Hackers allegedly stole hundreds of reports using a security flaw in an online tool used by the police. In normal circumstances, police are the investigating authority but Gwent County Police in the United Kingdom is in hot water and being investigated for not informing complainers that reports they filed have […]
Hacking
Is the financial sector the most vulnerable to cyber attacks?
The financial services industry is crucial to the health of the UK economy – accounting for more than a million jobs (double that employed in agriculture, for example) and contributing more than £120 billion in gross value added. The country has a healthy trade surplus of £60 billion-plus in this […]
Dangerous CredSSP flaw opens door into corporate servers
A critical vulnerability in the Credential Security Support Provider protocol (CredSSP), introduced in Windows Vista and used in all Windows versions since then, can be exploited by MitM attackers to run code remotely on previously uninfected machines and servers in the attacked network. About CredSSP CredSSP provides single sign-on (SSO) […]
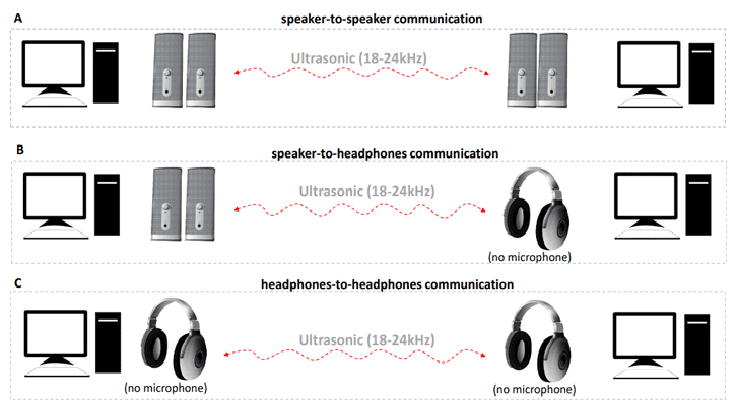
MOSQUITO attack allows to exfiltrates data from Air-Gapped computers via leverage connected speakers
MOSQUITO is new technique devised by a team of researchers at Israel’s Ben Gurion University, led by the expert Mordechai Guri, to exfiltrate data from an air-gapped network. The technique leverage connected speakers (passive speakers, headphones, or earphones) to acquire the sound from surrounding environment by exploiting a specific audio chip feature. Once […]
13 Critical Flaws Discovered in AMD Ryzen and EPYC Processors
Security researchers have discovered 13 critical Spectre/Meltdown-like vulnerabilities throughout AMD’s Ryzen and EPYC lines of processors that could allow attackers to access sensitive data, install persistent malware inside the chip, and gain full access to the compromised systems. All these vulnerabilities lie in the secure part of the AMD’s Zen architecture […]
Microsoft Admits It Incorrectly Upgraded Some Windows 10 Users to v1709
Microsoft admitted last week that it incorrectly updated some Windows 10 users to the latest version of the Windows 10 operating system —version 1709— despite users having specifically paused update operations in their OS settings. The admission came in a knowledge base article updated last week. Not all users of […]
Facebook Flaws Exposed Friend Lists, Payment Card Data
A researcher last year discovered some information disclosure vulnerabilities in Facebook that exposed users’ friend lists and partial payment card information. The social media giant patched one of the flaws within hours. Web security consultant Josip Franjković had been analyzing the Facebook application for Android when he identified a flaw […]
LARGE SCALE TROJAN ATTACKS SEEK CRYPTOCURRENCY
Despite Russia’s growing comfort with the crypto industry, they suffered large-scale attacks from cybercriminals attempting to install crypto mining malware this week. Nearly half a million computers experienced a persistent 12 hour attack. The attack was easily foiled On March 6, a large-scale attack on over 400 thousand PC’s took […]
Malware ‘Cocktails’ Raise Attack Risk
Malware mash-ups hiding in encrypted traffic are boosting attack numbers and increasing the danger to data, according to recent reports. It was good while it lasted. The drop in malware attacks seen in 2016 – from 8.19 billion in 2015 to 7.87 billion – is but a fond memory, as […]
Here’s a List of 29 Different Types of USB Attacks
Researchers from the Ben-Gurion University of the Negev in Israel have identified 29 ways in which attackers could use USB devices to compromise users’ computers. The research team has classified these 29 exploitation methods in four different categories, depending on the way the attack is being carried out. A) By […]