American Telecom giant T-Mobile suffering Massive data breach and hackers stolen around 2 million customers sensitive data. T-Mobile is one of the best United States-based wireless network operator that provides wireless voice and data services in the United States. A cybersecurity Team from T-Mobile learned that an unauthorized access on their […]
Hacking
New Form of Mirai Malware Attacking Cross Platform By leveraging Open-Source Project
A newly discovered different form of Mirai malware leveraging Open-Source Project called Aboriginal Linux to infect multiple cross-platforms such as routers, IP cameras, connected devices, and even Android devices. Mirai malware has strong records of infecting poorly managing IoT devices and performing DDOS attacks on various platforms. Mirai Malware(Mirai.linux) initially reported in […]
37,000 Eir Customer’s Personal Data Exposed as their Company Laptop Stolen
Eir data breach exposed more than 37,000 Irish customer’s personal data that includes names, email addresses, phone numbers and eir account numbers. The company confirms none of the financial data relating to the customer was leaked. Eir is the fixed mobile and broadband telecommunications company in Ireland that was founded on […]
AdvisorsBot Malware Attack on Hotels, Restaurants, and Telecommunications Via Weaponized Word Document
Newly discovered AdvisorsBot Malware actively distributing by threat actor TA555 to target Hotels, Restaurants, and Telecommunications departments using a malicious word document. This Malware spreading in the various form via email with a fake content and trick victims to open it infect the victims and steal the sensitive data. Researchers observers that the AdvisorsBot Malware […]
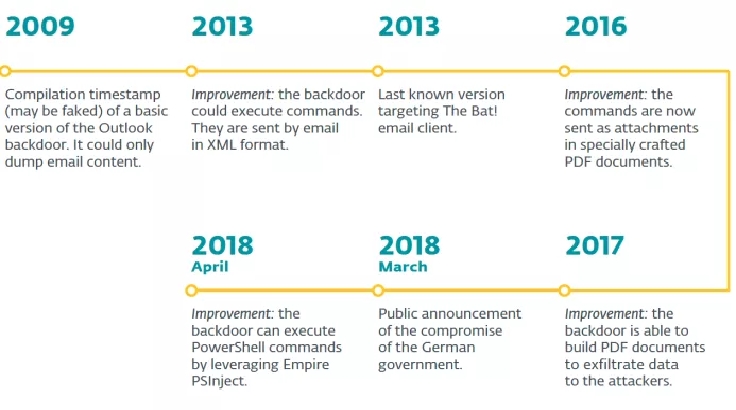
Latest Turla backdoor leverages email PDF attachments as C&C mechanism
Malware researchers from ESET have published a detailed report on the latest variant of the Turla backdoor that leverages email PDF attachments as C&C. Malware researchers from ESET have conducted a new analysis of a backdoor used by the Russia-linked APT Turla in targeted espionage operations. The new analysis revealed a list of […]
Bitdefender spotted Triout, a new powerful Android Spyware Framework
Security researchers from Bitdefender have spotted a new Android spyware framework dubbed Triout that could be used to create malware with extensive surveillance capabilities. Bitdefender researchers have identified a new spyware framework can be used to spy into Android applications, it is tracked as Triout and first appeared in the wild on May 15. The […]
Ryuk Ransomware Attack on various Enterprise Network Around the World & Earned $640,000
Newly spreading Ryuk Ransomware campaign targeting various enterprise network around the globe and encrypting various data in storage, personal computers, and data center. The attacker made over $640,000 from various victims by demanding 15 BTC to 50 BTC in order to retrieve their files and some of the organization from the […]
Beware of Dangerous Android Triout Malware That Records Phone Calls, Videos and Steals Pictures
A new Android malware strain dubbed Triout found bundled with a repackaged app contains surveillance capabilities and ability to hide the presence in the device. Security researchers from Bitdefender identified the new Triout malware that contains extensive surveillance capabilities. The malware appears to be first uploaded to virustotal from Russia […]
2.6 billion records exposed in 2,308 disclosed data breaches in H1
According to a report from cyber threat intelligence firm Risk Based Security some 2.6. billion data records have been exposed in data breached in the first half of 2018. According to a new report titled “Mid-Year 2018 Data Breach QuickView” published by the cyber threat intelligence company Risk Based Security some 2.6. […]
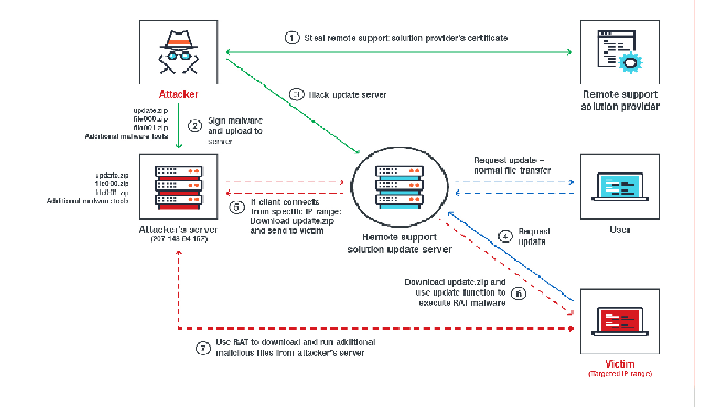
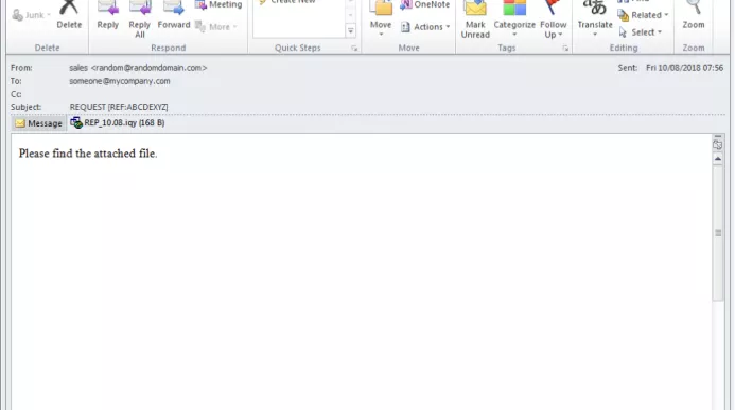
Marap modular downloader opens the doors to further attacks
Overview Proofpoint researchers recently discovered a new downloader malware in a fairly large campaign (millions of messages) primarily targeting financial institutions. The malware, dubbed “Marap” (“param” backwards), is notable for its focused functionality that includes the ability to download other modules and payloads. The modular nature allows actors to add […]