For the last couple of years, hackers have been exploiting unprotected MongoDBbased servers to steal data and hold the exposed databases for ransom. In order to raise awareness, hackers leaked 36 million records of internal data collected from several vulnerable servers.
The seriousness of the matter can be understood by the fact that in July of 2015 John Matherly of Shodan, the world’s first search engine for the Internet of Things (IoT devices) revealed that there are over 30,000 unprotected MongoDB databases exposed for public access.
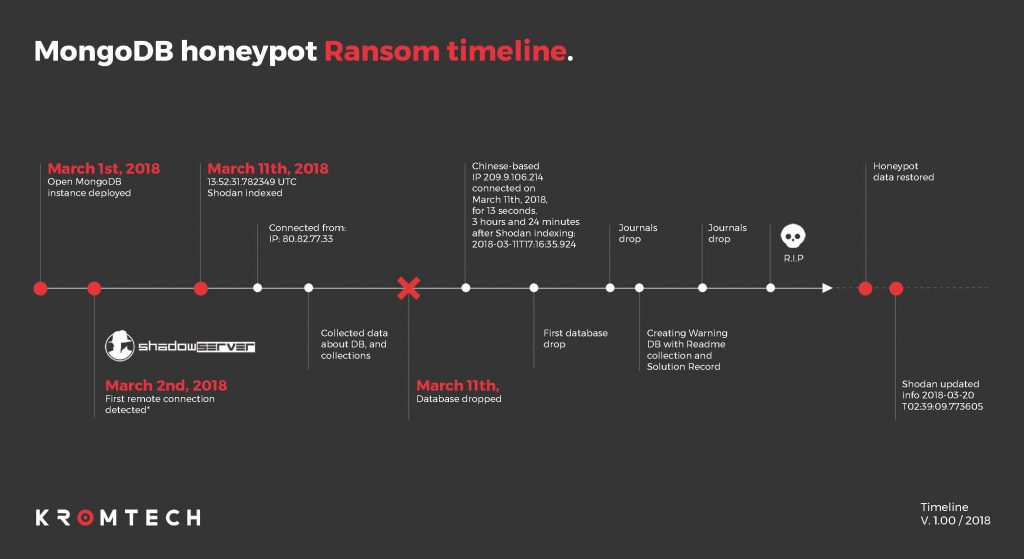
Now, to determine and measure the depth of attacks against MongoDB, the IT security researchers from German firm Kromtech conducted an experiment in which they purposely left a MongoDB database exposed to the public and kept an eye on the incoming connections.
This practice is called as honeypot which is a security mechanism set to detect and counteract attempts at unauthorized use of information systems.
According to Kromtech’s blog post, the honeypot database contained 30GB of fake data. Little did they know, it took only three hours for hackers to identify the database before wiping out its data in just 13 seconds and leaving a ransom note demanding 0.2 Bitcoin.

Here it is noteworthy that in January 2017, hackers held several MongoDB databases for ransom and demanded 0.2 Bitcoin in return. It is unclear if the hackers who took over the honeypot database are part of the same group. However, according to Kromtech’s Chief Communication Officer Bob Diachenko, the attack on their database has been traced back to China.
The researchers are certain that only an automated script can complete such task within 13 seconds.
“The attacker first connects to our database, then drops the databases to delete them, drops the Journals to erase their tracks, creates a database called Warning with Readme collection and the Solution Record, then drops the Journals again to cover their tracks. This was all completed in just thirteen seconds, leading to the conclusion that this was the work of an automated script,” noted Kromtech researchers.
The researchers are advising users to secure their database since exposed MongoDB servers are still at risk. Another important aspect of ransom attacks against MongoDBis that hackers are simply deleting the database therefore even if victim pays them off, their data will never be returned. Therefore, keep a back up of your data and never pay ransom in such cases.
HackRead recommends visiting the blog post by Kromtech researchers for additional technical details on the honeypot bait experiment.
To read the original article:
https://www.hackread.com/hackers-left-ransom-note-after-wipingout-mongodb-in-13-seconds/