The TheHackerGiraffe used the Printer Exploitation Toolkit (PRET) to hijack +50k vulnerable printers to Promote PewDiePie YouTube Channel. An anonymous hacker hijacked over 50,000 internet-connected printers worldwide to print out messages promoting the subscription to the PewDiePie YouTube channel. Felix Arvid Ulf Kjellberg, aka PewDiePie, is a popular Swedish Youtuber, comedian, and video game commentator, formerly best […]
Hacking
New PowerShell-based Backdoor points to MuddyWater
Security researchers at Trend Micro recently discovered PowerShell-based backdoor that resembles a malware used by MuddyWater threat actor. Malware researchers at Trend Micro have discovered a Powershell-based backdoor that is very similar to a malware used by MuddyWater APT group. The first MuddyWater campaign was observed in late 2017, then researchers from Palo Alto Networks […]
U.S Charges Two Iranian Hackers for SamSam Ransomware Attacks
U.S Charges Two Iranian Hackers for SamSam Ransomware Attacks The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and deploying the notorious SamSam ransomware. The alleged hackers, Faramarz Shahi Savandi, 34, and Mohammad Mehdi Shah, 27, have been charged on several counts of computer hacking […]
Dell data breach – Dell forces password reset after the incident
Dell data breach – Dell forces password reset after the incident Dell data breach – IT giant Dell disclosed a data breach, the company confirmed it has detected an intrusion in its systems on November 9th 2018. Attackers were trying to exfiltrate customer data (i.e. names, email addresses, and hashed passwords) […]
Malicious developer distributed tainted version of Event-Stream NodeJS Module to steal Bitcoins
Malicious developer distributed tainted version of Event-Stream NodeJS Module to steal Bitcoins
Chaining 3 zero-days allowed pen testers to hack Apple macOS computers
Dropbox team disclosed three critical zero-day vulnerabilities in Apple macOS, chaining them it is possible to take over a Mac computer. Dropbox team disclosed three critical zero-day vulnerabilities (CVE-2017-13890, CVE-2018-4176, CVE-2018-4175) affecting the Apple macOS operating system, an attacker could chain them to remotely execute arbitrary code on a targeted Mac computer. The attacker […]
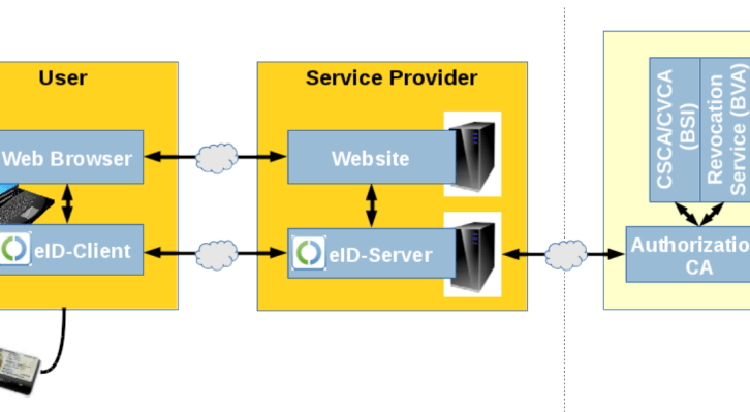
Flaw allowing identity spoofing affects authentication based on German eID cards
Flaw allowing identity spoofing affects authentication based on German eID cards The authentication process via German eID cards with RFID chips is flawed, an attacker could impersonate any other citizen. The nightmare comes true, the authentication process via German eID cards with RFID chips is flawed and a flaw could […]
Experts found first Mirai bot targeting Linux servers via Hadoop YARN flaw
Experts found first Mirai bot targeting Linux servers via Hadoop YARN flaw Security experts from Netscout Asert discovered more than ten Mirai bot variants attempting to exploit a recently disclosed flaw in Hadoop YARN on Intel servers. These Mirai variants are the first one that doesn’t target Internet of Things devices, […]
Sofacy APT group used a new tool in latest attacks, the Cannon.
Sofacy APT group (aka APT28, Pawn Storm, Fancy Bear, Sednit, Tsar Team, and Strontium) has a new weapon in its arsenal dubbed Cannon. The Russia-linked APT group delivers Cannon in a spear-phishing attack that targets government organizations in North America, Europe and in a former USSR state. Experts at Palo Alto Networks spotted a new campaign in late October and early […]
Security bug exposes password of Instagram users
A security bug inside Instagram’s “Download Your Data” tool that could have been exploited to expose password of thousands of users around the world. The feature « Download Your Data » was introduced in April this year after the change in the European Union’s General Data Protection Regulation (GDPR). It allows users […]