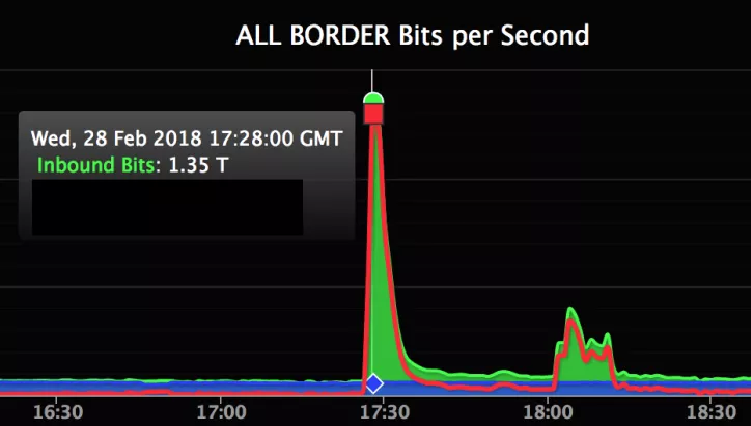
A mitigation mechanism is available for all victims who are under a DDoS attack carried out via Memcached servers.
This mitigation technique relies on the attacked victim sending a « flush_all » command back to the attacking servers. The measure was proposed last week by Dormando, one of the Memcached server developers.
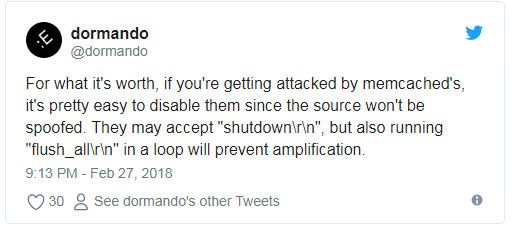
Dormando’s advice didn’t receive the attention it deserved until today, after a Corero press release.
The company announced that it integrated this basic mitigation mechanism inside its DDoS mitigation solution and found it « to be 100% effective » during a live attack.
« It has not been observed to cause any collateral damage, » Corero experts said about the « flush_all » technique.
Companies under DDoS attack from Memcached servers and who can’t afford DDoS mitigation services, can, in theory, create scripts that implement the two « shutdown » and « flush_all » commands recommended by Dormando. These commands shut down attacking servers, or clear their cache of any malicious packets that cause the amplification effect of the DDoS attack.
Memcached v1.5.6 fixes DDoS attack vector
These DDoS attacks are happening because of Memcached servers left accessible online. In their default configuration, these servers expose port 11211, which attackers are using to reflect and amplify DDoS attacks.
The Memcached team has taken steps to address this configuration issue (CVE-2018-1000115). On February 27, they released Memcached v1.5.6 that disables the UDP protocol by default and requires users to explicitly enable UDP support when deploying Memcached servers.
But besides a new secure version of Memcached being rolled out, the huge media coverage has also driven many server owners to take action.
Number of vulnerable Memcached servers goes down
Rapid7 reported today that Memcached servers with port 11211 open on the Internet has dropped from 18,000 on March 1 to under 12,000 on March 5.
Security researcher Victor Gevers has reported seeing the same thing, albeit with different numbers.