Security researchers from Duo Labs and the US Computer Emergency Response Team Coordination Center (CERT/CC) will release security advisories today detailing a new SAML vulnerability that allows malicious attackers to authenticate as legitimate users without knowledge of the victim’s password.
The flaw affects SAML (Security Assertion Markup Language), an XML-based markup language often used for exchanging authentication and authorization data between parties.
SAML’s most important use if in single sign-on (SSO) solutions that allow users to log into accounts using one single identity. Unlike other shared authentication schemes —such as OAuth, OpenID, OpenID Connect, and Facebook Connect— SSO stores the user’s identity on a central server on which users have accounts.
When users try to login into other enterprise apps, those apps (service providers – SP) make requests to the local SSO server (identity provider – IdP) via SAML.
Flaw caused by XML comment handling
In a report that’s going to go live later today, Duo Labs researchers reveal a design flaw that affects various SSO software and several open-source libraries meant to support SAML-based SSO operations.
The flaw is how these libraries handle XML comments inserted in the middle of a SAML response request. For example, researchers have noticed that if an attacker inserts a comment inside the username field in such a way that it breaks the username, the attacker might gain access to a legitimate user’s account.
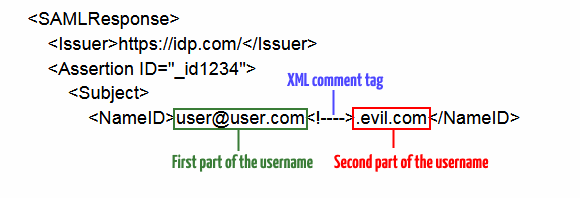
The only condition for an attacker to exploit this flaw is to have a registered account on the victim’s network, so it can query the SAML provider and forge requests to « trick SAML systems into authenticating as a different user. »
Flaw affects multiple vendors, open-source libraries
Duo Labs researchers say they identified multiple SSO vendors vulnerable to such attacks and vendors that used one of the following libraries to parse SAML’s XML-based authentication requests.
OneLogin – ruby-saml – CVE-2017-11428
Clever – saml2-js – CVE-2017-11429
OmniAuth-SAML – CVE-2017-11430
Shibboleth – CVE-2018-0489
Duo Network Gateway – CVE-2018-7340
However, Duo Labs says this isn’t a flaw that affects « all » SAML-based SSO providers in the same way, or even at all.
« The presence of this behavior is not great, but not always exploitable. SAML [identity providers] and [service providers] are generally very configurable, so there is lots of room for increasing or decreasing impact, » the Duo Labs team says.
Researchers recommend disabling public registration of user accounts on sensitive networks and vetting each user manually to avoid attackers registering an account on internal networks in the first place.
If this is not possible, network admins can configure a whitelist of accepted email address domain names to limit who can register on the network, albeit this is not a reliable protection measure and a determined attacker will find a way around it.
The attack is not possible against accounts protected by two-factor authentication (2FA) solutions.
UPDATE: The Duo Labs technical report is available here. The CERT/CC advisory is scheduled to go live later today at this link.
To read the original article:
