A new zero-day vulnerability known as baseStriker allows miscreants to send malicious emails that bypass security systems on Office 365 accounts.
Discovered last week, on May 1, 2018, by security researchers from Avanan, baseStriker is a flaw in how Office 365 servers scan incoming emails.
The HTML tag at the center of baseStriker
At the center of this vulnerability is the < base > HTML tag. This is a seldom used tab, but developers declare it in the < head > section of an HTML document (web page), and its purpose is to establish a base URL for relative links.
For example, a website might declare a base URL like this:
< base href = "https://www.example.com" / >Once declared, developers can include links to content hosted on the base URL without typing the whole thing, like so:
< img src = "/images/slider/photo-1.png" / >Under the hood, the HTML rendering engine (usually a browser) will merge the base URL with the relative path and come with:
https://www.example.com/images/slider/photo-1.pngOffice 365 doesn’t support the « base » HTML tag
The problem, according to Avanan, is that Office 365’s security systems don’t appear to support base URLs.
An attacker can simply send out a rich-text-formatted email with the following structure and Office 365 won’t be able to scan and detect any malware hosted on the URLs.
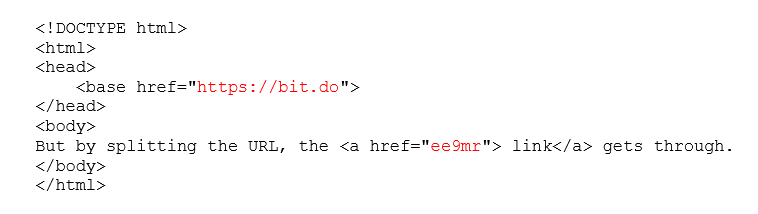
Outlook will render the link correctly, meaning the user will be able to click on it and land on the intended page.
But Office365 security systems like Advanced Threat Protection (ATP) and Safelinks do not merge the base URL and the relative path together before they scan the link —scaning each part separately.
Avanan says it tested various email services but found that only Office 365 to be vulnerable to baseStriker attacks.
baseStriker used in the wild
But baseStriker isn’t just a random vulnerability that researchers found after weeks of pen-testing. Avanan says it discovered baseStriker as part of real-world attacks.
« So far we have only seen hackers using this vulnerability to send phishing attacks, but but it is also capable of distributing ransomware, malware and other malicious content, » Avanan’s Yoav Nathaniel wrote in a report published today.
Nathaniel says Avanan contacted and warned Microsoft of their findings, but the company did not provide feedback on when it would fix the issue. Microsoft is scheduled today to release the Patch Tuesday security updates for the month of May 2018, albeit is unclear if the company had enough time to address baseStriker.
to read the original article:
