Microsoft has reportedly acquired the popular code repository hosting service GitHub, but at the time of writing there is no news about how much Microsoft paid for the platform. Microsoft has reportedly acquired the popular code repository hosting service GitHub. GitHub was last valued at $2 billion in 2015, but […]
Cybersecurity
Tech giants are all working on new Spectre and Meltdown attacks, so-called variant 3 and variant 4
Yesterday AMD, ARM, IBM, Intel, Microsoft and other major tech firms released updates, mitigations and published security advisories for two new variants of Meltdown and Spectre attacks. Spectre and Meltdown made the headlines again, a few days after the disclosure of a new attack technique that allowed a group of researchers to recover data […]
Bank Of Canada Strengthening Defenses Against Cyber-Criminals
Even though many cyber-attacks inevitably succeed the Bank Of Canada is looking to reduce their risk. They have recovery mechanisms in place to limit as much damage as possible and get the financial system back up and running, as claimed by the central bank on Wednesday. Chief Operating Officer Filipe Dinis, said […]
IBM Bans the Use of Removable Drives to Transfer Data
IBM has allegedly issued a worldwide ban against the the use of removable drives, including Flash, USB, and SD cards, to transfer data. This new policy is being instituted to prevent confidential and sensitive information from being leaked due to misplaced or unsecured storage devices. According to a report by TheRegister, […]
Line Feeds for Everyone! Notepad Now Supports Unix & Mac EOL Characters
If you have ever copied or opened a Unix file in the Windows Notepad, you would have seen that the result is very ugly as all of the text appears as a mess on one line as Notepad does not recognize Linux End of Line (EOL) characters. This is all going […]
Can existing endpoint security controls prevent a significant attack?
Endpoint security solutions are failing to provide adequate protections to address today’s security threats, specifically malware, according to Minerva Labs. A majority of the respondents surveyed indicated a heightened concern of a major malware breach in the coming year and acknowledged that they require more than an AV solution on the […]
Carthage Cyber Arena CCA Edition 2018
CCA regroupe l’élite du monde de la cybersécurité et du Hacking, les responsables de sécurité, les chefs d’entreprises, les représentants de la communauté Internet et les étudiants pour coopérer et résoudre les problèmes de sécurité. CCA couvre les problèmes les plus actuels liés à la sécurité de l’information. L’édition CCA […]
Les meilleures pratiques de sécurité à adopter pour protéger son entreprise
En faisant les gros titres en 2017, les cyberattaques ont fait réaliser aux entreprises l’importance de s’en prémunir. Dans le même temps, elles ont démontré que la simple installation d’un antivirus ne suffit plus face aux menaces les plus récentes. Tribune par José Fernandes, directeur France de Malwarebytes – L’heure est désormais aux […]
Probably you ignore that Facebook also tracks non-users across the web
Facebook explained how it is tracking Non-Users across the Internet and for which purposes it is using their metadata. Facebook is still in the middle of a storm for its conduct and the way it approached the privacy of its users after the Cambridge Analytica case. Now Facebook is under scrutiny after Zuckerberg […]
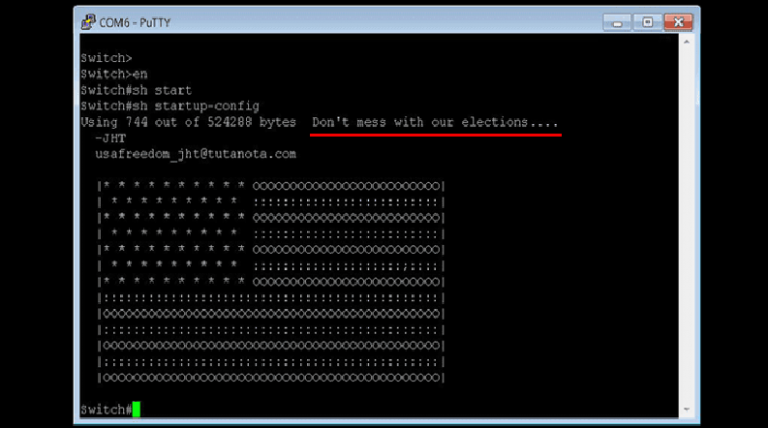
Cisco Smart Install Protocol Misuse
Cisco is aware of a significant increase in Internet scans attempting to detect devices where, after completing setup, the Smart Install feature remains enabled and without proper security controls. This could leave the involved devices susceptible to misuse of the feature. Customers who have not done so are encouraged to […]