Crooks can abuse Memcache servers to launch insanely massive DDoS attacks using very few computational resources on their end.
These type of DDoS attacks are possible because of the unsecured way Memcache developers have implemented support for the UDP protocol in their product.
Furthermore, to make matters worse, Memcache servers also expose their UDP port to external connections in the default configuration, meaning any Memcache server not behind a firewall can be abused for DDoS attacks right now.
Memcache servers can be abused for reflection DDoS attacks
Cloudflare says it detected several DDoS attacks carried out via exposed Memcached servers in the past few days.
The company explains in a technical report that crooks send small byte-sized requests to Memcached servers on port 11211. Because the UDP protocol wasn’t implemented correctly, instead of responding with a similar or smaller packet, Memcache servers respond with packets that are sometimes thousands of times bigger than the initial request.
Because it’s the UDP protocol, the packet’s origin IP address can be easily spoofed, meaning the attacker can trick the Memcache server into sending this oversized response packets to another IP address —the DDoS attack victim’s IP.
In the DDoS community, this type of DDoS attack is named reflective DDoS or reflection DDoS. The amount of times the response packet size is amplified is the DDoS attack’s « amplification factor. »
Memcache amplification factor can reach a massive 51,200
According to Cloudflare, Memcache-based reflection DDoS attacks can have amplification factors up to 51,200. The company cites recent DDoS attacks launched against its network where attackers sent 15-byte packets and Memcache servers responded with 750kB-packets in return.
This amplification factor can vary, though, depending on the attacker’s ability to craft malicious requests that trick the server into responding with bigger and bigger packets.
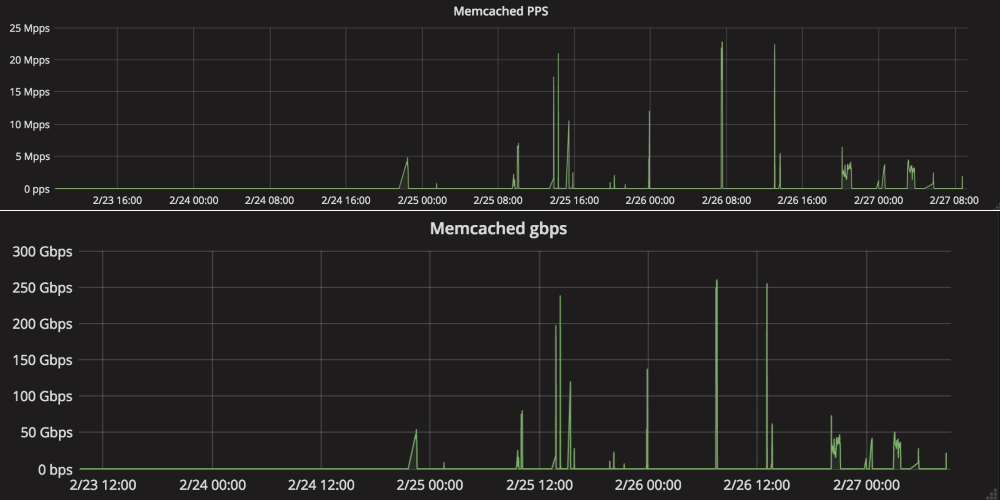
Cloudflare also says the biggest Memcache-based reflection DDoS attack it mitigated this past two days reached a massive size of 260 Gbps (Gigabytes-per-second) and 23 Mpps (Millions-of-packets-per-second).
« The majority of [Memcache response] packets are 1400 bytes in size. Doing the math 23Mpps x 1400 bytes gives 257Gbps of bandwidth, exactly what the chart shows, » said Marek Majkowski, a Cloudflare engineer.
« This is massive for a new amplification vector, » Majkowski said. « But the numbers don’t lie. »
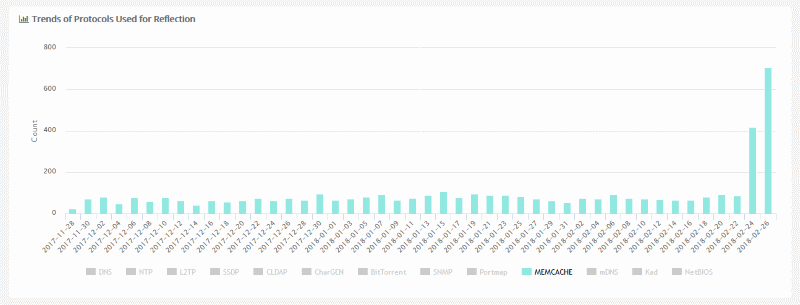
And the numbers truly don’t lie because public statistics provided by Qihoo 360’s Network Security Research Laboratory (Netlab) show a sudden rise in Memcache servers used as a source of reflection DDoS attacks.
Over 93,000 Memcache servers ready for the taking
An amplification factor of 51,200 is enormous. There are other protocols and technologies that can be abused for reflection DDoS attacks, such as DNS, TFTP, LDAP, CLDAP, SNMP, BitTorrent, and others.
Amplification factors usually range from 2 to 10, with the biggest reaching between 50 and 100. Rarely you see a reflection DDoS attack with an amplification factor of over 100, let alone 10,000 or 50,000 as is the case with Memcache.
This wouldn’t be a huge problem if Memcache wouldn’t be a popular web-page caching solution. Bleeping Computer found over 93,000 Memcache servers easily accessible online. The good news is that this number is down from over 134,000 that were available online in 2015.
Security experts are recommending pleading with Memcache server owners to disable their UDP port if they’re not using it and place these servers on private networks, behind firewalls. To get server owners started, Cloudflare has included simple steps on how to disable Memcache’s UDP support in their recent report.
To read the original article:
