On the malware scene, there is no clearer sign of trends to come than the leaking of a malware family’s source code. Based on this assumption, we can now expect an influx of Point-of-Sale malware in the coming months after the release of the source code of the TreasureHunter PoS […]
Année : 2018
Faster Payments: Effective Fraud Mitigation Strategies
The Faster Payments Task Force is working toward launching a real-time payments network in the U.S. by 2020. But faster payments could open the door to more fraud, as has been experienced in other countries, such as the U.K. and Mexico. Meanwhile, the U.S. has already experienced fraud exploits on a […]
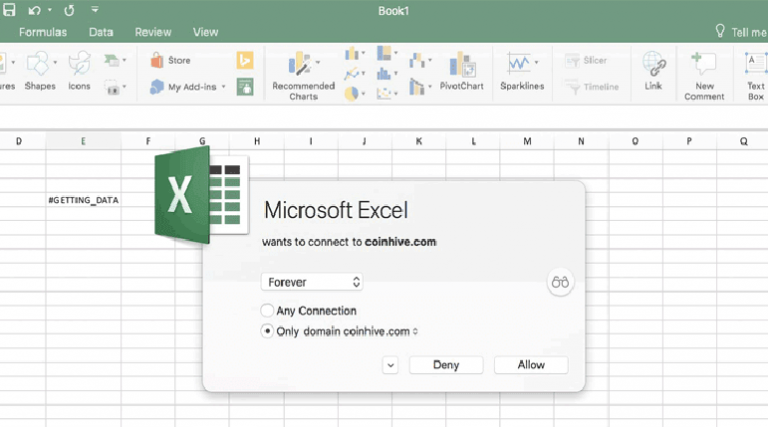
Microsoft Adds Support for JavaScript in Excel—What Could Possibly Go Wrong?
hortly after Microsoft announced support for custom JavaScript functions in Excel, someone demonstrated what could possibly go wrong if this feature is abused for malicious purposes. As promised last year at Microsoft’s Ignite 2017 conference, the company has now brought custom JavaScript functions to Excel to extend its capabilities for better work […]
Are you using Python module ‘SSH Decorator’? Newer versions include a backdoor
A backdoor was discovered in the Python module named SSH Decorator (ssh-decorate), that was developed by Israeli developer Uri Goren. Are you using the Python module ‘SSH Decorator’? You need to check the version number, because newer versions include a backdoor. The library was developed to handle SSH connections from Python code. […]
Copenhagen city’s bicycle sharing system hacked; 1,800 bikes affected
You have heard about ride-sharing companies like Uber and Careem becoming victims of large-scale cyber attacks but now a bike sharing company has been hacked after falling for a damaging cyber attack. The computer system responsible for controlling and managing operations of Denmark’s Copenhagen city’s bicycle sharing system “Bycyklen” was hacked over the weekend […]
Office 365 Zero-Day Used in Real-World Phishing Campaigns
A new zero-day vulnerability known as baseStriker allows miscreants to send malicious emails that bypass security systems on Office 365 accounts. Discovered last week, on May 1, 2018, by security researchers from Avanan, baseStriker is a flaw in how Office 365 servers scan incoming emails. The HTML tag at the […]
Adobe Patch Tuesday Is Out With Fixes for Flash Player, Creative Cloud, Connect
Minutes ago, Adobe published this month’s batch of security fixes, part of the company’s regular Patch Tuesday outing. For the month of May 2018, Adobe fixed five vulnerabilities — one in Flash Player, three in the Creative Cloud Desktop application (the app that starts Photoshop, Illustrator, InDesign, and the rest […]
FBI: CYBER-FRAUD LOSSES RISE TO REACH $1.4B
About 301,580 consumers reported cyber-fraud and malware attacks to the FBI’s Internet Crime Complaint Center (IC3) last year – with reported losses exceeding a whopping $1.4 billion. The year’s haul of reports brings the overall total of complaints since the IC3 began recording such things to 4 million. Top threats […]
Line Feeds for Everyone! Notepad Now Supports Unix & Mac EOL Characters
If you have ever copied or opened a Unix file in the Windows Notepad, you would have seen that the result is very ugly as all of the text appears as a mess on one line as Notepad does not recognize Linux End of Line (EOL) characters. This is all going […]
« Hide and Seek » Becomes First IoT Botnet Capable of Surviving Device Reboots
Security researchers have discovered the first IoT botnet malware strain that can survive device reboots and remain on infected devices after the initial compromise. This is a major game-changing moment in the realm of IoT and router malware. Until today, equipment owners could always remove IoT malware from their smart […]