Intel may be facing as many as eight new Spectre-level vulnerabilities in its chips, a new report alleges. The report comes months after the Spectre and Meltdown flaws first rocked the silicon industry in early 2018.
German magazine c’t reported on Thursday that the new security flaws in Intel CPUs have been reported to the manufacturer by many different teams of researchers. While the magazine held back on reporting exact details about the vulnerabilities, it says that they are caused by the “same design problem.”
“Protecting our customers’ data and ensuring the security of our products are critical priorities for us. We routinely work closely with customers, partners, other chipmakers and researchers to understand and mitigate any issues that are identified, and part of this process involves reserving blocks of CVE numbers,” An Intel spokesperson told Threatpost. “We believe strongly in the value of coordinated disclosure and will share additional details on any potential issues as we finalize mitigations. As a best practice, we continue to encourage everyone to keep their systems up-to-date.”
According to c’t, each of the eight vulnerabilities has its Common Vulnerabilities and Exposures (CVE) number reserved, along with corresponding patches. Four of these flaws are classified as “high risk,” and the remaining are rated as “medium,” the magazine stated. One of the flaws touts a significantly higher threat potential than that of Spectre, as it essentially simplifies attacks across system boundaries. Making matters worse, one of the flaws – more so than Spectre – can be easily exploited for attacks across system boundaries, according to the publication.
“Specifically, an attacker could launch exploit code in a virtual machine (VM) and attack the host system from there – the server of a cloud hoster, for example,” according to c’t. “Alternatively, it could attack the VMs of other customers running on the same server. Passwords and secret keys for secure data transmission are highly sought-after targets on cloud systems and are acutely endangered by this gap. Intel’s Software Guard Extensions (SGX), which are designed to protect sensitive data on cloud servers, are also not Spectre-safe.”
C’t alleged that Google Project Zero has discovered one of the flaws. A Google spokesperson did not respond to a request for comment.
Google’s security team was also responsible for the January disclosure of Spectre and Meltdown, which account for three variants of a side-channel analysis security issue in server and desktop processors, could potentially allow hackers to access users’ protected data.
While Spectre and Meltdown have impacted Intel processors, AMD has said in a statement it was potentially vulnerable to the Spectre variant, but that “we believe it is difficult to exploit Variant 2 on AMD processors.”
The new vulnerabilities show “initial evidence” that they might impact some ARM CPUs, and further investigations are underway to see if AMD is also susceptible.
In order to protect against Spectre and Meltdown in the future, Intel has said it designed a new set of CPU design features that work with the operating system to install “virtual fences” protecting the system from speculative execution attacks that could exploit a variant of the Spectre flaw.
Another infamous aspect of the Spectre and Meltdown story is the messy patching efforts across the industry in the wake of the vulnerability disclosure. Intel initially released patches addressing the Spectre and Meltdown vulnerabilities in January, but later yanked its patches for the Variant 2 flaw – both for client compute and data center chips – after acknowledging that they caused “higher than expected reboots and other unpredictable system behavior.”
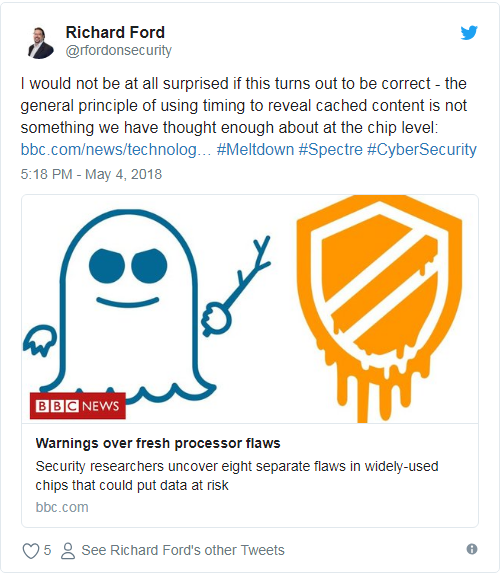
IT professionals, for their part, are stressing that chip manufacturers need to take responsibility for thinking through security in a more holistic way at the chip level. Richard Ford, chief scientist at Forcepoint, took to Twitter to say companies have not thought through chip security when it comes to “using timing to reveal cached content.”
he magazine says that the vulnerabilities will be disclosed on May 7 in accordance with the 90 day vulnerability disclosure deadline; that is also the day before the next Windows patch day.
“Intel is already working on its own patches for Spectre-NG and developing others in cooperation with the operating system manufacturers,” according to c’t. “According to our information, Intel is planning two waves of patches. The first is scheduled to start in May; a second is currently planned for August.”
To read the original article
https://threatpost.com/report-intel-facing-new-spectre-like-security-flaws/131714/