For more than a week hackers have started scanning the Internet, searching for machines running Oracle WebLogic servers.
Scans started after April 17, when Oracle published its quarterly Critical Patch Update (CPU) security advisory.
The April 2018 CPU contained a patch for CVE-2018-2628, a vulnerability in the WLS core component of WebLogic, a Java EE application server.
This security issue received a severity score of 9.8 out of 10 because it could allow attackers to execute code on remote WebLogic servers without needing to authenticate.
PoC published online last week
The flaw was discovered and reported by Liao Xinxi of NSFOCUS Security Team and an independent security researcher named loopx9.
A day after the Oracle patches, Xinxi published a blog post on a Chinese social network, explaining how the vulnerability works. Leveraging this info, a user named Brianwrf created and released proof-of-concept (PoC) code on GitHub that could exploit this flaw.
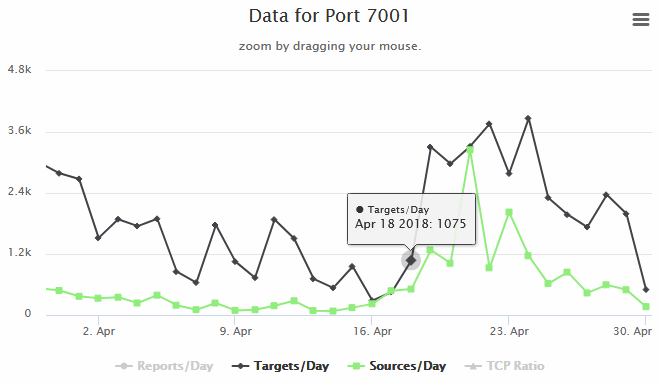
The publishing of a fully-weaponized PoC led to an immediate spike in scans for port 7001, the port running the vulnerable WebLogic « T3 » service.
 |
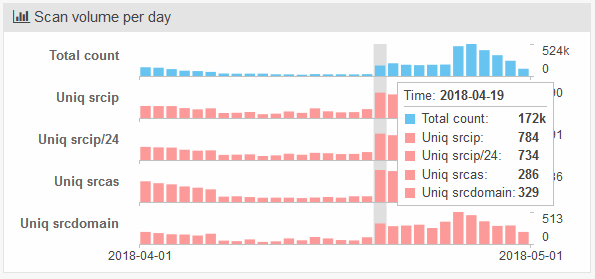 |
Cyber-security firm GreyNoise, the one who first spotted the port 7001 scan spike, said at the time that « opportunistic exploitation has not yet been confirmed, » meaning crooks were only scanning the web to look for vulnerable machines, merely to assess the total pool of exploitable machines.
We have asked the GreyNoise team to keep Bleeping Computer informed of the first signs of hackers moving in to capitalize this flaw for actual intrusions.
But while we have not heard back from GreyNoise during the past week, things got worse over the weekend, but for different reasons.
Oracle CVE-2018-2628 patch is incomplete
According to an Alibaba Cloud engineer, Oracle appears to have botched the CVE-2018-2628 patch, and there’s a way to bypass the April 2018 patch and exploit the flaw even on supposedly patched WebLogic systems.
To read the original article:
