Even though phishing attacks can be quite convincing, a give away is when diligent users notice that the login form is unsecured or the SSL certificate is clearly not owned by the company being impersonated. A new Office 365 phishing attack utilizes an interesting method of storing their phishing form hosted on Azure Blob Storage in order to be secured by a Microsoft SSL certificate.
Azure Blob storage is a Microsoft storage solution that can be used to store unstructured data such as images, video, or text. One of the advantages of Azure Blob storage is that it accessible using both HTTP and HTTPS, and when connecting via HTTPS, will display a signed SSL certificate from Microsoft.
Phishing attack uses Azure blob storage to impersonate Microsoft
The use of Azure Blob storage to host a phishing form is exactly the type of attack cloud security provider Netskope recently discovered. In this attack, bad actors are sending out spam emails with PDF attachments that pretend to be from a law firm in Denver.
These attachments are named « Scanned Document… Please Review.pdf » and simply contain a button to download a supposed PDF of a scanned document.
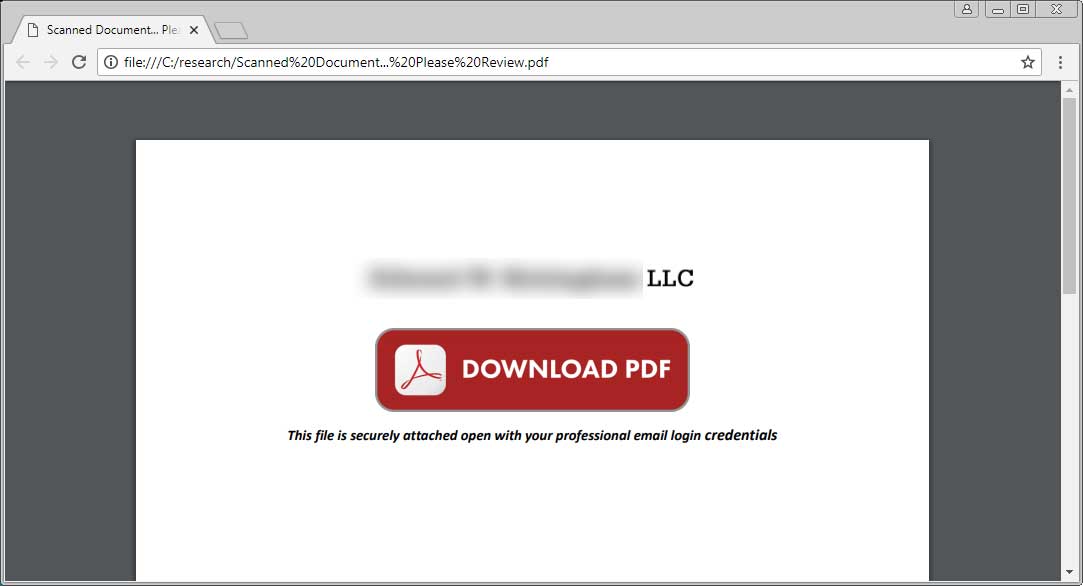
