Just three months after Princeton researchers were warning users of the dangers of « session replay » attacks, developers of malicious Chrome extensions have incorporated this « trick » into their latest « releases. »
The term « session replay » refers to JavaScript code that records user activity and then plays it back in exact detail. Over the past several years, web analytics firms have added support for « session replay » features in their dashboard, allowing website owners to analyze how users were utilizing their website. These are valuable A/B testing tools if used for legitimate reasons.
Crooks abusing Yandex Metrica « session replay » script
Over the past several weeks, several malicious Chrome extensions have started embedding a JavaScript library provided by web analytics provider Yandex Metrica, which records user actions on all the sites they surf.
While Yandex Metrica does not record text entered in password fields, the script can still log various sorts of details, such as names, credit card numbers, CVV numbers, email addresses, and phone numbers.
Below is a GIF of what the operators of these malicious Chrome extensions are seeing when replaying a user session.
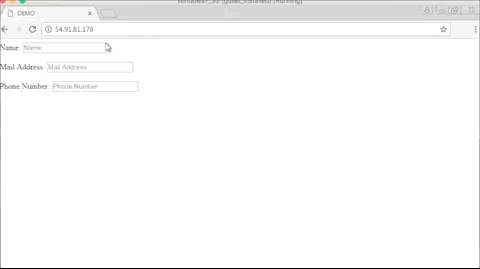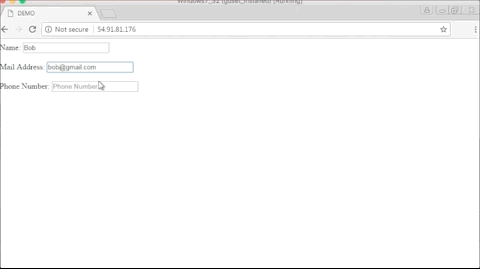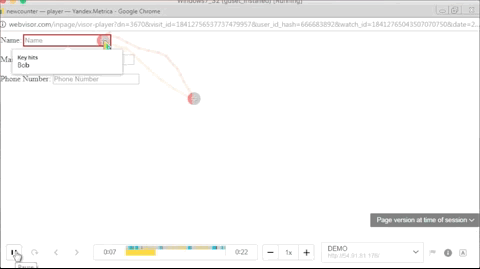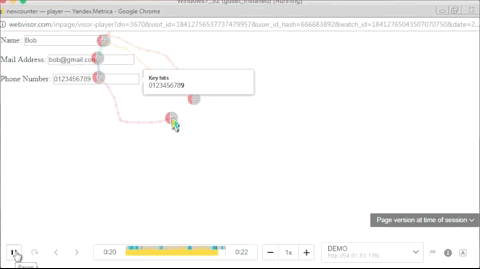
While Bleeping Computer’s Lawrence Abrams has found quite a few of these malicious Chrome extensions —for which has provided removal instructions [e.g.: Strawberry Daiquiri Cocktail, BrowserWatch, 11 Pumpkin Flavored Foods, To Deodorize Laundry]— Trend Micro has tracked down a few more.
The company says it has found 89 of these malicious Chrome extensions, which have a total install count of over 423,000.
The US cyber-security firm has published today a list containing the names of 58 Chrome extensions. If users find they installed any of these, they can use the removal instructions template from the links above to get rid of these threats.
Extensions created by the same group —Droidclub
Trend Micro believes these extensions were created by the same group and tracks the entire operation as Droidclub, after the domain name of one of the command and control servers (droidclub[.]net).
These extensions have a C&C server infrastructure because the the session record/replay scripts aren’t the only malicious code they deploy on victim’s Chrome browsers.
The main purpose of these extensions is to inject advertising in all pages a user is viewing, generating a profit for the Droidclub gang.
Older versions of these extensions also deployed the Coinhive cryptojacking script that mined Monero using people’s CPUs, but the Coinhive script has been removed in newer versions.
Extensions are easy to spot and avoid
All these extensions follow the same pattern, using random names and non-sensical descriptions. From Bleeping Computer’s observations, most of these extensions didn’t last more than a day, with the Chrome team removing them from the official Web Store before they could do more harm.
To read the originala article: