In July 2018, US-CERT raised an alert regarding the Emotet banking trojan, which is also being used to distribute a secondary malware known as “Trickbot”. This alert provided recommendations on how businesses can mitigate their exposure to the Trojan. Unfortunately, it looks like criminals are also reading the US-CERT’s warnings as they have adopted new techniques to bypass these recommendations.
Circa 2014, Emotet was first observed as a banking trojan and over time it has evolved to become a highly effective delivery system for other malware. Today, Emotet assumes numerous roles; it acts as a information stealer, malspammer and dropper. Its ability to spread itself via email, maintain a persistent state, and propagate laterally through networks, while using built-in evasion techniques that elude blue teams, has awarded it good reason for defensive teams to be concerned.
Emotet’s ability to spread through emails is one of its significant strengths. After Emotet has infected a machine it will communicate with a command and control (C2) server. The C2 responds by supplying instructions containing a list of recipients to include in a malspam campaign, the content of the email to send, and an email address to spoof as the sender. Emotet then utilises the built-in mail module to begin its malspam phase.
Spoofing an email is far too common and is essentially the act of masquerading as a different sender. This is routinely observed in phishing campaigns and of great concern as a report from Cisco Talosindicates that more than 85% of all emails are illegitimate.
It is therefore unsurprising the US-CERT has supplied recommendations to reduce the impact of receiving malicious mail.
One of the US Government recommendations is to use « Domain-based message authentication, Reporting and Conformance (DMARC) », a mechanism used to assess if an email is genuine. DMARC relies on two technologies; « Sender Policy Framework » (SPF) and « Domainkeys Identified Mail » (DKIM). Either one can be used individually or together.
When using DKIM, the header of a sent email contains instructions and a DKIM public key certificate. When the recipient’s mail server receives the DKIM marked email, the server contacts the sender domain and follows the instructions from within the email header. The instructions enable the discovery of the unique key found within the _domainkeys.DOMAIN address, which is used to confirm the sender is authorised to distribute emails for that domain.
Unfortunately, threat actors have discovered a mechanism to circumvent DMARC controls by using the technique known as domain hijacking. Domain hijacking is an attack with the intention to control an existing domain name, redirecting traffic once destined for a legitimate server to a new malicious destination. This attack fools both human and technology elements that may have once whitelisted the domain.
There are multiple methods that can be used to perform a domain hijack, but in the case of the « Trickbot–Emotet » campaign, hijacked domains were observed with newly created subdomains called _domainkey. This subdomain is an essential part of DKIM protocol and it is almost certain the attackers were trying to circumvent DMARC controls. From this we can learn two things; DMARC was working to reduce the impact of spoofed mail and the attackers knew it.
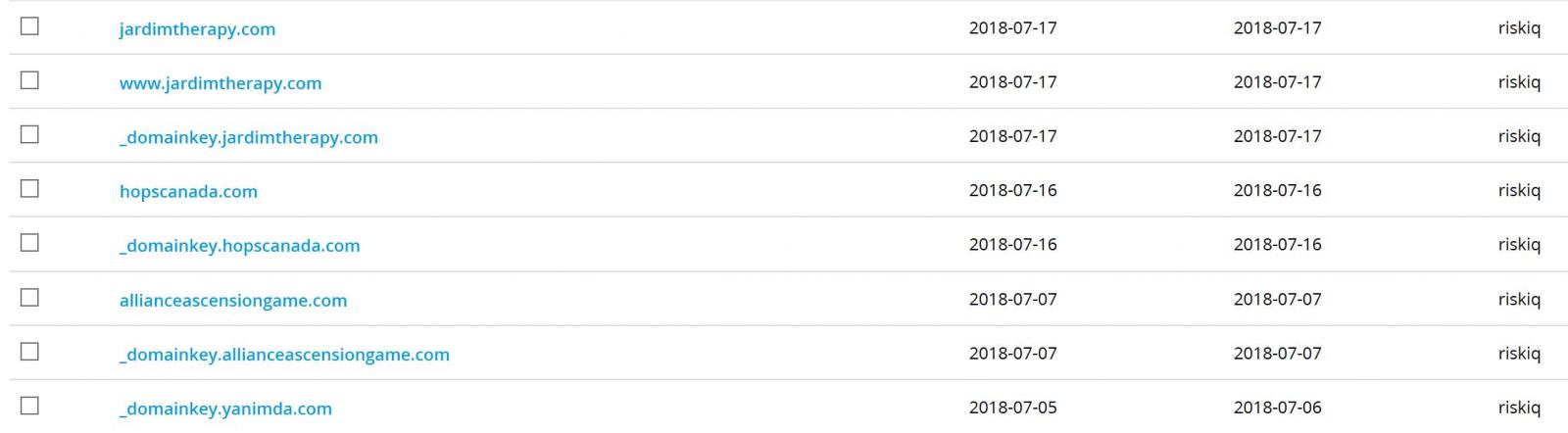
The combination of domain hijacking, DKIM, and Emotet’s malspam module provides attackers with a dynamic distribution method that changes too fast for many organisations to react to and costs the attacker nothing.
Unfortunately, nothing changes for those whom adopt DMARC. The reality is, DMARC is a good control and significantly reduces spoofed emails. It may have its draw backs by filtering out mail from organisations yet to adopt the technology, but it is a great step in the direction to overcome the aging problem that is spam and phishing.
To read the original article:
