A ransomware dubbed as DoubleLocker has infected Android devices by changing the security PIN of the device and encrypting all the data stored. Researchers from cybersecurity firm ESET have discovered the Double Locker ransomware, that is a two-step ransomware which adopts a dual-locking approach. According to researchers, the ransomware is […]
Haythem Elmir
The Matrix Ransomware has risen again!
Security researcher (Jérôme Segura) from Malwarebytes has found that Matrix Ransomware has risen again and it is now being distributed through the RIG exploit kit. The Matrix Ransomware was first spotted in 2016 by Palo Alto Networks researchers, since then the malware had slowly faded until these days. The Matrix […]
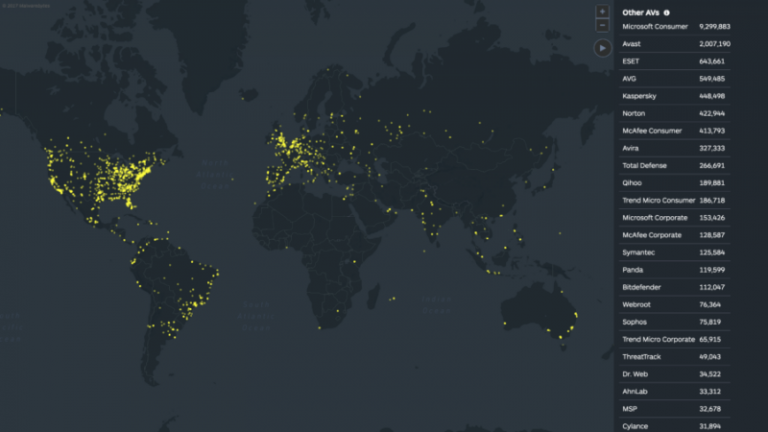
Traditional AV solutions shown ineffective in real-time global heat map
It’s no secret that antivirus technology (AV) has faced increased scrutiny in the tech industry for quite some time. With signature-based detection methods, traditional AV solutions are simply weak against unknown malware and other malicious content. Meanwhile, consumers and businesses continue to trust AV solutions to protect their devices. So, how ineffective […]
ELECTIONS IN KYRGYZSTAN 2017 – EXPOSING SAMARA, A FRAUDULENT VOTER MANAGEMENT SYSTEM
EXECUTIVE SUMMARY One day before the presidential elections in Kyrgyzstan (15 Oct 2017), an activist with the nick name “suppermario12” leaked a video and forensic information about a fraudulent “voter management system” (also known as samara.kg) to be used to influence the elections. Qurium together with the editors of Kloop.kg, […]
Digging the Middle East and North African cybercrime underground market
Security experts from Trend Micro have published an interesting report on the Middle East and North African cybercrime underground market, enjoy it! We explained several times that criminal communities adopt different tactics, techniques, and procedures (TTPs) depending on the location they operate. Experts at Trend Micro have highlighted the differences between […]
A Massive New Internet of Things Bot Is Growing, and No One Knows What It Will Do
There’s something transfixing about the swirling animations of hurricanes gathering strength. Even for those of us who know nothing about weather science, a graphic from the National Hurricane Center can quickly convey a strong sense of impending doom: something big and dangerous is coming and there’s nothing any of us […]
«Bad Rabbit» : Le nouveau ransomware qui rappelle de mauvais souvenirs
« Ransomware BadRabbit : Plus de peur que de mal », « Le ransomware Bad Rabbit crée le désordre en Russie et Ukraine », « Bad Rabbit : ce que l’on sait de la dernière attaque au ransomware », « فايروس الفدية الجديد Bad Rabbit يجتاح العالم » Des titres effrayants lus sur differents sites, réseaux sociaux et média […]
La gestion des risques, sécruité pour les PME
Vos entreprises, activités industrielles et commerciales évoluent dans un écosystème en mouvement fait de nombreux risques. Ces derniers sont internes et externes, matériels ou immatériels. L’exposition et la vulnérabilité face aux risques sont souvent complexes à identifier et à maîtriser. Mais ce qui clair, c’est qu’une mauvaise anticipation des risques mettra en difficulté votre […]
Développement sécurisé: Comment maitriser le risque?
À l’origine des failles de sécurité, il y a le plus souvent, une erreur humaine. Et les développeurs sont (à quelques rares exceptions prêtes ) des humains. Pourtant il existe quelques principes de base notamment recommandée par l’OWASP qui permettent de produire du code à minima sécurisé. Mais peu de […]
Kaspersky: Hackers used backdoored MS Office key-gen to steal NSA exploits
According to Kaspersky, the PC was hacked after the NSA employee installed a backdoored key generator for a pirated copy of Microsoft Office. More details emerge from the story of the hack of the Kaspersky antivirus that allowed Russian intelligence to stole secret exploits from the personal PC of the NSA staffer. The PC […]