You have heard about ride-sharing companies like Uber and Careem becoming victims of large-scale cyber attacks but now a bike sharing company has been hacked after falling for a damaging cyber attack. The computer system responsible for controlling and managing operations of Denmark’s Copenhagen city’s bicycle sharing system “Bycyklen” was hacked over the weekend […]
Haythem Elmir
Office 365 Zero-Day Used in Real-World Phishing Campaigns
A new zero-day vulnerability known as baseStriker allows miscreants to send malicious emails that bypass security systems on Office 365 accounts. Discovered last week, on May 1, 2018, by security researchers from Avanan, baseStriker is a flaw in how Office 365 servers scan incoming emails. The HTML tag at the […]
Adobe Patch Tuesday Is Out With Fixes for Flash Player, Creative Cloud, Connect
Minutes ago, Adobe published this month’s batch of security fixes, part of the company’s regular Patch Tuesday outing. For the month of May 2018, Adobe fixed five vulnerabilities — one in Flash Player, three in the Creative Cloud Desktop application (the app that starts Photoshop, Illustrator, InDesign, and the rest […]
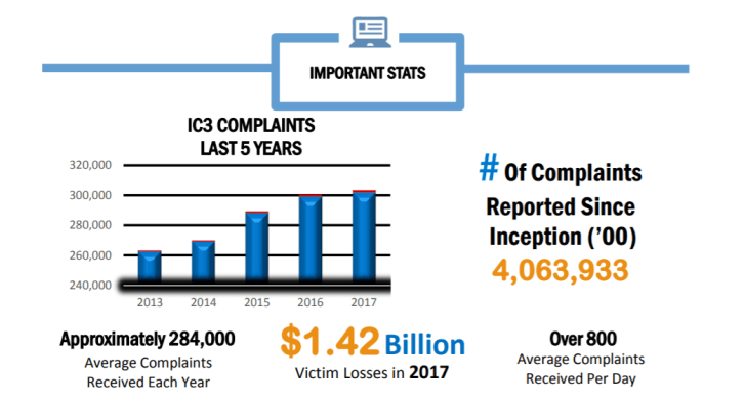
FBI: CYBER-FRAUD LOSSES RISE TO REACH $1.4B
About 301,580 consumers reported cyber-fraud and malware attacks to the FBI’s Internet Crime Complaint Center (IC3) last year – with reported losses exceeding a whopping $1.4 billion. The year’s haul of reports brings the overall total of complaints since the IC3 began recording such things to 4 million. Top threats […]
Line Feeds for Everyone! Notepad Now Supports Unix & Mac EOL Characters
If you have ever copied or opened a Unix file in the Windows Notepad, you would have seen that the result is very ugly as all of the text appears as a mess on one line as Notepad does not recognize Linux End of Line (EOL) characters. This is all going […]
« Hide and Seek » Becomes First IoT Botnet Capable of Surviving Device Reboots
Security researchers have discovered the first IoT botnet malware strain that can survive device reboots and remain on infected devices after the initial compromise. This is a major game-changing moment in the realm of IoT and router malware. Until today, equipment owners could always remove IoT malware from their smart […]
SIERRA WIRELESS PATCHES CRITICAL VULNS IN RANGE OF WIRELESS ROUTERS
Sierra Wireless has patched two critical vulnerabilities for its range of wireless gateways that would leave the enterprise devices helpless to an array of remote threats, including the charms of the Reaper IoT botnet. The more critical of the two (with a 9.4 CVSSv3 Temp Score) is a privilege-escalation bug (CVE-2018-10251), […]
Hackers continue to hack Drupal installs to install backdoors and inject cryptocurrency malware
Recently security experts discovered two critical vulnerabilities in the Drupal CMS (CVE-2018-7600 and CVE-2018-7602), and cybercriminals promptly attempted to exploit them in the wild. The hackers started using the exploits for the above vulnerabilities to compromise drupal installs, mostly cryptocurrency mining. It has been estimated that potentially over one million Drupal websites are vulnerable […]
UPDATED – Critical RCE vulnerability found in over a million GPON Home Routers
Security researchers at VPNMentor conducted a comprehensive assessment on of a number of GPON home routers and discovered a Critical remote code vulnerability that could be exploited to gain full control over them. The researchers have found a way to bypass the authentication to access the GPON home routers (CVE-2018-10561). The experts chained this authentication […]
Reading the 2017 Internet Crime Complaint Center (IC3) report
The FBI’s Internal Crime Complaint Center (IC3) released the FBI 2017 Internet Crime Report, a document that outlines cybercrime trends over the past year. Here we are to analyze the annual FBI 2017 Internet Crime Report, one of the most interesting documents on the crime trends in the last 12 months. The […]