ome unofficial repositories for Kodi open-source media player serve a modified add-on that leads to downloading cryptomining malware on Windows and Linux platforms.
Security researchers discovered a campaign that infects machines running Kodi via a legitimate add-on that has been altered by cybercriminals looking to mine the Monero cryptocurrency with the resources of Kodi users.
The operation appears to have started in December 2017 through ‘script.module.simplejson’ add-on hosted by the now-defunct Bubbles repository. As Bubbles disappeared, Gaia repository started to distribute the malicious add-on.
Criminals take advantage of the update verification system
Security researchers from ESET spotted the campaign in the XvBMC repository, which was recently shut down for copyright infringement, but other repositories are likely to offer the tampered file.
Since Kodi add-ons are available from multiple repositories, and the verification for an update requires only the version number, victims can add the malicious add-on to their Kodi installation when they refresh the repositories that host the modified file.
They say that update routines of unsuspecting owners of other repositories lead to spreading the malicious add-on across the Kodi ecosystem.
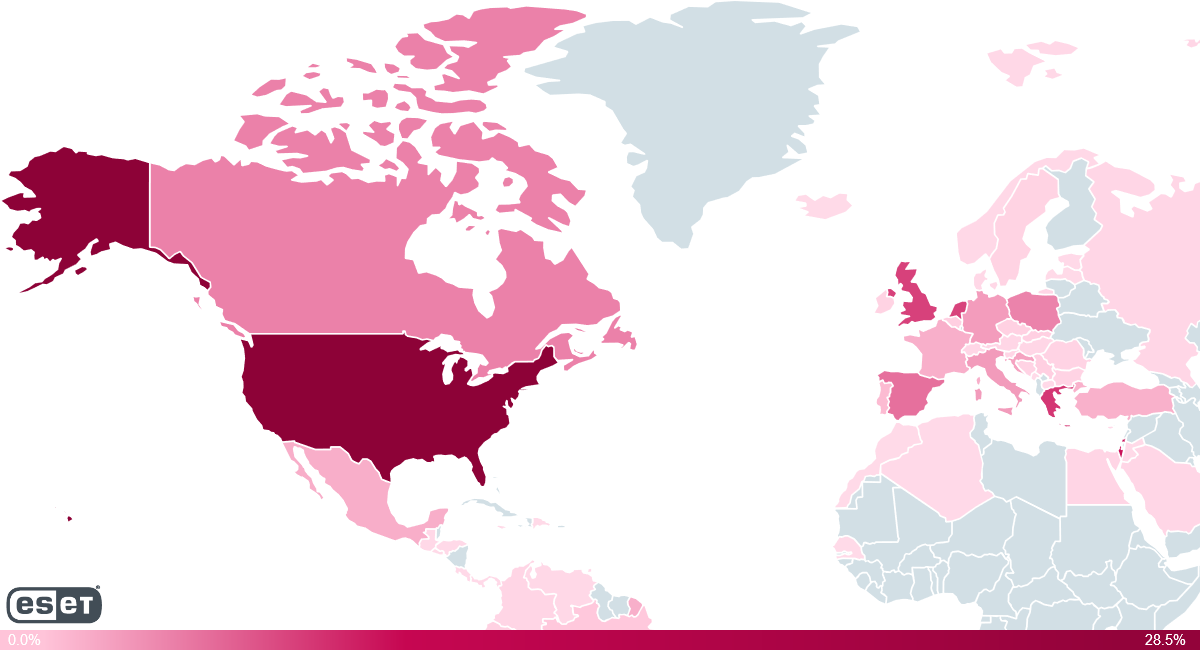
At the moment, the top five affected countries are the United States, Israel, Greece, the United Kingdom and the Netherlands, which is also the home country of XvBMC. These countries are also the ones recording the most traffic for Kodi add-ons.
‘script.module.simplejson’ is the name of a legitimate Kodi add-on, but cybercriminals abused the update system used by Kodi and released the ill-intended variant with a higher version number.
At the moment, ‘script.module.simplejson’ is at version 3.4.0, while the malicious repositories serve version 3.4.1. As the repository had a higher version, Kodi users would automatically auto-update and install the malicious version.
Infection rolls out in stages
ESET’s analysis shows that the threat actor modified the metadata of the original add-on to instruct Kodi to download an add-on called ‘script.module.python.requests’ at version 2.16.0 or above.
The newly downloaded add-on contains Python code that funnels in and executes the cryptominer. Once the malware successfully installed, the Python string that brought it in gets deleted.
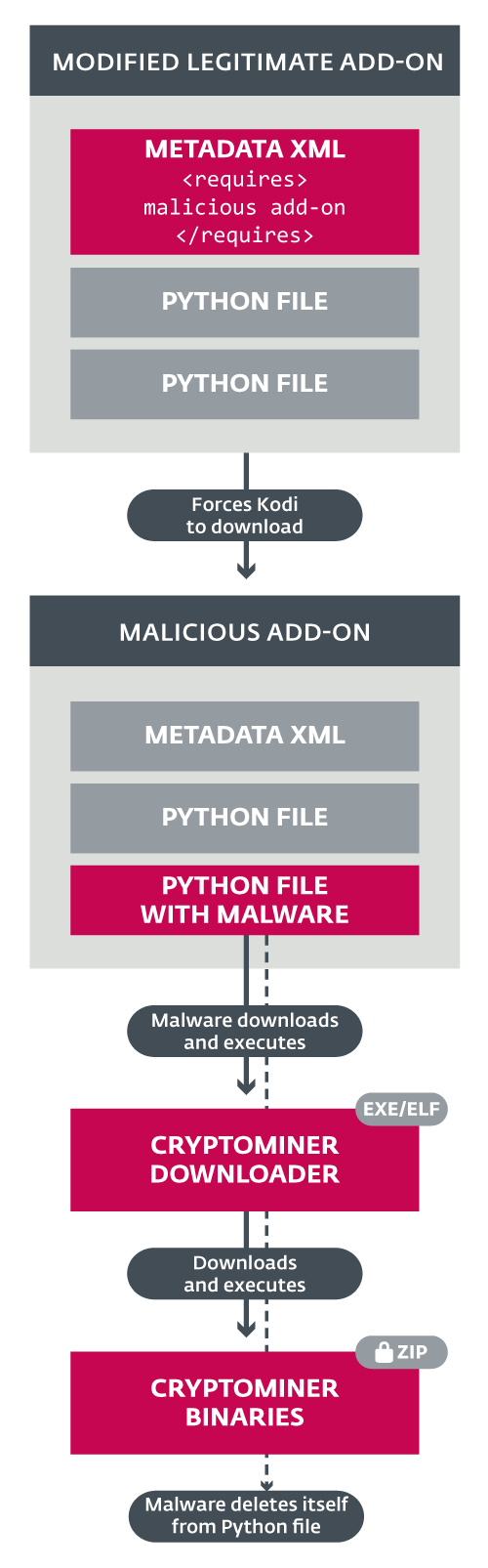
« The code is clearly written by someone with a good knowledge of Kodi and its add-on architecture. The script detects which OS it is running on (only Windows and Linux are supported, Android and macOS ignored), connects to its C&C server, and downloads and executes an OS-appropriate binary downloader module, » the researchers note.
The infection can happen whenever users point Kodi to check a compromised repository URL for add-on updates or when they install a ready-made build of the media player that already contains the URL or the modified add-on itself.
ESET reckons that users that installed used a third-party repository with Kodi there is a chance of compromise.
To read the original article: