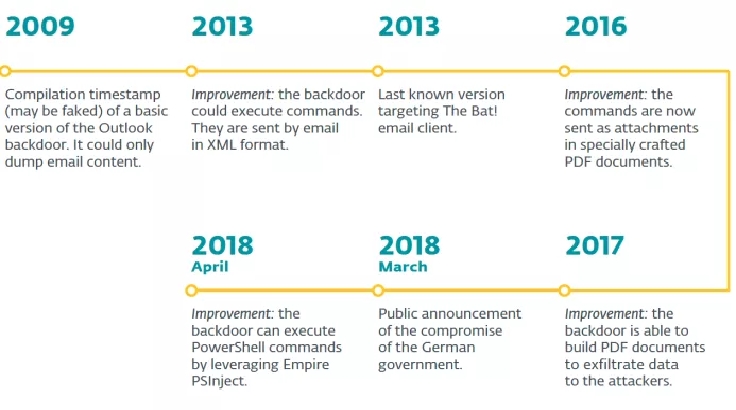
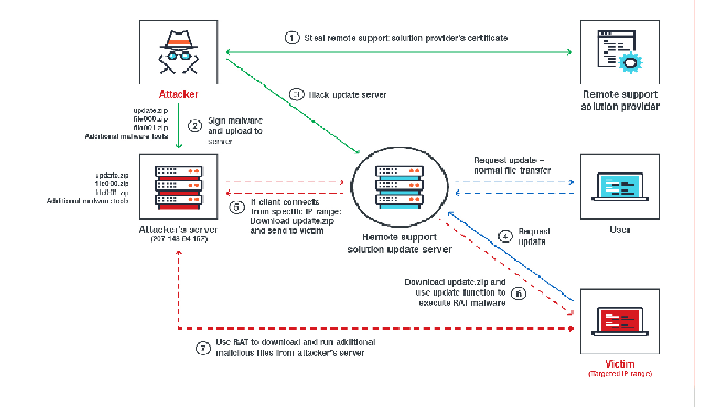
Malware researchers from ESET have published a detailed report on the latest variant of the Turla backdoor that leverages email PDF attachments as C&C. Malware researchers from ESET have conducted a new analysis of a backdoor used by the Russia-linked APT Turla in targeted espionage operations. The new analysis revealed a list of […]
Année : 2018
Bitdefender spotted Triout, a new powerful Android Spyware Framework
Security researchers from Bitdefender have spotted a new Android spyware framework dubbed Triout that could be used to create malware with extensive surveillance capabilities. Bitdefender researchers have identified a new spyware framework can be used to spy into Android applications, it is tracked as Triout and first appeared in the wild on May 15. The […]
Ryuk Ransomware Attack on various Enterprise Network Around the World & Earned $640,000
Newly spreading Ryuk Ransomware campaign targeting various enterprise network around the globe and encrypting various data in storage, personal computers, and data center. The attacker made over $640,000 from various victims by demanding 15 BTC to 50 BTC in order to retrieve their files and some of the organization from the […]
Beware of Dangerous Android Triout Malware That Records Phone Calls, Videos and Steals Pictures
A new Android malware strain dubbed Triout found bundled with a repackaged app contains surveillance capabilities and ability to hide the presence in the device. Security researchers from Bitdefender identified the new Triout malware that contains extensive surveillance capabilities. The malware appears to be first uploaded to virustotal from Russia […]
2.6 billion records exposed in 2,308 disclosed data breaches in H1
According to a report from cyber threat intelligence firm Risk Based Security some 2.6. billion data records have been exposed in data breached in the first half of 2018. According to a new report titled “Mid-Year 2018 Data Breach QuickView” published by the cyber threat intelligence company Risk Based Security some 2.6. […]
Marap modular downloader opens the doors to further attacks
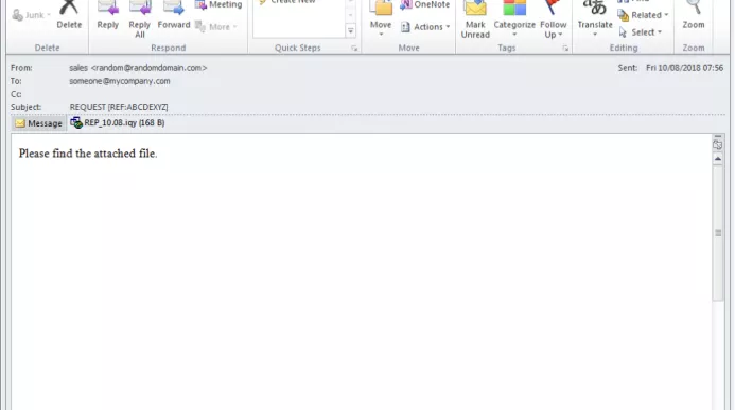
