ASCO is the latest headline-making organization to be hit by ransomware, prompting many companies to consider what to do to minimize their risk. A ransomware attack on Belgian airplane manufacturer ASCO this week is the latest in a string of incidents that show the unique danger lurking in this type […]
Facebook to stop Huawei pre-installing apps on smartphones
Facebook is reportedly planning to stop Chinese tech giant Huawei from pre-installing its applications on future Huawei smartphones. According to Reuters, new Huawei smartphone models will not have Facebook, WhatsApp, or Instagram pre-installed. There will, or would have been, a business deal in place between Facebook and Huawei to allow […]
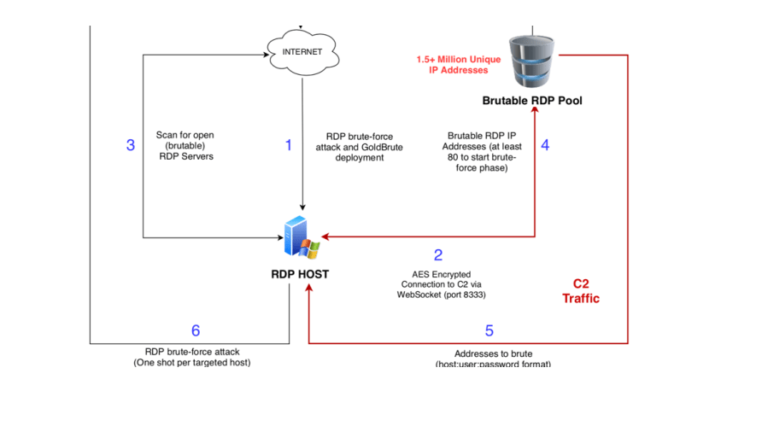
New GoldBrute Botnet is attempting to infect 1.5 Million RDP Servers
A new botnet tracked as GoldBrute is scanning the web for Windows machines with Remote Desktop Protocol (RDP) connection enabled. A new botnet tracked as GoldBrute has appeared in the threat landscape, it is scanning the web for Windows machines with Remote Desktop Protocol (RDP) connection enabled. The botnet is […]
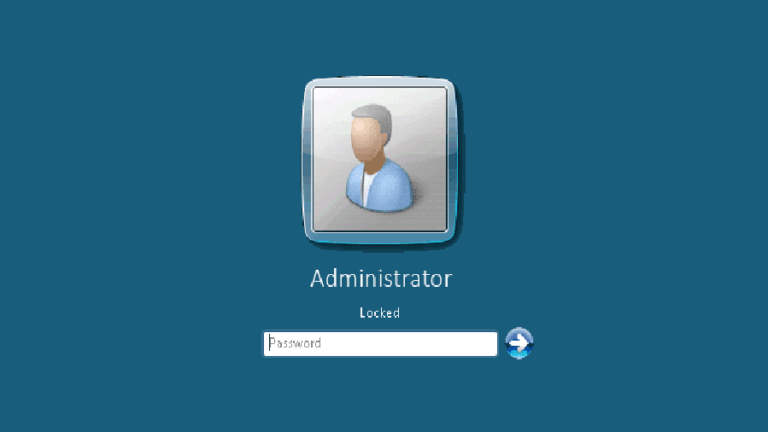
Unpatched Bug Let Attackers Bypass Windows Lock Screen On RDP Sessions
A security researcher today revealed details of a newly unpatched vulnerability in Microsoft Windows Remote Desktop Protocol (RDP). Tracked as CVE-2019-9510, the reported vulnerability could allow client-side attackers to bypass the lock screen on remote desktop (RD) sessions. Discovered by Joe Tammariello of Carnegie Mellon University Software Engineering Institute (SEI), the […]
Hackers Stole Customers’ Credit Cards from 103 Checkers and Rally’s Restaurants
If you have swiped your payment card at the popular Checkers and Rally’s drive-through restaurant chains in past 2-3 years, you should immediately request your bank to block your card and notify it if you notice any suspicious transaction. Checkers, one of the largest drive-through restaurant chains in the United […]
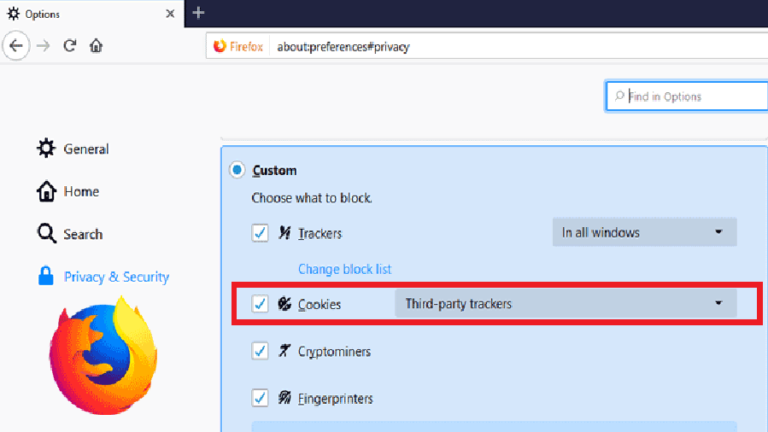
Firefox Web Browser Now Blocks Third-Party Tracking Cookies By Default
As promised, Mozilla has finally enabled « Enhanced Tracking Protection » feature on its Firefox browser by default, which from now onwards would automatically block all third-party tracking cookies that allow advertisers and websites to track you across the web. Tracking cookies, also known as third-party cookies, allows advertisers to monitor your […]
Critical Flaws Found in Widely Used IPTV Software for Online Streaming Services
Security researchers have discovered multiple critical vulnerabilities in a popular IPTV middleware platform that is currently being used by more than a thousand regional and international online media streaming services to manage their millions of subscribers. Discovered by security researchers at CheckPoint, the vulnerabilities reside in the administrative panel of Ministra […]
Leicester City Football Club disclosed a card breach
Leicester City Football Club disclosed a card breach that affected its website, hackers stole payment card data, including card numbers and CVVs. Leicester City Football Club revealed that hackers have breached its website (https://shop.lcfc.com/) and stole credit card data of people that bought products disclosed a card breach that affected […]
Google is taking action on deceptive installation tactics for Chrome Browser Extensions
Google aims at eliminating the use of deceptive installation tactics among Chrome browser extensions introducing a new policy. Google announced a new policy for Chrome browser extensions to eliminate the use of deceptive installation tactics. The additional changes are part of the Project Strobe presented by Google in October 2018 in the […]
Google is taking action on deceptive installation tactics for Chrome Browser Extensions
Google aims at eliminating the use of deceptive installation tactics among Chrome browser extensions introducing a new policy. Google announced a new policy for Chrome browser extensions to eliminate the use of deceptive installation tactics. The additional changes are part of the Project Strobe presented by Google in October 2018 in the […]