Read Time4 Minute, 18 Second
Security experts from Trend Micro have published an interesting report on the Middle East and North African cybercrime underground market, enjoy it!
We explained several times that criminal communities adopt different tactics, techniques, and procedures (TTPs) depending on the location they operate. Experts at Trend Micro have highlighted the differences between the different underground communities, they detailed the Russian underground, the North American one, the Chinese one, the Japanese one and the Brazilian one,
The last report published by Trend Micro is full of interesting information about the Middle East and North African cybercrime underground marketplaces.
The marketplaces in this specific area are full of offers for malware tools and services, but experts warn that shopping these markets can be tricky for outsiders.
In many cases, registrations require a joining fee and the Arabic represents a high entry barrier.
“Our look into these digital souks also revealed how the Middle Eastern and North African underground is not a glass tank like North America’s, but more cautious like the Frenchunderground.” states the report. “Potential customers are barred from window-shopping, for instance, and viewing links or full forum posts requires an account. Registration is a lengthy process that involves paying for one’s membership in bitcoins and getting through the language barrier. English-based forums and sites do exist, but there are certain regional variances.”
Of course in these marketplaces, many actors offer for free also a wide range of hacking tools, malware components, and free instruction manuals. The underground markets in this region are characterized by the confluence of ideology and cybercrime, according to the researchers, there are not profit-driven like other black marketplaces.
Members readily handing out malware tools for free, they tend to cooperate with each other in planning and launching powerful cyber attacks such as
DDoS attacks and malicious operations such as
spam campaigns.“Their underground marketplaces aren’t profit-driven like Russia’s, or China’s. There’s an ironic confluence of ideology and cybercrime in this region, where the “spirit of sharing” and sense of brotherhood are the apparent forces behind the distribution of crimeware. ” reads the report.
“A common practice among its players is to readily hand out codes, malware, and instruction manuals for free. Crypters, typically used to obfuscate malware, as well as SQL injection tools, keyloggers, and basic malware builders, are given away—a reflection of the culture within the regions’ underground scene.”
“The most interesting driver here is the deep permeation of religious influence – from what is sold to how users and sellers interact,” explained Ed Cabrera, chief cybersecurity officer for Trend Micro.
Even if the Middle East and North African cybercrime underground are young it is rapidly increasing, making this ecosystem very dangerous due to future attacks powered by its actors.
The researchers also highlighted another worrisome aspect of the ecosystem, its players are in continuous contact with the threat actors in the Russian underground, in many cases, malware coders and hackers are hired by Russians from the Middle East and North Africa.
The research was conducted in the period between July 2016 and December 2016, the researchers focused their investigation on the kind of merchandise available for sale in these black markets and their price lists.
The vast majority of products and services available in these marketplaces is the same that is available elsewhere, such as malware, hacking services, credit card and credential dumps, and stolen identity information.
“The marketplaces are also rife with do-it-yourself kits that provide the resources that even beginners can use to launch their own cyber criminal business. Developers typically sell their malware either as a single binary, or a bundle of binary and builder; and in some cases, access to a command-and-control (C&C) infrastructure.” continues the report.
Another element that characterized these black market is the low presence of weapons or drugs, visitors looking to buy these items were directed to forums in the North American underground instead.
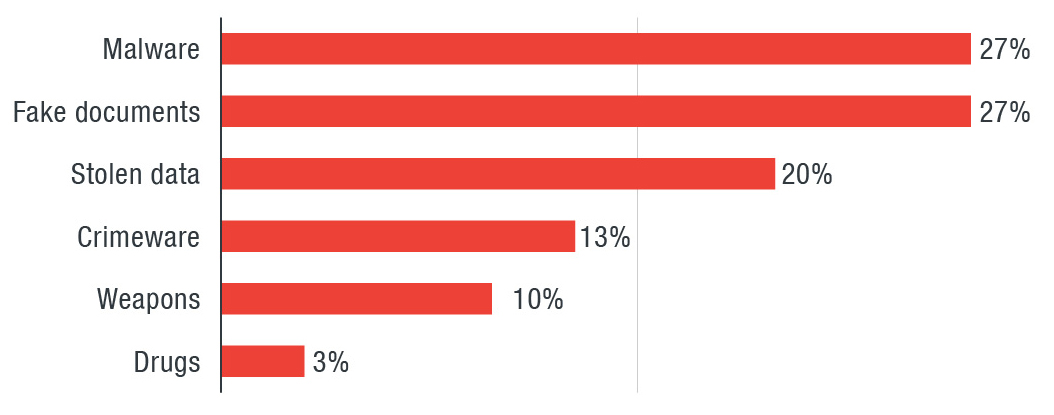
Giving a look at the price list of the underground offering, markets in this area tended to be more expensive than in other regions.
Keylogger goes for $19 in Middle Eastern and North African forums, much more expensive than elsewhere, in the North American underground, it is possible to buy them for between $1 and $4.

The same is for credit card data, as usual, the final price depends on the country origin.

The stolen credentials and online accounts are also much more expensive, these commodities are very attractive for hackers that use them to access e-commerce
accounts and hijack government-owned systems and servers with weak authentication.
The following table shows that the highest price is for PayPal accounts belonging to Israeli users, they go for $50.

Port numbers for Internet-connected SCADA system were available for free in the criminal underworld in this region, while a WannaCry sample was available for just $50.
To read the original articel:
https://www.trendmicro.com/vinfo/us/security/news/cybercrime-and-digital-threats/the-middle-eastern-and-north-african-underground-where-culture-and-cybercrime-meet
http://securityaffairs.co/wordpress/64649/cyber-crime/north-african-cybercrime-underground.html

Happy
0
0 %

Sad
0
0 %

Excited
0
0 %

Sleepy
0
0 %

Angry
0
0 %

Surprise
1
100 %




