Recently researchers from FireEye uncovered and blocked a campaign powered by the Chinese APT10 cyber espionage group aimed at Japanese media sector In July, security researchers from FireEye uncovered and blocked a campaign carried out by Chinese APT10 group (aka Menupass, and Stone Panda) aimed at Japanese media sector. Experts noticed the […]
Haythem Elmir
Ransomware Attack Hits Bristol Airport, Flight Display Screens Went Offline
Ransomware attack at the Bristol Airport in UK takes the flight display screens offline. The computers running the flight information display screen’s are affected. The incident likely took place on Friday morning which affected all the flight information display screen and the Airport staffs using Whiteboard to provide flight details. […]
Operator at kayo.moe found a 42M Record Credential Stuffing Data ready to use
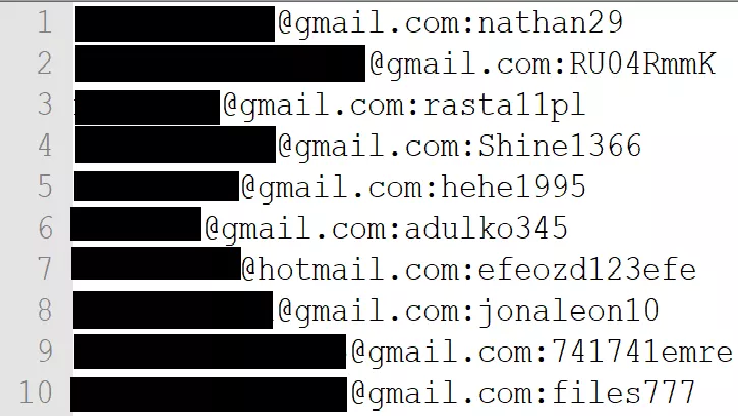
Operator at kayo.moe found a 42M Record Credential Stuffing Data containing email addresses, plain text passwords, and partial credit card info. A huge archive containing email addresses, plain text passwords, and partial credit card data has been found on a free anonymous hosting service, Kayo.moe. The operator of the service shared the file with […]
Veeam Publicly Exposed 445 Million Customers Records Of its Marketing Database
Data Management Company’s misconfigured MongoDB server exposed its marketing database that contains around 445 million its customer records. Veeam, a company that develops backup, disaster recovery and intelligent data management software for virtual, physical and cloud-based infrastructures. Exposed data contains more than 200 gigabytes of customer records, mostly names, email addresses, and in […]
Chinese Cyber Espionage Group APT10 Delivers UPPERCUT Backdoor Via Malicious Word Documents
Chinese cyber espionage group APT10 know for targeting construction and engineering, aerospace, and telecom firms, and governments agencies in United States, Europe, and Japan. With the current campaign, the espionage group targeting Japanese entities through spear phishing emails with password-protected Microsoft Word documents that contain malicious VBA macros. Once the […]
Malware-as-a-Service – New Black Rose Lucy Malware Targets Android Devices With a Special Logic for Xiaomi Phones
Malware-as-a-Service(MaaS) is a practice in which the attackers puts the malware for sale allows anyone with little technical knowledge can launch an attack. Checkpoint research team uncovered the new MaaS product, Black Rose Lucy, developed by Russian speaking team dubbed The Lucy Gang. The MaaS bundle contains a Lucy Loader […]
Flaws in firmware expose almost any modern PC to Cold Boot Attacks
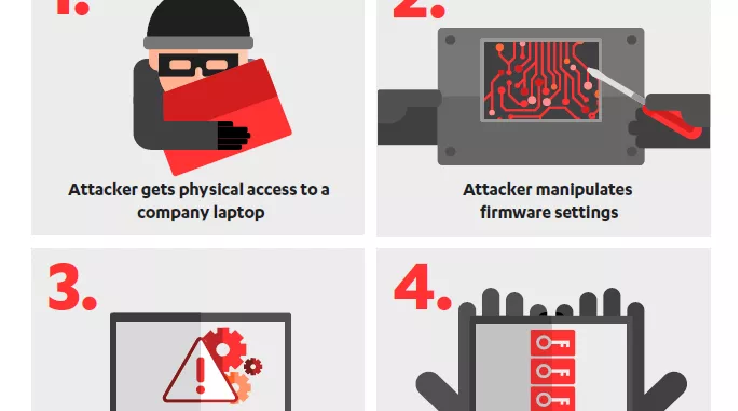
New Firmware Flaws Resurrect Cold Boot Attacks A team of security researchers demonstrated that the firmware running on nearly all modern computers is vulnerable to cold boot attacks. A team of experts from cybersecurity firm F-Secure has discovered security flaws affecting firmware in modern computers that could be exploited by hackers […]
ICS CERT warns of several flaws in Fuji Electric V-Server
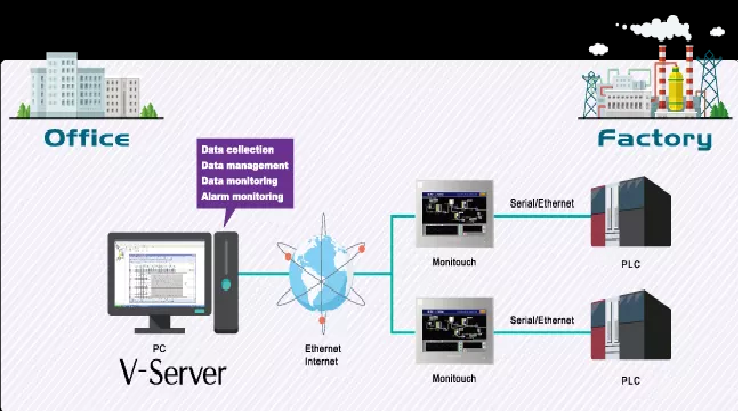
Experts discovered several flaws in Fuji Electric V-Server, a tool that connects PCs within the organizations to Industrial Control Systems (ICS). Experts discovered several vulnerabilities in Fuji Electric V-Server, a tool that connects PCs within the organizations to Industrial Control Systems (ICS) on the corporate network. The ICS-CERT published two advisories to warn […]
Malicious Kodi Add-ons Install Windows & Linux Coin Mining Trojans
ome unofficial repositories for Kodi open-source media player serve a modified add-on that leads to downloading cryptomining malware on Windows and Linux platforms. Security researchers discovered a campaign that infects machines running Kodi via a legitimate add-on that has been altered by cybercriminals looking to mine the Monero cryptocurrency with the resources of Kodi users. The operation […]
Cobalt crime gang is using again CobInt malware in attacks on former soviet states
The Russian Cobalt crime gang was particularly active in the last month, a new report confirms a massive use of the CobInt malware in recent attacks. Security researchers from Proofpoint reported the massive use of the CobInt malware by the Cobalt group in recent attacks. The Cobalt name is based […]