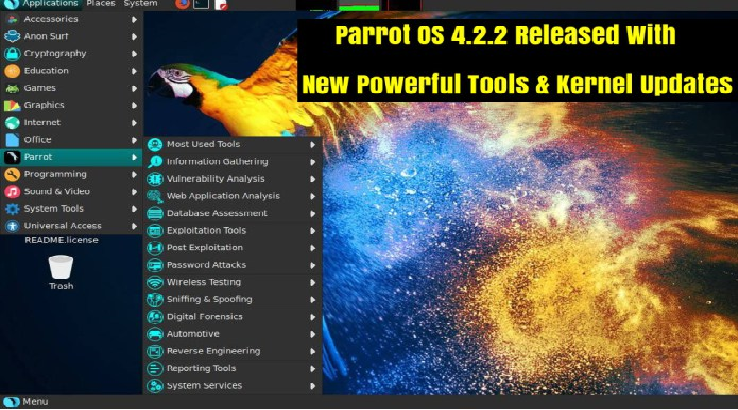
Parrot Security OS 4.2.2 released with a number of new tools, updated for packages and bug fixes that released since the last Parrot Security OS 4.0. This release contains various improvement in kernel and core packages and added the new security tools and updated the existing powerful tools new version. Also, […]
Haythem Elmir
L’armée américaine investit 2 milliards de dollars dans l’intelligence artificielle
« La prochaine étape dans la guerre impliquera des systèmes autonomes de plus en plus efficaces, mais avant que nous puissions permettre à de telles machines de collaborer avec des soldats, elles doivent devenir bien plus intelligentes. » C’est pour cette raison que la Darpa (Defense Advanced Research Projects Agency), l’agence de recherche de l’armée des Etats-Unise, a annoncé vendredi 7 septembre un […]
Hackers Launching GandCrab Ransomware via New Fallout Exploit Kit using Malvertising Campaign
Cybercriminals now using new Fallout Exploit Kit for launching GandCrab Ransomware via Malvertising Campaign that targets many victims around the world. This malvertising campaign mainly affected users in Japan, Korea, the Middle East, Southern Europe, Asia Pacific region and other countries. Along with this Exploit kit, there are additional domains, regions, and […]
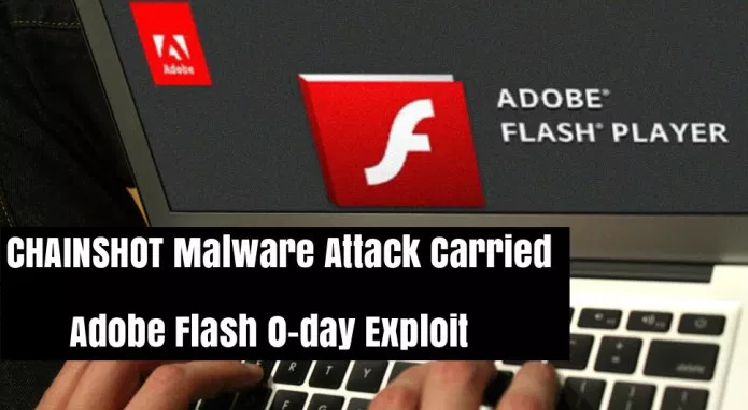
New CHAINSHOT Malware Attack Carried Adobe Flash 0-day Exploit with Weaponized Microsoft Excel Documents
Newly discovered CHAINSHOT Malware attack using Adobe Flash 0-day vulnerability that carried by several Weaponized documents along with the encrypted malware payload. Researchers successfully cracked the 512-bit RSA key and decrypted the payload also the attack contains the several steps that follow each and every steps input. Attackers using the […]
Most Important Cyber Attack Techniques that often used by Hackers
The cyber attack occurs on a daily basis, and these can range from attacks on tech giants to individuals falling foul to the many scams which are present online. Thankfully, there are ways in which people and groups at both ends of the scale can reduce their level of susceptibility […]
