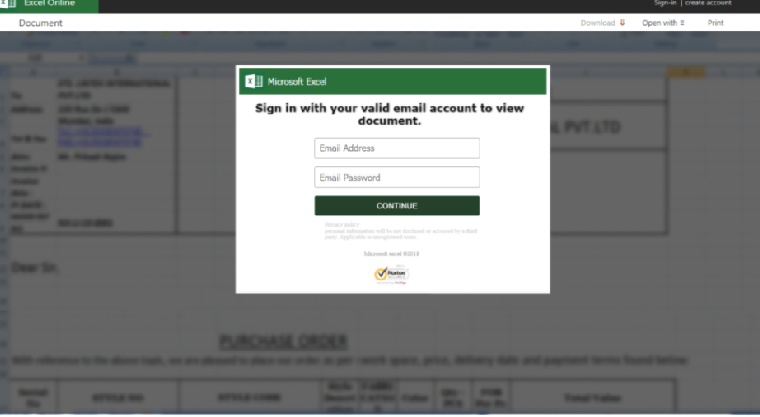
A brand-new approach to harvesting credentials hinges on users’ lack of cloud savvy. A fresh tactic for phishing Office 365 users employs credential-harvesting forms hosted on Azure Blob storage – signed with legitimate Microsoft SSL certificates to lend an air of legitimacy. Azure Blob Storage is a cloud storage solution […]
Hacking
Italian Police Finally Identified 25-Year-old Italian Hacker who have Defaced NASA Websites
After 5 years Italian police identified the hacker who is behind the NASA Websites hack and sixty institutional sites of local authorities. The Hackers almost defaced around 70 websites that belong to Italian and foreign institutional sites along with American spy agencies and 8 NSA owned domainsback in 2013. A 23-year-old […]
New Gallmaker APT group eschews malware in cyber espionage campaigns
A previously unknown cyber espionage group, tracked as Gallmaker, has been targeting entities in the government, military and defense sectors since at least 2017. A new cyber espionage group tracked as Gallmaker appeared in the threat landscape. According to researchers from Symantec, who first spotted the threat actor, the group has launched […]
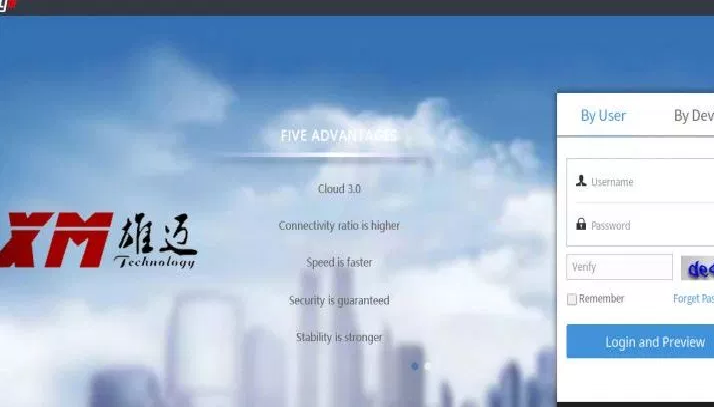
Millions of Xiongmai video surveillance devices can be easily hacked via cloud feature
Millions of Xiongmai video surveillance devices can be easily hacked via cloud feature, a gift for APT groups and cyber crime syndicates Security experts from security firm SEC Consult have identified over 100 companies that buy and re-brand video surveillance equipment (surveillance cameras, digital video recorders (DVRs), and network video recorders […]
Meet GhostDNS: The dangerous malware behind IoT botnet targeting banks
Security researchers at NetLab, a sub-division of the Chinese cybersecurity firm Qihoo 360, have discovered a new, wide-scale, and very active malware campaign that has managed to hijack more than 100,000 home routers between Sept 21 and 27. A majority of routers (almost 88%) are located in Brazil. The malware […]
Apple Releases Security Updates for iOS and iCloud, Fixes Passcode Bypass
Apple has released a new round of security updates for iOS 12 and iCloud that resolve numerous vulnerabilities. For iOS, these updates resolve two passcode bypasses and for iCloud there are numerous, including critical, vulnerabilities that were fixed. Included in this update are also fixes for the charging and WiFi bugs that […]
Microsoft Patches Zero-Day Under Active Attack by APT
A zero-day vulnerability tied to the Window’s Win32k component is under active attack, warns Microsoft. Microsoft has issued a patch for a zero-day bug being actively being exploited in the wild, as part of its Patch Tuesday security bulletin. The vulnerability is an elevation-of-privilege flaw, rated important, affecting the Windows […]
New Ninth-Gen Intel CPUs Shield Against Some Spectre, Meltdown Variants
New Intel Coffee Lake CPUs offer hardware-based protections against some -but not all- Spectre and Meltdown variants. Intel’s new ninth-generation CPUs come packed with hardware-based protections against two variants of the infamous Meltdown and Spectre speculative execution attacks. The ninth-generation desktop Core processors are dubbed Coffee Lake, and became available […]
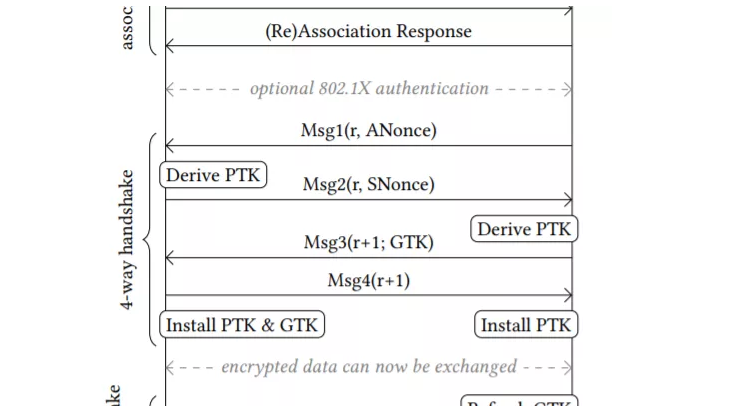
Researchers presented an improved version of the WPA KRACK attack
Security researchers who devised last year the Key Reinstallation Attack, aka KRACK attack, have disclosed new variants of the attack. Security researchers Mathy Vanhoef and Frank Piessens who devised last year the Key Reinstallation Attack against WPA, aka KRACK attack, have disclosed new variants of the attack. Last year, boffins discovered several key […]
Phishing Campaign uses Hijacked Emails to Deliver URSNIF by Replying to Ongoing Threads
While most phishing campaigns are fairly simplistic in nature and easy to spot (they usually involve a legitimate-looking email, often with a malicious attachment or link embedded in the text), a spam campaign we observed in September indicates attackers are angling towards a more sophisticated form of phishing. The campaign […]