Security researchers are reporting that malicious Android apps they have detected and reported to Google the first time, have slipped back into the Play Store after changing their name.
Seven of these apps have been « rediscovered, » said Symantec in a report published yesterday. The company’s experts say the author of the original malicious apps didn’t do anything special, but only changed the app’s names, without making modifications to the code, and re-uploaded the apps on the Play Store from a new developer account under a new name.
Symantec says it detected seven of these re-uploaded apps on the Play Store, which it re-reported to Google’s security team and had them taken down again.
The apps were promoted as emoji keyboard additions, space cleaners, calculators, app lockers, and call recorders. A list of these seven malicious apps is available in the image below, or in this text file.

The security researchers who analyzed these apps said none of these apps worked as promised, but instead focused on tricking the user into granting it admin rights, and then showing ads via Google Mobile Services, or loading scam sites in the user’s browser.
The revelation that malware authors can bypass Google’s Play Store defenses just by changing file and account names is disheartening, to say the least.
Second set of malicious apps discovered
But besides the seven apps re-uploaded to the Play Store, the same Symantec team also discovered another 38 malicious apps, different from the first, which also made it on Google’s official app store.
Experts say these malicious apps were focused on loading a blog’s URL in the phone’s background.
« The URLs lead to various blogs and it is likely the app is being used to increase web traffic to these sites, » Symantec researchers explained the existence of these 38 weird apps.
« So far, the majority of users downloading these apps seem to be located in the U.S., U.K., South Africa, India, Japan, Egypt, Germany, Netherlands, and Sweden, » the company added. « The presence of the apps on the Google Play Store and the seemingly legitimate app names and descriptions allowed the apps to be downloaded onto at least 10,000 devices. »
Symantec says it contacted Google and had this second set of apps removed from the Play Store. The company says it detected both malware campaigns under the same definition of Android.Reputation.1. A list of these 38 malicious apps is available in the image below, or in this text file.
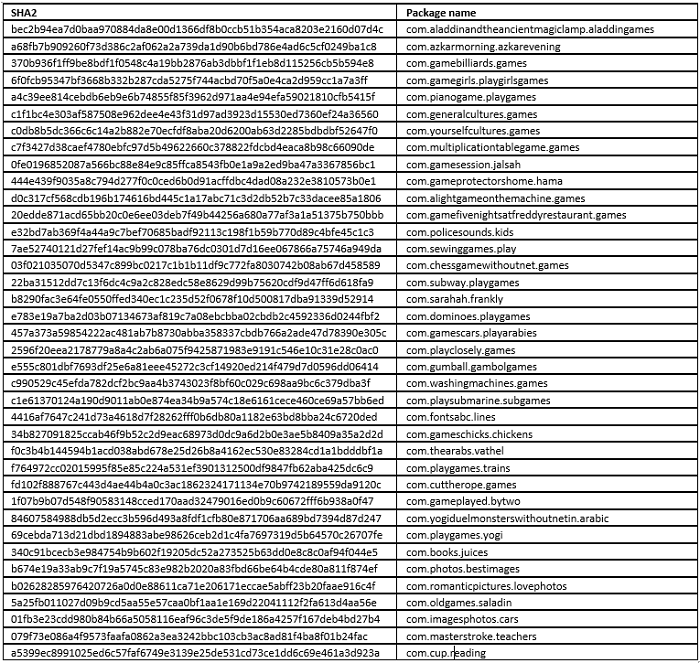
More Android adware
In addition, ESET mobile security researcher Lukas Stefanko has also detected another 15 malicious apps that made it on the Play Store.
« 15 apps with more than 400k+ installs in total found on Google Play, » the expert wrote on Twitter. « These apps can download additional payload and display [and] click on ‘invisible’ ads. Everything is hidden from user’s view. »
Uninstall these apps!
15 apps with more than 400k+ installs in total found on Google Play.
These apps can download additional payload and display + click on « invisible » ads. Everything is hidden from user’s view. pic.twitter.com/Zb5wdnJY6G— Lukas Stefanko (@LukasStefanko) May 10, 2018
This week, Sophos, too, has also published more info on the Guerilla Android adware campaign that made it on the Play Store at the start of the year.
To read the original article:
https://www.bleepingcomputer.com/news/security/malicious-apps-get-back-on-the-play-store-just-by-changing-their-name/
