Precisely two months on the day since the release of its first version, the group behind the Rapid ransomware strain has released v2.0 today.
This new version has not suffered any major modifications compared to its previous release, but small changes have occurred.
The biggest is the addition of a code routine that detects the user’s PC locale settings before launching encryption operations. If the user has locale settings set to Russian, the ransomware will not encrypt files.
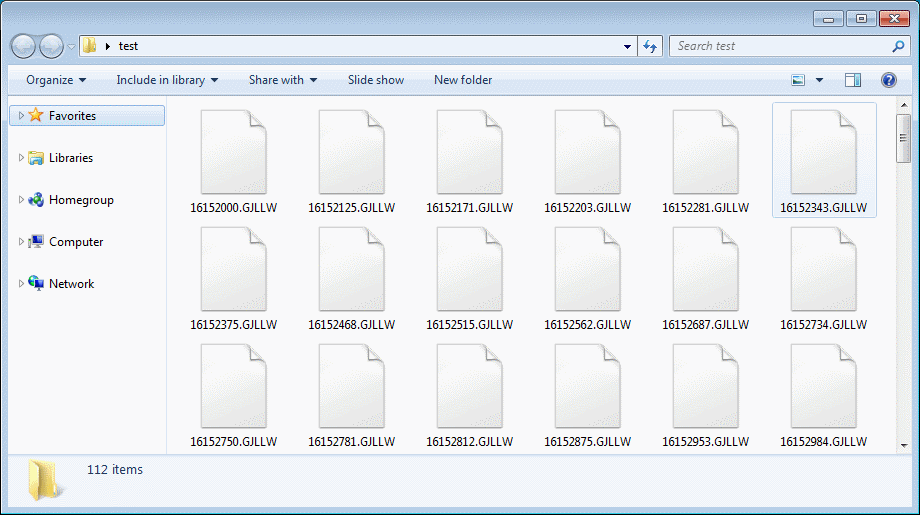
Second, the ransomware now adds a randomly generated string as the file extension at the end of encrypted files. Version 1.0 used « .rapid », which allowed victims to easily detect what ransomware strain had infected their PCs.
But users now can detect they’ve been infected with Rapid 2.0 because the ransom note says so right at the top. The ransom note also uses different wording, compared to v1.0, and a subsequent updated version that was deployed in fake IRS malspam campaign.
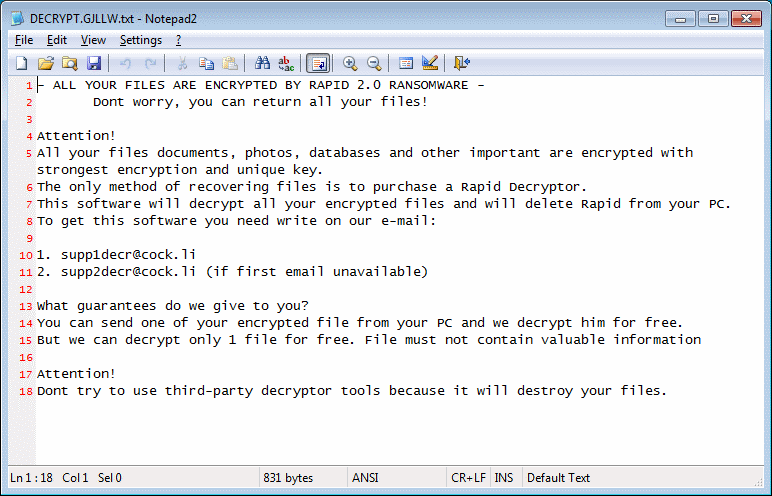
Rapid 2.0 still relies on asking victims to get in contact with the ransomware’s operators via email. This version uses supp1decr@cock.li and supp2decr@cock.li as contact addresses.
First spotted by security researcher MalwareHunter, Rapid 2.0 seems to have been released into the wild by accident, as the ransomware’s source code was not packed and included debug messages that helped researchers quickly analyze its source code. The AVCrypt ransomware, also spotted for the first time today, was also not packed, revealing its secrets to researchers in a similar manner.
Bleeping Computer is not aware of any attempts to mass-distribute this threat at the time of writing, but the Rapid crew were quite successful at distributing v1.0, so they do have the channels in place to switch to mass-distributing v2.0 if they wish to.
To read the original article:
https://www.bleepingcomputer.com/news/security/rapid-20-ransomware-released-will-not-encrypt-data-on-pcs-with-russian-locale/
