Proof-of-concept code to run massive DDoS attacks using unsecured Memcached servers has been published online this week, along with a ready-made list of over 17,000 IP addresses belonging to vulnerable Memcached servers.
Two, and not one, of such proof-of-concept (PoC) utilities, have been released, both uniques in their own way.
PoC #1
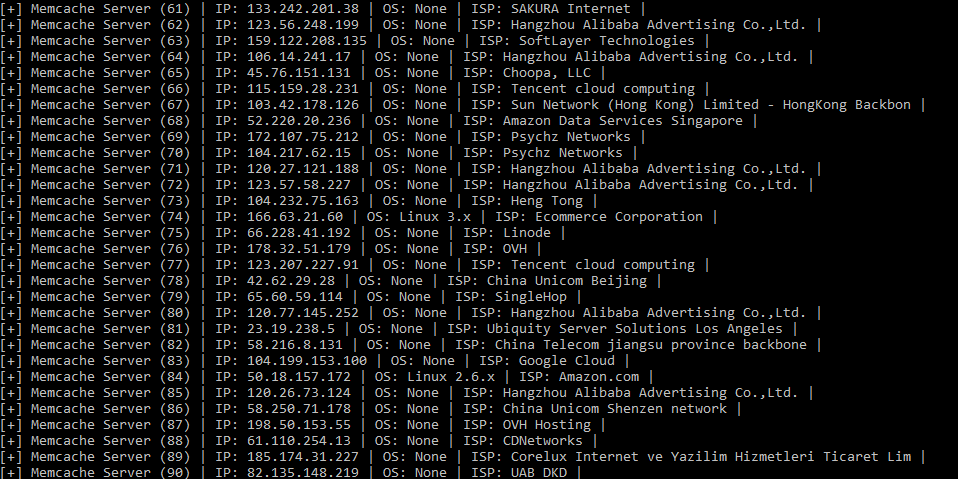
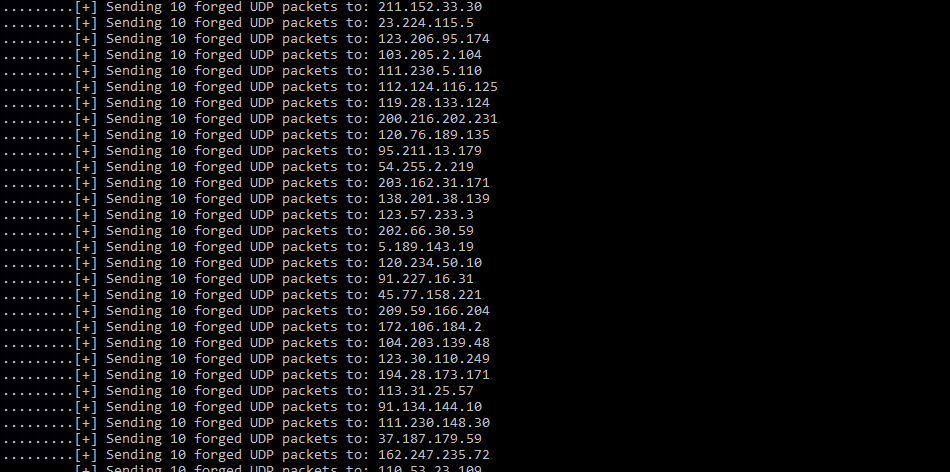
The first is a Python script named Memcacrashed.py that scans Shodan for IPs of vulnerable Memcached servers and allows a user to launch a DDoS attack against a desired target within seconds of running the tool.
The creator of this tool is —surprisingly— the infosec researcher behind the Spuz.me blog.
 |
 |
PoC #2
The second PoC was released on Pastebin on Monday. The author is unknown, and the PoC is written in C.
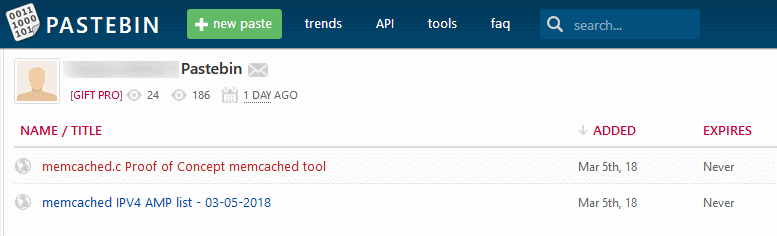
This Pastebin repo also comes with a list of over 17,000 IPs belonging to vulnerable Memcached servers. The C script will launch DDoS attacks by using the IPs from this list to reflect and amplify traffic towards the target of the DDoS attack.
Publishing of the PoC code was not a suprise
Memcached-based DDoS attacks gained public attention last week when Cloudflare reported seeing such attacks in the real world. Cloudflare’s report got a lot of media attention because Memcached servers would amplify incoming UDP packets for up to 51,200 times, allowing an attacker with a small bandwidth to launch humongous-sized DDoS attacks.
In the last week, the DDoS record has been broken twice because of Memcached-based DDoS attacks. GitHub suffered a 1.3 Tbps attack last week, and an unnamed US service provider suffered an attack of 1.7 Tbps this week.
Most industry experts expected PoC code to be released, so this news won’t surprise any infosec aficionados. The publicly accessible PoCs will just make it easier for more low-skilled actors to launch attacks of their own.
« I bet the DDoS-as-a-Service industry has Memcached included in their offerings by next week, » said Daniel Smith, a security researcher for US cyber-security firm Radware.
Most Memcached server owners don’t care
The only way to fix this is for the Memcached team to issue an update that fixes the UDP protocol implementation to remove the DDoS attacks’ amplification factor.
But applying these updates may take a while. In the meantime, some security researchers are fighting an uphill battle with owners of Memcached servers.
For example, Victor Gevers, Chairman of the GDI Foundation, has been contacting Memcached server owners for almost two years, advising companies to secure servers and place them behind a firewall.
« It’s sour to see [DDoS attacks] finally happen after more than two years of warnings. Sometimes you don’t want to be right, » Gevers told Bleeping Computer.
« It’s so frustrating finding the owners, warning them of the risks, and getting them to act. Because there is no risk of a data breach, people are hardly or not responding at all to our emails, » Gevers says.
« And the threat of large volume DDoS attacks is not shrinking. Now with PoC tools and ready-to-go lists in public, we will see a significant increase of Memcached amplification attacks after the coming weekend, I guess. »
The only bright spot is that many cloud service providers are aggressively rate-limiting outbound 11211 UDP ports in attempts of having their infrastructure abused in DDoS attacks, according to Justin Paine, Trust & Safety at CloudFlare.
To read the original article: