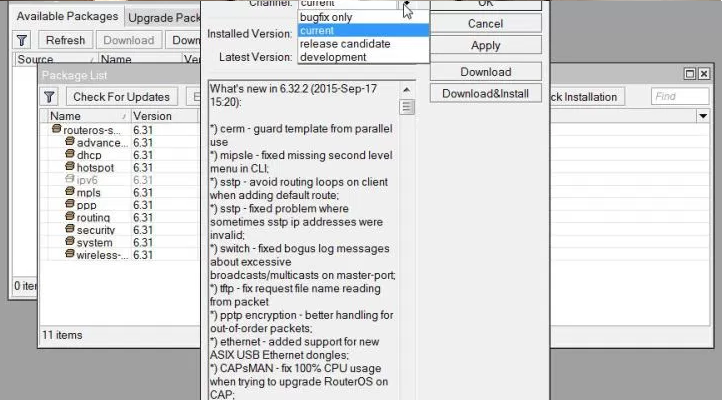
Experts discovered remotely exploitable buffer overflow vulnerability in MikroTik RouterOS
Security experts at Core Security have disclosed the details of a buffer overflow vulnerability that affects MikroTik RouterOS in versions prior to the latest 6.41.3. MikroTik is a Latvian vendor that produce routers used by many telco companies worldwide that run RouterOS Linux-based operating system. The vulnerability, tracked as CVE-2018-7445, could be exploited […]
Russian Hackers Target U.S. Power, Water Facilities
WASHINGTON, DC, March 16, 2018 (ENS) – Russian government hackers have been targeting U.S. government entities as well as organizations in the energy, nuclear, commercial facilities, water, aviation, and critical manufacturing sectors for the past two years, according to a joint Technical Alert issued by the Department of Homeland Security and […]
Fears about the possibility of Russian cyber attacks in Britain
The British intelligence service has warned large power companies in the country of the possibility of Russian cyber attacks after the scandal with the poisoning of former Russian double spy Sergei Scrypal and his daughter Yulia, today reported British media citing a government source. “Communicate with all major infrastructure managers […]
GitHub utilisé par des acteurs malveillants pour héberger un mineur de moneros
Des acteurs malveillants s’appuient sur l’infrastructure de GitHub – une plateforme d’hébergement et de gestion de développement de logiciels – pour propager les malwares dont ils sont les auteurs. L’information est de la firme de sécurité Avast. « Les cybercriminels créent des forks – ce qui sous GitHub veut dire copier […]