British Airways annonce un vol de données qui pourrait concerner 380 000 cartes de paiement
British Airways annonce un vol de données qui pourrait concerner 380 000 cartes de paiement En raison d’une faille informatique, les réservations faites sur le site Internet et sur l’application de la compagnie aérienne entre le 21 août et le 5 septembre ont pu être compromises. La compagnie aérienne britannique British Airways a […]
Mirai botnet:New sophisticated Scanner
Mirai botnet:New sophisticated Scanner New variant of “Mirai” targeting Internet of Things(IoT) devices such as video camera, routers are spreading. The new new ELF Trojan is capable of scanning the network devices or Internet of Things and try to compromise these systems especially those protected with defaults credentials. Samples were served from […]
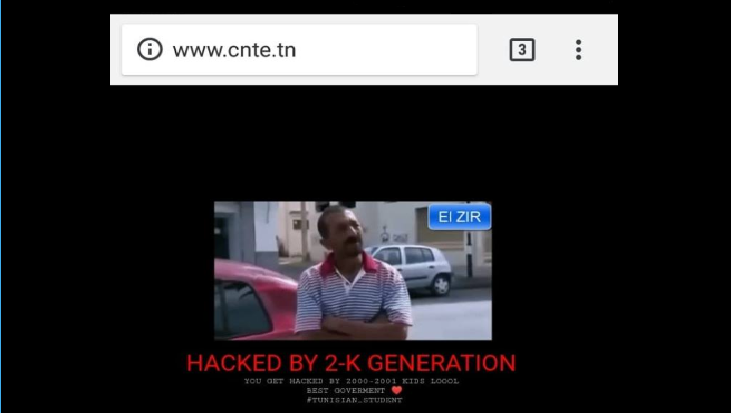
Une attaque de Type Web Defacement cible le site du Centre National des Technologies en Education
Le 30 Aout 2018 ,le site web du Centre National des Technologies en Education a été attaqué par le groupe de pirate anonjoker. I S’AGIT-IL ? L’attaque est de type Web defacement de site internet qui est une forme d’attaque qui vise à remplacer la page principale ou toutes les […]
Russian Hacking Group “Silence” Made Over $800,000 From Attacking Bank ATMs
The world has seen its fair share of cybercriminal gangs. The cyber criminal group “Silence” is rising among the ranks it would seem. Group-IB, a cybersecurity company was able to identify and expose the crimes committed by Silence. The gang’s main targets are banks, especially those in Russia, although attacks […]
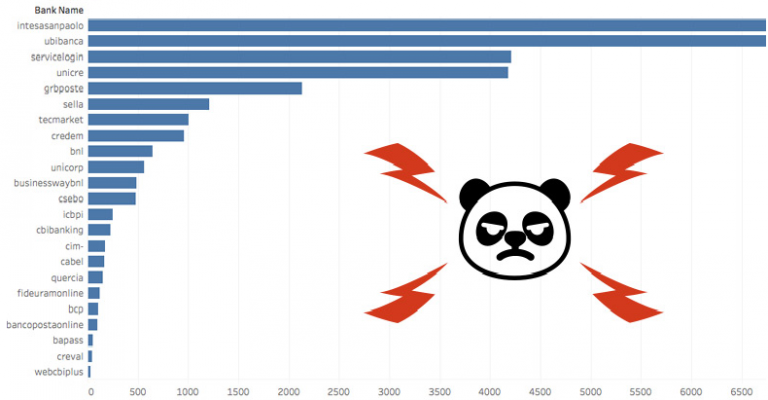
Banks and crypto wallets: unveiling a global malware campaign using Zeus/Panda
For the past weeks our Threat Intelligence team has been following an enxtesive campaign, possibly operated by the same group, targeting a large amount of financial institutions, cyptocurrency wallets and the occasional Google and Apple accounts. The attackers target their victims both with Phishing emails, typo-squatted domains and malicious attachments […]