A team of academics has identified an issue with the Zerocoin protocol, along with two security flaws in libzerocoin, the software library used for building actual cryptocurrencies around protocol. Researchers said they found these three issues to affect at least five cryptocurrencies based on Zerocoin, each in varying degrees. The five […]
Hacking
ZLAB MALWARE ANALYSIS REPORT: RANSOMWARE-AS-A-SERVICE PLATFORMS
Security experts at CSE CybSec ZLab malware Lab have conducted an interesting analysis of the principal Ransomware-as-a-Service platforms available on the dark web. Over the years, the diffusion of darknets has created new illegal business models. Along with classic illegal goods such as drugs and payment card data, other services appeared in […]
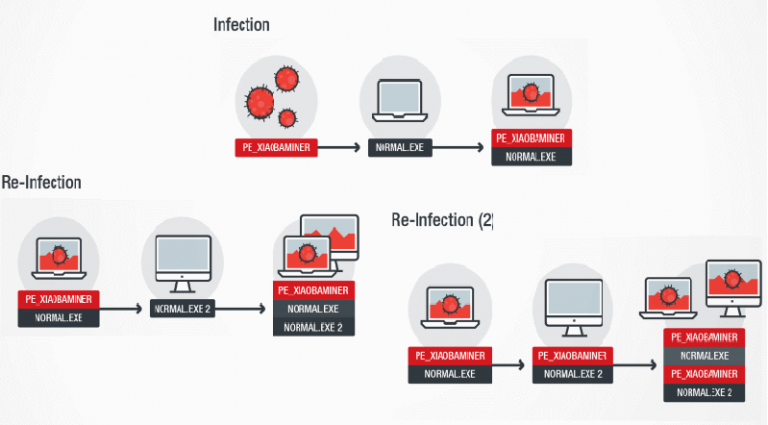
XiaoBa Ransomware Retooled as Coinminer But Manages to Ruin Your Files Anyway
The authors of the XiaoBa ransomware have retooled their malware’s code into a cryptocurrency miner (coinminer). Unfortunately, despite not encrypting files anymore, the XiaoBa coinminer still destroys users’ data thanks to a series of bugs that primarily corrupt a user’s executable files. History of the XiaoBa ransomware The XiaoBa ransomware […]
Oracle Critical Patch Update Advisory – April 2018
Description A Critical Patch Update is a collection of patches for multiple security vulnerabilities. Critical Patch Update patches are usually cumulative, but each advisory describes only the security fixes added since the previous Critical Patch Update advisory. Thus, prior Critical Patch Update advisories should be reviewed for information regarding earlier […]
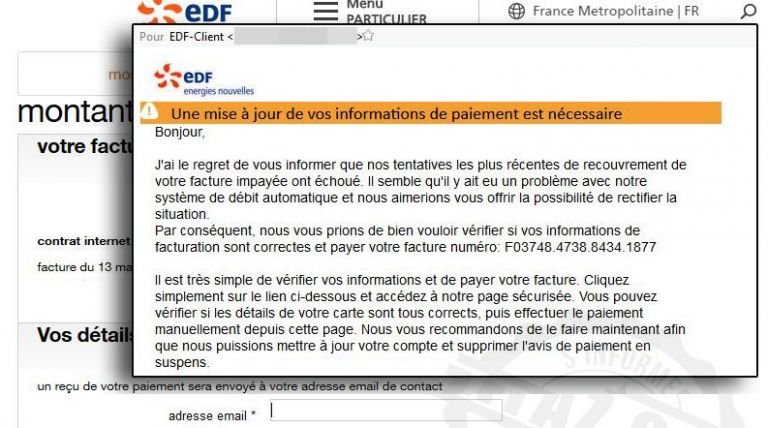
Nouvelle vague de phishing au couleur d’EDF
Fraude EDF : gare au courriel d’un pirate ! Fraude EDF – Des centaines de courriers électroniques aux couleurs d’EDF diffusés par un pirate. Mission de l’escroc, se faire passer pour l’opérateur d’énergie et mettre la main sur vos données bancaires. Nouvelle vague de phishing et d’une fraude EDF. Des hameçonnages […]
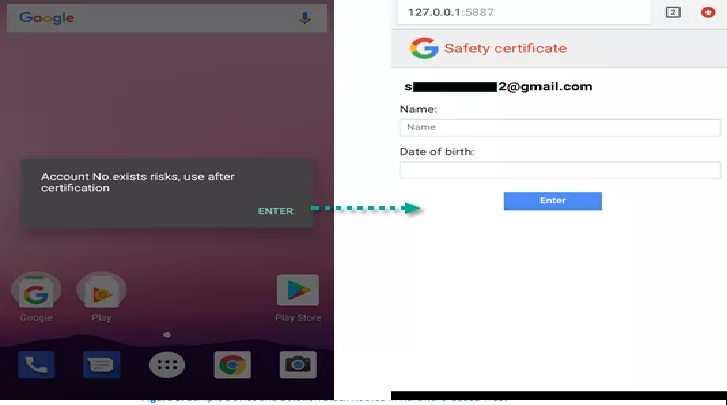
Roaming Mantis Malware Campaign Leverages Hacked Routers to Infect Android Users With Banking Trojan
According to experts at Kaspersky, the Roaming Mantis malware is designed for distribution through a simple, but very efficient trick based on DNS hijacking. According to experts at Kaspersky, the Roaming Mantis malware is designed for distribution through a simple, but very efficient trick based on DNS hijacking. Imagine a […]
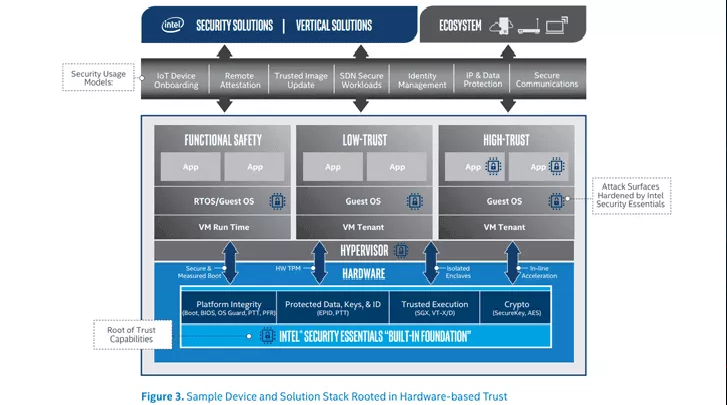
Intel announced the new Threat Detection Technology and Security Essentials
Intel announced a new Threat Detection Technology and a framework of critical root-of-trust hardware security capabilities in its chips. Intel continues to innovate its products, the tech giant announced two new technologies, the Threat Detection Technology (TDT) and Security Essentials. The Threat Detection Technology leverages the silicon-level telemetry and functionality to allow […]
US, UK warn Russians hackers are compromising networking devices worldwide
Russian state-sponsored hackers are targeting network infrastructure devices worldwide, the US Department of Homeland Security (DHS), Federal Bureau of Investigation (FBI), and the United Kingdom’s National Cyber Security Centre (NCSC) have warned on Monday. A joint technical alert published by the organizations says that the targets are “primarily government and […]
Bank web apps are the « most vulnerable » to getting hacked, new research says
Bad news if you’re one of the hundreds of millions of online banking users around the world. The chances are your bank’s website and web apps are horribly insecure. Researchers at security firm Positive Technologies, which has a commercial stake in securing web apps, tested 33 websites and services using its […]
Talos experts found many high severity flaws in Moxa EDR-810 industrial routers
Security experts at Cisco’s Talos group have discovered a total of 17 vulnerabilities in Moxa EDR-810 industrial routers manufactured by Moxa. The Moxa EDR-810 is an integrated industrial multiport router that implements firewall, NAT, VPN and managed Layer 2 switch capabilities. These devices are used in industrial environments to protect systems such […]