A threat actor apparently interested in inter-Korean affairs continues to launch highly targeted attacks using new pieces of malware and decoy documents referencing North Korean political topics.
The cyber espionage group, which experts believe is sponsored by a nation state, has been active for several years, but it managed to stay under the radar until last year, when researchers analyzed two of its main tools, namely SYSCON and KONNI. These pieces of malware had been leveraged in attacks aimed at organizations linked to North Korea.
McAfee’s Advanced Threat Research team recently spotted a new campaign that appears to focus on North Korea, particularly humanitarian aid efforts. The security firm named this operation Honeybee based on the name of the user who created the malicious documents.
Previous research into this group’s activities and a new McAfee report claim the threat actor is likely a Korean speaker. In the past, some even suggested that the attacks may have been launched from South Korea.
However, McAfee told SecurityWeek that South Korea is most likely not behind the attacks. The security firm believes this is the work of an actor interested in inter-Korean affairs, specifically in English-language information.
The attack starts with a spear-phishing email carrying or linking to a malicious document. The document contains a macro designed to drop and execute a new version of the SYSCON backdoor. The malware allows attackers to upload files to a server, and download files to the compromised system and execute them.
The campaign appears to be mainly focused on North Korea, particularly humanitarian aid efforts, with primary targets located in Southeast Asia and the Americas. While many of the targeted entities are located in South Korea, some attacks are also aimed at users in Vietnam, Singapore, Japan, Indonesia, Canada and Argentina.
Some of the malicious documents used to deliver the malware reference North Korea – for example, one is named “International Federation of Red Cross and Red Crescent Societies – DPRK Country Office.”
Other documents, however, rely on a different approach. They display fake Google Docs or Microsoft Office messages that instruct recipients to enable editing and content in order to access the information. If users comply, malicious code is executed and malware is downloaded to their device.
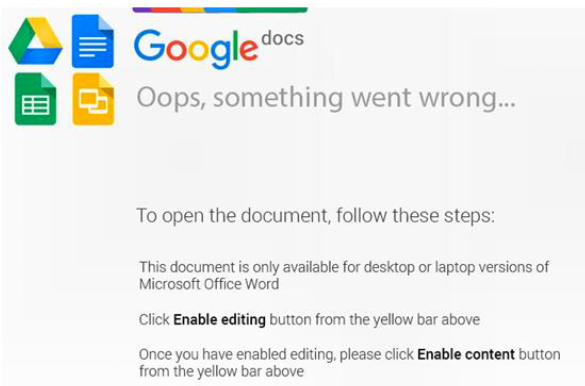
Some of the droppers used in the Honeybee campaign are only disguised as documents. One dropper, tracked by McAfee as MaoCheng, has a document icon, but it’s actually an executable file signed with a stolen Adobe certificate. Once executed, MaoCheng opens a decoy document that instructs users to enable content in order to access the information.
McAfee said the MaoCheng dropper was likely created specifically for the Honeybee campaign and it has only been spotted two times. A new variant of the SYSCON backdoor was first seen by researchers on January 17, but the operation has relied on new implants since at least November 2017. Experts say many components are loosely based on previous versions of SYSCON, but they are unique from a code perspective.
“The attacks used simplistic malware, but the speed to put the campaign into production indicates that this is a well-organized group, hence it has the traits of a nation state level group,” Ryan Sherstobitoff, McAfee Senior Analyst of Major Campaigns, told SecurityWeek.
To read the original article :
https://www.securityweek.com/new-malware-used-attacks-aimed-inter-korean-affairs