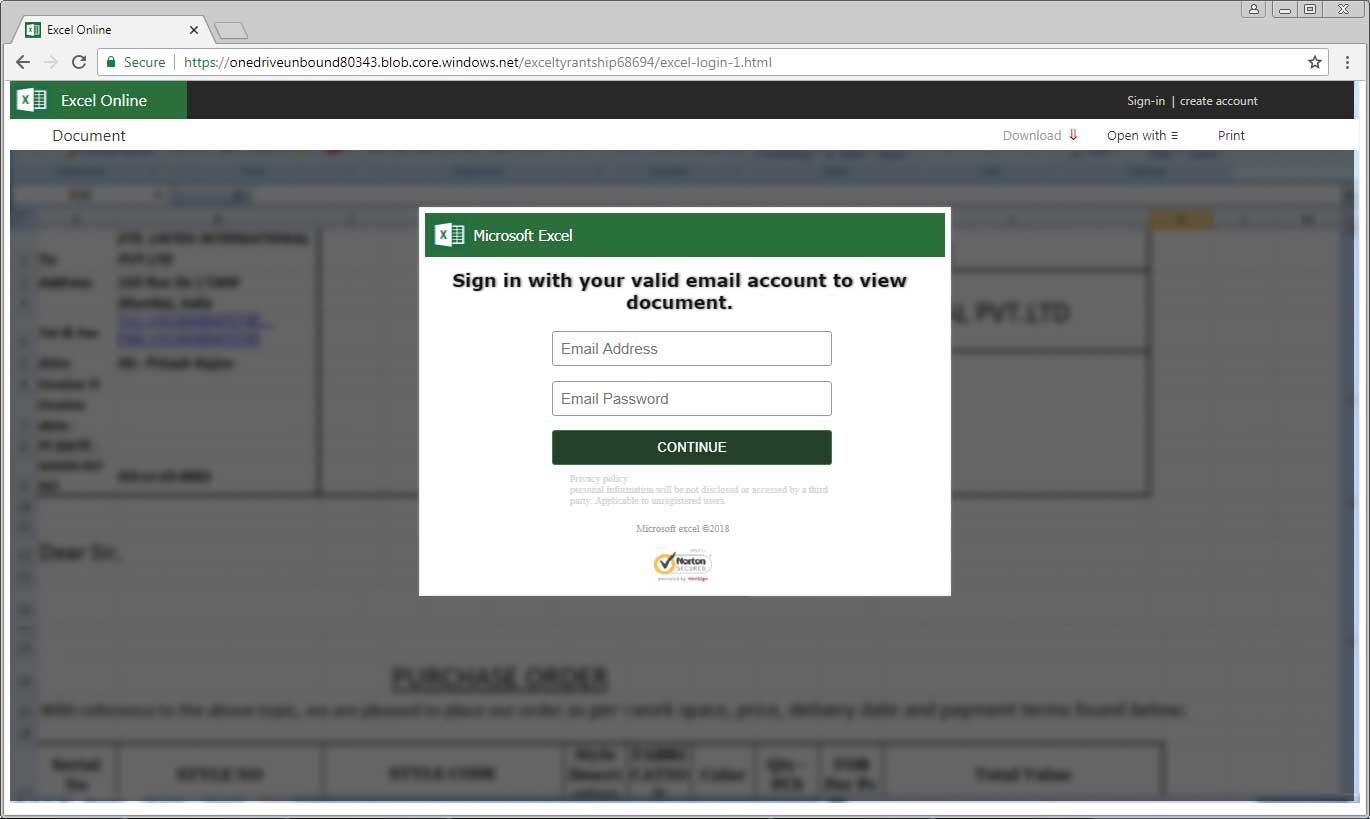
When users click on this link they will be brought to a HTML page pretending to be a Office 365 login form that is stored on the Microsoft Azure Blob storage solution. Notice how the URL https://onedriveunbound80343.blob.core.windows.net indicates it is a blob. As this page is also being hosted on a Microsoft service, it gets the benefit of being a secured SSL site as well.
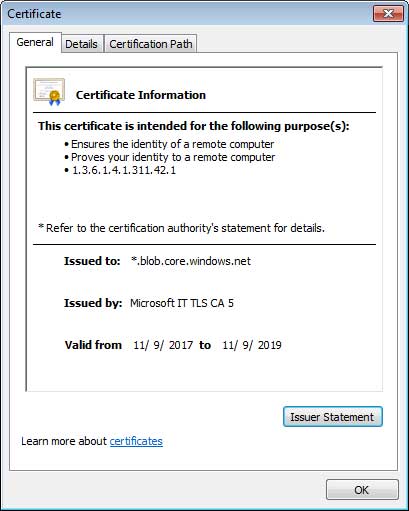
For those users who may be suspicious of the strange URL, if they look at the certificate they will see that the page is signed by a SSL certificate issued by Microsoft IT TLS CA 5.
As this is a supposed Office 365 login and the site is secured using a Microsoft SSL certificate, many may be convinced that this is a legitimate sign-in form.
Once a user enters their information, the form will submit the contents to a server operated by the attackers.
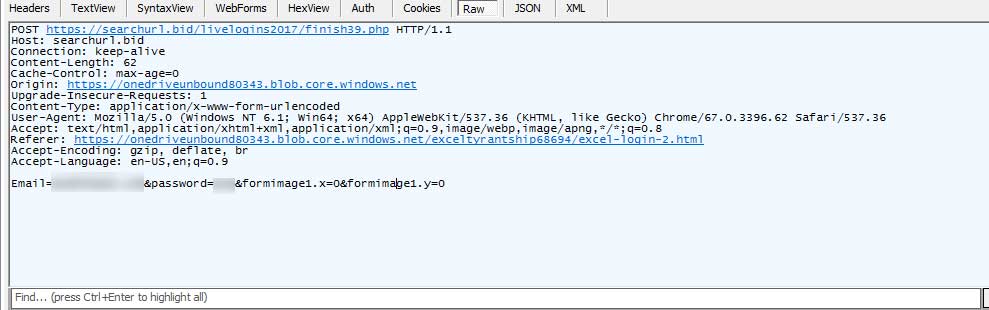
After the form is submitted, the page will pretend to get the document ready to be downloaded, but will ultimately just redirect the user to the https://products.office.com/en-us/sharepoint/collaboration Microsoft site.
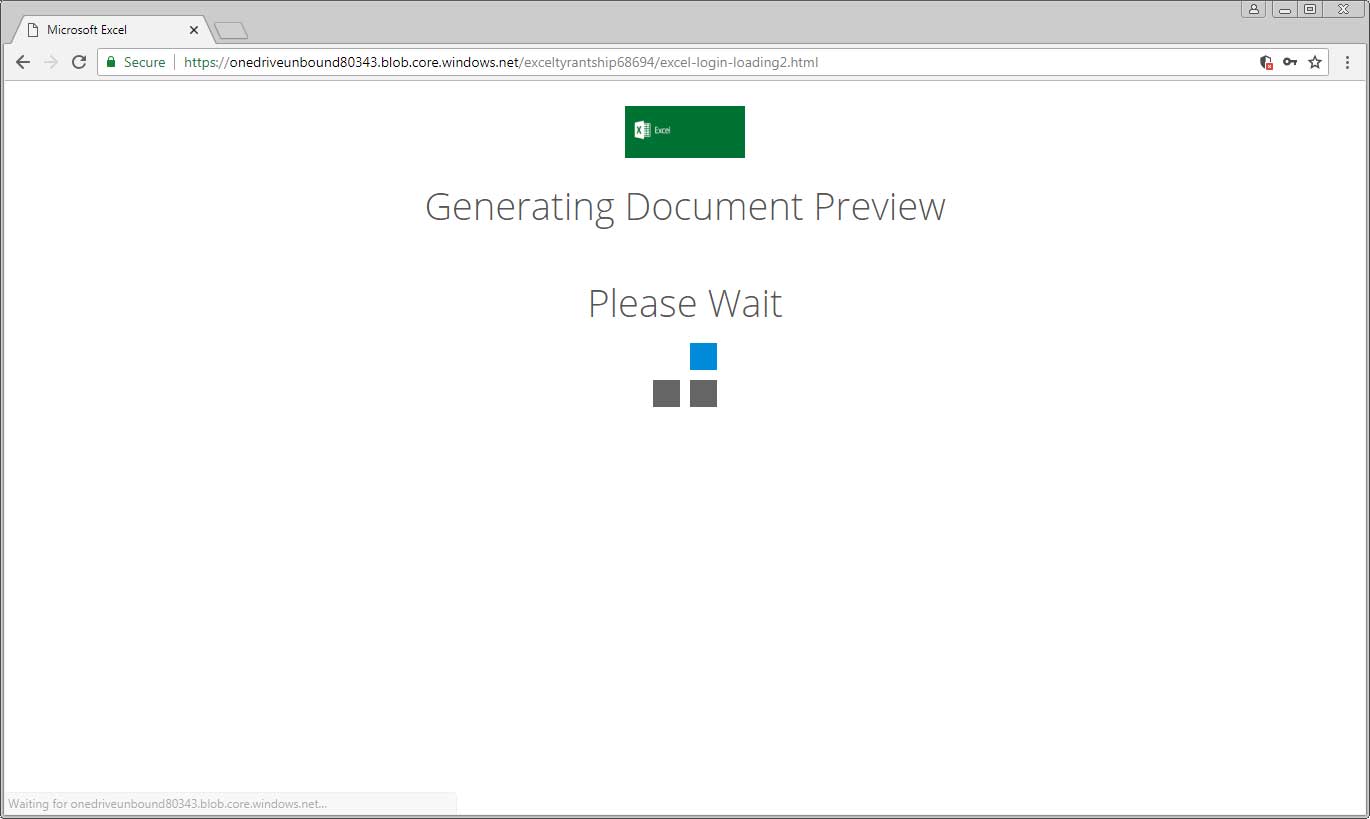
While more experienced users may not fall for this attack due to the strange URL, others may be more convinced because the page utilizes a certificate from Microsoft and thus must be safe.
To better protect users from these types of evolving threats,Netskope recommends that companies properly educate their users to recognize non-standard web page addresses.
« Enterprises should educate their users to recognize AWS, Azure, and GCP object store URLs, so they can discern phishing sites from official sites. »
To read the original article:
