When it was released back in 2015, one of the main perks of Windows 10 was the improved security features that made it harder for rootkits to get a foothold on Microsoft’s new OS.
But three years later, security researchers from Romania-based antivirus vendor Bitdefender say they’ve discovered a new adware strain named Zacinlo that uses a rootkit component to gain persistence across OS reinstalls, a rootkit component that’s even effective against Windows 10 installations.
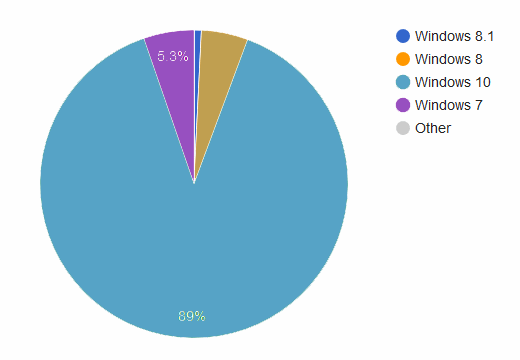
In fact, researchers say that 90% of all Zacinlo’s recent victims are Windows 10 users, showing that crooks intentionally designed their « product » to work against Microsoft’s latest OS.
Zacinlo group active since 2012
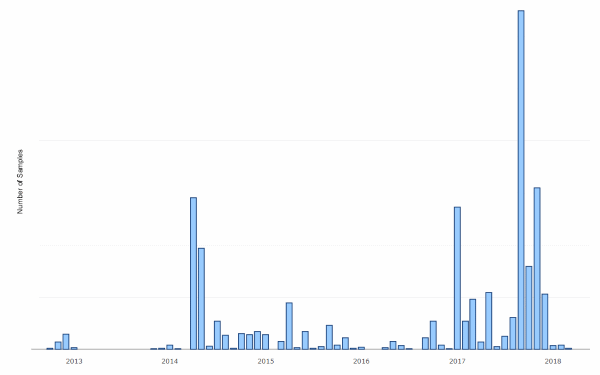
But it wasn’t always so. According to researchers, the group behind Zacinlo have been in business since 2012, and have been distributing their malware all this time.
The adware’s distribution came in surges of activity, with big spikes in 2014, 2015, and especially in 2017 and 2018. It is believed that in these two past years, Zacinlo added its rootkit component that can work on Windows 10.
 |
 |
 |
« The adware components are silently installed by a downloader that is presented as a free and anonymous VPN service (s5Mark), » Bitdefender experts wrote in a 102-page report detailing Zacinlo’s modus operandi and all of its modules released today.
Finding a powerful threat like Zacinlo in the s5Mark app isn’t a surprise as this app was previously categorized as a PUP (Potentially Unwanted Program) for a long time.
This VPN app —actually more of a proxy— didn’t and still doesn’t do that much, to begin with, but it serves its purpose of initial point of infection and « downloader » for Zacinlo’s other modules.
Of all these modules, the rootkit one is the most important, as it can ensure the adware survives on infected hosts for weeks, months, or years.
Furthermore, this same rootkit module is also utilized to stop processes deemed dangerous to the functionality of the adware while also protecting the adware from being stopped or deleted.
Zacinlo has some pretty dangerous privacy intrusive features
There is also a module for carrying out man-in-the-middle (MitM) attacks to intercept traffic, even HTTPS one. While this feature could allow it to intercept banking sessions and tamper with online payments, Zacinlo has been using this feature mainly to injects ads into any web pages it wants.
Another module that stands out is one that can detect and remove competing adware. Bitdefender says this module isn’t very advanced, but is something not seen in most adware families.
Zacinlo also comes with regular adware components that harvest local system information, transmit it to a remote command and control server, and then receive commands from it. These commands allow the adware’s master to uninstall or delete any local services he deems dangerous, like the ones specific to security software.
But besides the rootkit and the MitM component there is another Zacinlo module that sends shivers down your back, and that’s its « screenshoting » module that can take screengrabs off the victim’s screen, similar to a feature often found in RATs (remote access trojans).
« This functionality has a massive impact on privacy as these screen captures may contain sensitive information such as e-mail, instant messaging or e-banking sessions, » Bitdefender says.
Zacinlo used mainly for clickjacking and ad fraud
Further, Zacinlo also comes with a self-update feature to upgrade its components with new versions, the ability to install any software it wants on the victims’ systems, a « redirector » module to make users forcibly navigate to a web page, and an ad replacer to push its own ads part of affiliate schemes into users’ browsing sessions.
Last but not least, Zacinlo also runs a Chromium-based headless browser in the background where it loads web pages and ads on which it silently clicks to generate profits for crooks.
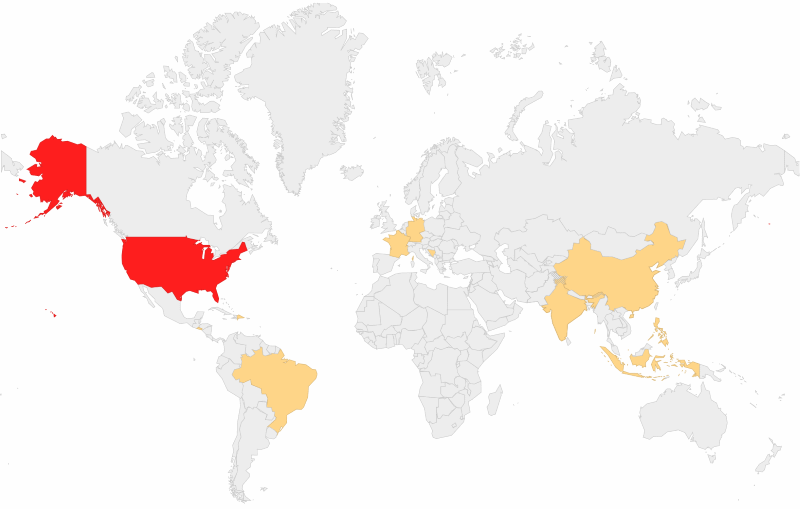
Overall, this is a dangerous threat that’s been silently spreading for the least six years, and most of its victims have been spotted in the US, with others also seen in France, Germany, Brazil, China, India, Indonesia, and the Philippines.
