Firefox engineers are working on a method to address the recent rise in usage of in-browser miners (cryptojacking scripts) that are, in most cases, ruining the web surfing experience of most users.
Plans to address this growing scourge were revealed in an email interview Bleeping Computer had with Peter Dolanjski, Product Manager of Firefox, in regards to the recent publishing of the Firefox feature roadmap for 2018.
One of the topics not included in the roadmap was « cryptojacking, » so we decided to ask the Mozilla executive about it.
« Currently, Firefox’s Tracking Protection feature already blocks some leading cryptojacking scripts, » Dolanjski told us. « We are exploring individual controls which would allow users to specifically block cryptojacking scripts. »
Throttling or domain blocking
This « exploring » on the part of Mozilla could mean one of two things. The first would be if Firefox would start throttling JavaScript « workers » executed in background tabs, similar to the method the Chrome team recently took to deal with cryptojackers.
Discussions on this possible feature is already taking place on the Mozilla bug tracker, here.
The other alternative would be if this anti-cryptojacking protection would be part of Firefox’s upcoming « ad filter system » that Mozilla plans to add to Firefox this year, to protect users from today’s toxic advertising landscape. More details on that, here.
Firefox Tracking Protection blocks Coinhive & Crypto-Loot
As for Firefox’s current anti-cryptojacking protection, we took a look at it to see how useful this was. The cryptojacking blocking system is currently hidden in Firefox Tracking Protection, a feature that prevents Firefox from loading scripts from abusive ad trackers.
We say hidden because Mozilla never advertised they were actively blocking cryptojacking domains via this feature.
In its current form, the Firefox Tracking Protection is powered via the Disconnect.me blocklist, a list of domains associated with advertisers that have a habit of secretly tracking users across multiple sites.
Since November 16, this list has also been blocking the domains of Coinhive and Crypto-Loot, two companies that provide in-browser mining services.
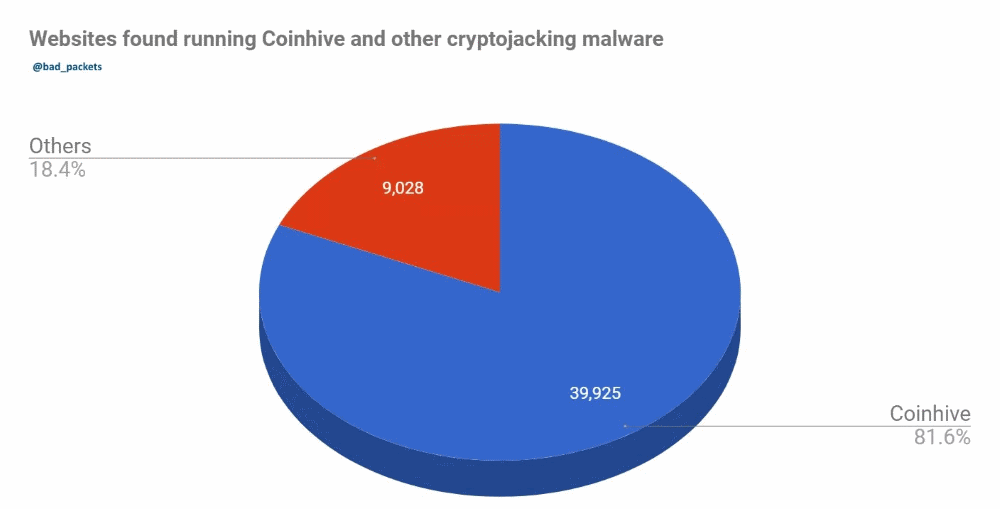
One might say blocking two domains wouldn’t be enough to make a dent. But according to statistics Bleeping Computer received from US security researcher Troy Mursch, the Coinhive JS script is found on 81.6% of all web domains that include a cryptojacking script, while Crypto-Loot is ranked #5 on that list, so, despite blocking just two domains, this list covers quite a lot of ground.
The only problem is that most users didn’t know this cryptojacking blocking feature was in the Tracking Protection feature all this time.
Second, this feature is not turned on by default, being only active when users start a private browsing window. Sure, since Firefox 57 users can enable Tracking Protection at all times, but the feature is not optimized for normal browsing, and most people will have a hard time staying logged in on most sites.
Nonetheless, in spite of which path Mozilla chooses —throttling background tabs or blocking cryptojacking domains outright— users will most likely embrace this new feature, especially since Mozilla has a habit of putting these new features under about:config flags or settings panel options, where users can turn them on or off as they see fit.
to read the original article: