Companies in the manufacturing, industrial and infrastructure sectors have been warned to tighten up their security as industrial control systems increasingly come under sophisticated attacks. The warning comes from security specialist Kaspersky, which has warned that computers used in industry have become prime targets for hackers. Kaspersky says that one […]
Hacking
Elaborate scripting-fu used in espionage attack against Saudi Arabia Government entity
We recently came across a campaign targeting a Saudi Arabia Government entity via a malicious Word document which at first reminded us of an attack we had previously described on this blog. In our previous research, we detailed how an information stealer Trojan was deployed via a Word macro, in order […]
Apple’s iOS 11 release prevents backdoor exploit on Wi-Fi chips
Apple’s release of iOS 11 patched an out-of-bounds write vulnerability in Wi-Fi chips that, if exploited, could have allowed attackers within range to execute arbitrary code on the firmware. Designated CVE-2017-11120, the bug was discovered by team researcher Gal Beniamini, and is comparable to the Broadpwnvulnerability found in Broadcom chipsets earlier this year. Following Apple’s Sept. […]
More Mac malware than ever before
Malware isn’t a problem on Macs, is it? You might think so. But that’s not a very safe assumption. Macs have been on malware writers’ radar for a long time. And the trend seems to be increasing. Research from Malwarebytes shows that attacks against macOS are growing. More Mac malware was detected in […]
Devastating phishing attacks dominate 2017
2017 first half: Kaspersky Labs products blocked 51 million phishing attempts; mobile ransomware attacks up 250% percent; Ironscales’ own research estimates 95 percent of successful attacks start with phishing says Eyal Benishti. The recent phishing attack on Breitbart shows how even the simplest attempts can be successful. In this case, […]
RedBoot: A new ransomware that can encrypt and repartition your hard drive-permanently
A newly discovered ransomware called RedBoot is one of the most dangerous yet. Not only does it encrypt files, it also alters the partition table and the master boot record (MBR) to cause what seems to be permanent damage. Early research into RedBoot hasn’t turned up a command and control […]
Google Discloses Critical Wi-Fi Flaws Affecting iOS, Android
Google Project Zero has disclosed the details of two critical remote code execution vulnerabilities affecting the Broadcom Wi-Fi chips found in many Android and iOS devices. The flaws, identified as CVE-2017-11120 and CVE-2017-11121, were patched in Android on September 5 with this month’s security updates and in iOS on September […]
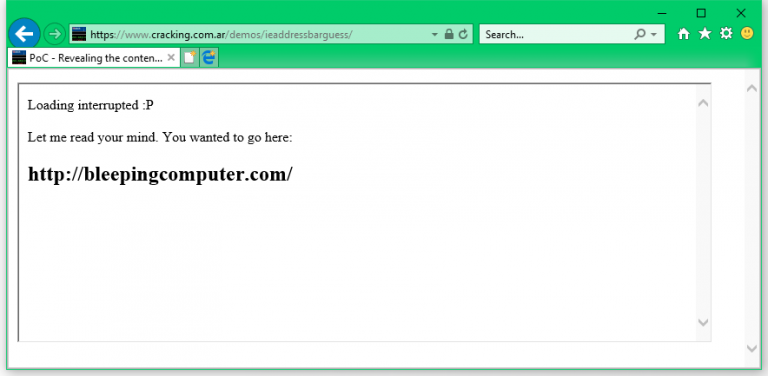
Internet Explorer Bug Leaks What Users Type in the URL Address Bar
Microsoft’s Internet Explorer browser is affected by a serious bug that allows rogue sites to detect what the user is typing in his URL address bar. This includes new URLs where the user might be navigating to, but also search terms that IE automatically handles via a Bing search. Users […]
Cybercrime Costs Each Business $11.7M Per Year
The most expensive attacks are malware infections, which cost global businesses $2.4 million per incident. The average cost of cybercrime in 2017 was $11.7 million per organization, a 23% increase from $9.5 million in 2016 and a 62% increase over the past five years for global businesses. In a new […]
XPCTRA financial malware leaves no stone unturned
A Trojan that has previously been only stealing users’ banking credentials has been modified to do much more than that. This new variant, dubbed XPCTRA, can also steal users credentials for bitcoin cryptocurrency wallet Blockchain.info, online e-payment service PerfectMoney, e-wallet provider Neteller, as well as email credentials. The XPCTRA financial […]