Overview Proofpoint researchers recently discovered a new downloader malware in a fairly large campaign (millions of messages) primarily targeting financial institutions. The malware, dubbed “Marap” (“param” backwards), is notable for its focused functionality that includes the ability to download other modules and payloads. The modular nature allows actors to add […]
Unusual Malspam campaign targets banks with Microsoft Publisher files
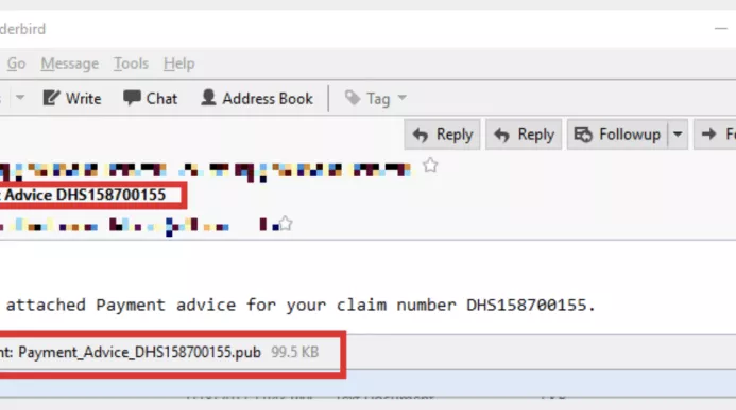
Researchers from Trustwave have uncovered a malspam campaign targeting banks with the FlawedAmmyy RAT. The peculiarity of this malspam campaign is the unusual use of a Microsoft Office Publisher file to infect victims’ systems. Experts noticed an anomalous spike in the number of emails with a Microsoft Office Publisher file (a .pub attachment) and the subject line, “Payment Advice,” […]
Linux Kernel Project rolled out security updates to fix two DoS vulnerabilities
Linux kernel maintainers have rolled out security updates for two DoS vulnerabilities tracked as SegmentSmack and FragmentSmack. Linux kernel maintainers have released security patches that address two vulnerabilities, tracked as two bugs are known as SegmentSmack (CVE-2018-5390) and FragmentSmack (CVE-2018-5391). potentially exploitable to trigger a DoS condition. The vulnerabilities reside the Linux kernel’s […]
Microsoft Cortana Vulnerability Allows Hackers to Browse With Your Locked Computer
A new privilege escalation vulnerability with Cortana allows an attacker with physical access to do unauthorized browsing on the locked system. Security researchers form Mcafee observed two different scenario’s, in the first scenario attackers, can force Microsoft Edge browser to navigate to the URL hosted in attacker’s server, with the second case […]
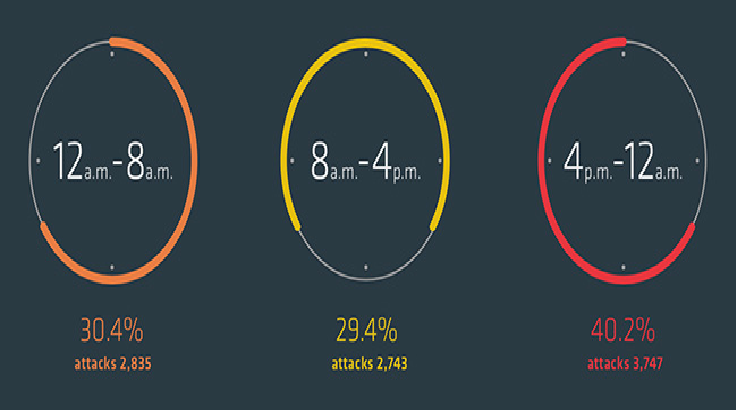
DDoS attackers increasingly strike outside of normal business hours
DDoS attack volumes have increased by 50% to an average of 3.3 Gbps during May, June and July 2018, compared to 2.2 Gbps during the previous quarter, according to Link11. Attacks are also becoming increasingly complex, with 46% of incidents using two or more vectors. While attack volumes increased, researchers recorded a […]