Cisco published on Wednesday 30 security advisories on vulnerabilities identified in its products. Half of them are for high and critical severity bugs.
Only three alerts refer to security problems with critical impact; among them is the recently disclosed remote code execution vulnerability in Apache Struts, for which several proof-of-concept exploits exist.
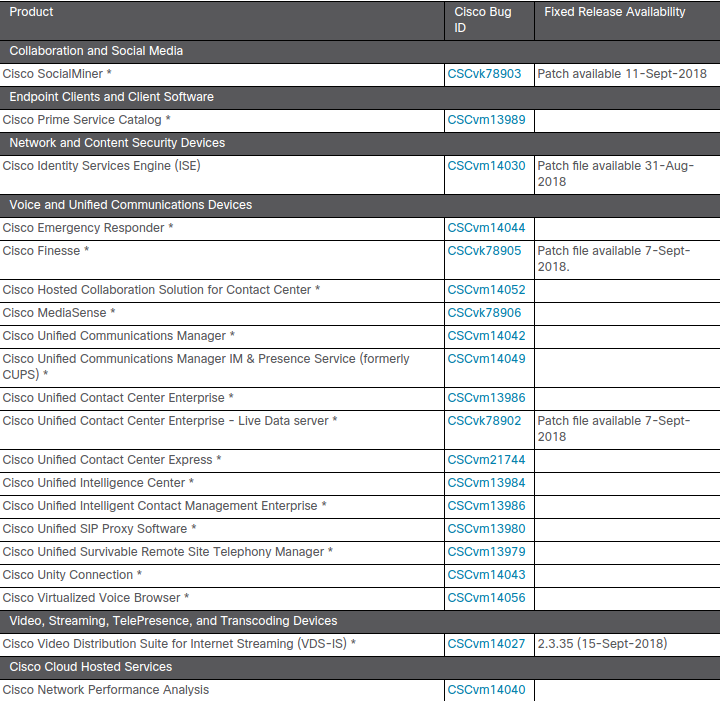
Cisco notes that not all of its products that include an affected Struts library are vulnerable because of the way they use the library.
Only one Cisco product affected by this vulnerability received a patch, the others awaiting an update in the coming weeks or pending schedule for a fixed software release.
Another critical vulnerability is present in Cisco Umbrella API that could « allow an authenticated, remote attacker to view and modify data across their organization and other organizations, » the advisory informs.
Reported by Critical Start’s Section 8 threat intelligence and security research team, the issue is fixable only through a software update.
The Umbrella Enterprise Roaming Client and the Enterprise Roaming Module are also affected by two additional privilege escalation vulnerabilities (CVE-2018-0437 and CVE-2018-0438), with a high severity impact.
Network defenses affected by buffer overflow bug
The third critical bug on Cisco’s list affects the RV-series firewalls and routers, specifically RV110W Wireless-N VPN Firewall, RV130W Wireless-N Multifunction VPN Router, and the RV215W Wireless-N VPN Router.
The vulnerability, now identified as CVE-2018-0423, is a buffer overflow in the management interface that could cause a denial-of-service condition or allow execution of arbitrary code.
« The vulnerability is due to improper boundary restrictions on user-supplied input in the Guest user feature of the web-based management interface. An attacker could exploit this vulnerability by sending malicious requests to a targeted device, triggering a buffer overflow condition, » the advisory explains.
The two routers and the firewall are also vulnerable to directory traversal (CVE-2018-0426), command injection (CVE-2018-0424) and information disclosure (CVE-2018-0425) bugs, all having a high severity.
Products with high severity vulnerabilities:
- Cisco Webex Meetings client for Windows – privilege escalation (CVE-2018-0422 )
- Cisco Webex Teams – information disclosure and modification (CVE-2018-0436)
- Cisco SD-WAN Solution – certificate validation (CVE-2018-0434), command injection (CVE-2018-0433), privilege escalation (CVE-2018-0432)
- Cisco Prime Access Registrar – denial of service (CVE-2018-0421)
- Cisco Integrated Management Controller – command injection (CVE-2018-0430 and CVE-2018-0431)
- Cisco Data Center Network Manager – privilege escalation to the underlying operating system (CVE-2018-0440)
To read the original article:
