A massive malware outbreak that attempted to infect over 400,000 users during a 12-hour period was caused by a backdoored Russian-based BitTorrent client named MediaGet.
The outbreak happened last Tuesday, on March 6. Microsoft said that the Windows Defender team picked up and stopped a massive malware operation that came out of the blue and attempted to infect mostly Russian and Turkish users with the Dofoil (Smoke Loader) trojan.
Microsoft published an in-depth report of how the malware operated, revealing Dofoil would later try to download and install a Monero miner.
At the time, Microsoft did not reveal how Dofoil landed on users’ computers, mainly because it was not entirely sure. Now, the company has published more details, and according to the Windows Defender team, the Dofoil malware landed on users’ computers via a file named my.dat, created by mediaget.exe —the MediaGet BitTorrent client’s binary.
MediaGet hack happened in mid-February
« Our continued investigation on the Dofoil outbreak revealed that the March 6 campaign was a carefully planned attack with initial groundwork dating back to mid-February, » the Windows Defender team said today in a new report.
Microsoft alleges hackers broke into MediaGet’s infrastructure, and sometimes between February 12 and 19, attackers managed to replace the official MediaGet installer with one that also included a backdoor.
Hackers then allowed for a two-week window so users would install or update to the new MediaGet versions, the one containing the backdoor.
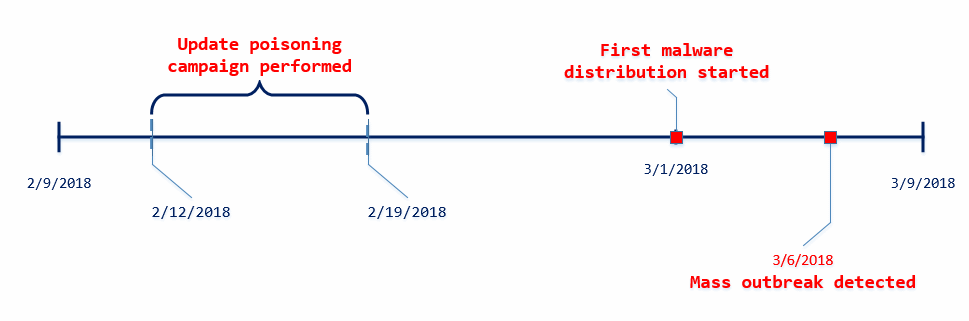
Attackers started running first tests on March 1, by using the backdoor to plant malware on users’ computers and sprung their main attack on March 6, when they delivered the Dofoil+coinminer malware combo.
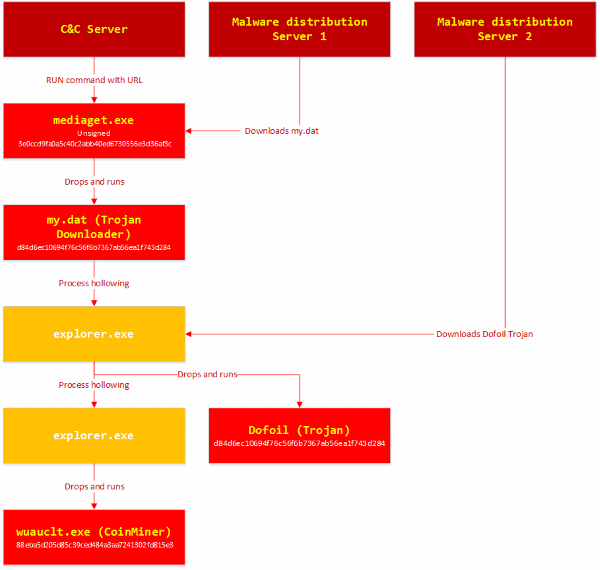
During their attack, crooks also used a stolen digital certificate to sign the poisoned MediaGet update, in an attempt to avoid detection.
Microsoft said it notified both MediaGet and the company’s whose certificate crooks have abused. Bleeping Computer could not reach MediaGet for additional comments on the incident, mainly to clarify how hackers broke into their network.
Supply chain attacks are very efficient
This incident is not the first time when hackers broke into websites to poison a BitTorrent client with malware. Previously, hackers breached the site of the Transmission BitTorrent client on two separate occasions. First, they distributed the KeRanger ransomware, and later the Keydnap infostealer malware, both incidents aimed at Mac users.
Hackers have also breached other software distribution websites in the past to insert malware into downloadable files. Other incidents include phpBB, Elmedia Player, HandBrake, and Linux Mint.
But, of course, the most prominent supply chain attack still remains the NotPetya ransomware outbreak—carried out via a tainted update for M.E.Doc, a Ukrainian accounting software program.
