The Colorado Department of Transportation (DOT) has shut down over 2,000 computers after some systems got infected with the SamSam ransomware on Wednesday, February 21.
The agency’s IT staff is working with its antivirus provider McAfee to remediate affected workstations and safeguard other endpoints before before reintroducing PCs into its network.
DOT officials told local press that crucial systems were not affected, such as those managing road surveillance cameras, traffic alerts, message boards, and others. The agency’s Twitter feed continued to show traffic alerts after the agency shut down much of its employees’ IT network.
Colorado DOT will not pay the ransom
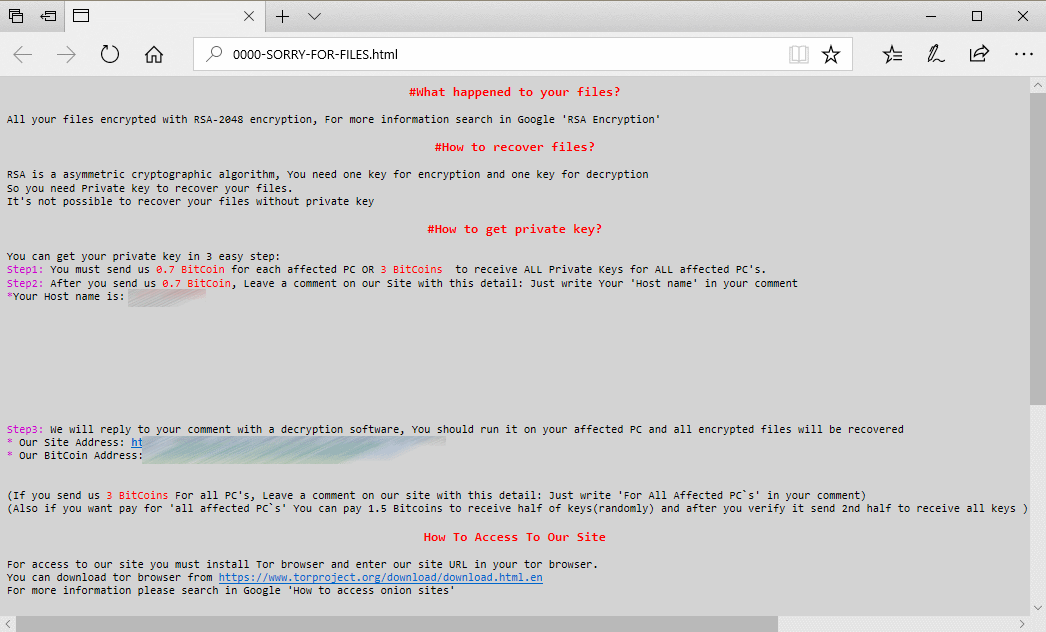
In a rare sign of transparency, officials revealed the name of the ransomware —SamSam. This is the same ransomware strain that infected hospitals, city councils, and ICS firms in January.
The hackers made over $300,000 from those attacks. One of the victims, an Indiana hospital agreed to pay a $55,000 ransom demand despite having backups. Hospital officials said it was easier and faster to pay the ransom than restore all its computers’ data from backups.
DOT officials said they don’t intend to follow suit by paying the ransom demand and they will restore from backups.
SamSam ransomware making a comeback
The SamSam ransomware is a ransomware strain that’s been deployed by a single group. Infection occurs after attackers gain access to a company’s internal networks by brute-forcing RDP connections.
Attackers then try to gain access to as many computers on the same network as possible, on which they manually run the SamSam ransomware to encrypt files.
In the recent campaigns, SamSam operators usually asked for a 1 Bitcoin ransom and left a message of « I’m sorry » on victims’ computers.
The SamSam group had been previously active in the winter of 2016 but have come back with new attacks. These new attacks have been detailed in reports published by Bleeping Computer, Secureworks, and Cisco Talos.
To read the original article::
