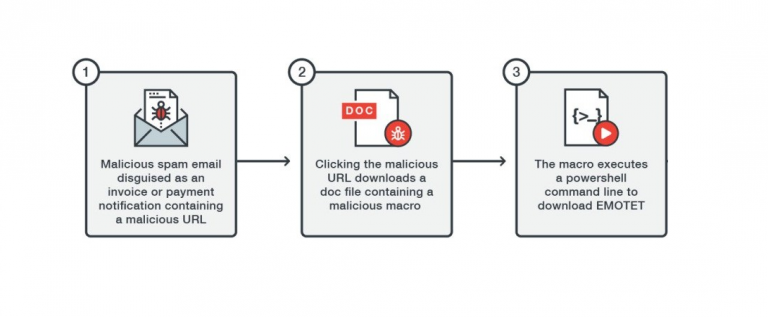
Trend Micro recently observed a new campaign leveraging the Ursnif banking Trojan using new malicious macro tactics payload delivery and evade detection. Researchers at Trend Micro have recently spotted a new campaign leveraging the Ursnif banking Trojan featuring new malicious macro tactics for payload delivery. Malicious macros are widely adopted by crooks […]
Protection des données personnelles
Vous êtes un consommateur de service? Lorsque vous commandez, achetez, communiquez, savez-vous où vont les informations personnelles ou confidentielles que vous confiez aveuglément ?Seriez-vous d’accord si toutes les données (coordonnées postales, e-mail, bancaires, santé, politique, religion, habitudes de consommation etc.) que vous communiquez en toute confiance à des tiers se […]
88 Percent of Java Apps Susceptible to Widespread Attacks from Known Security Defects, According to New Research from CA Veracode
The 2017 State of Software Security Report also shows that approximately 53.3 percent of Java applications rely on a vulnerable version of the Commons Collections components. Even today, there are just as many applications using the vulnerable version as there were in 2016. The use of components in application development […]
Microsoft provides details of a code execution vulnerability in Chrome
Microsoft’s Offensive Security Research (OSR) team disclosed a remote code execution vulnerability in the Chrome web browser. Microsoft’s Offensive Security Research (OSR) team has disclosed a remote code execution vulnerability in the Chrome web browser that was discovered by its experts. The flaw, tracked as CVE-2017-5121, was addressed by Google last month with […]
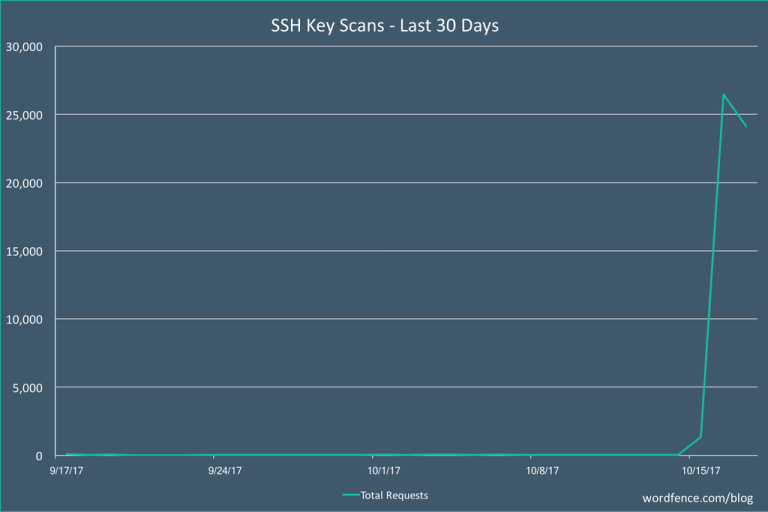
Threat actors started scanning for SSH Keys on websites
Threat actors in the wild are mass-scanning websites for directories containing SSH private keys to hack them. The SSH allows a secure way to connect to servers hosting the websites, it allows administrators to get a terminal on them and enter commands. The SSH authentication could rely on login credentials (username […]
Que faire si vous êtes victime d’une cyber-attaque ?
Vous détectez une activité anormale, une déconnexion, un ralentissement système… Après vérification, vous en êtes sûr, vous êtes attaqué. Ce dossier vous présentera quelques règles qu’il faut appliquer rapidement. Ces règles dépendent de vous : vous ne réagirez pas de la même façon si vous êtes un particulier qui surfe […]
Cyber espionage – China-Linked group leverages recently patched .NET Flaw
Security researchers at Proofpoint spotted a cyber espionage campaign conducted by a group previously linked to China. The hackers have been using a recently patched .NET vulnerability, tracked as CVE-2017-8759, in attacks aimed at organizations in the United States. “Proofpoint researchers are tracking an espionage actor targeting organizations and high-value […]
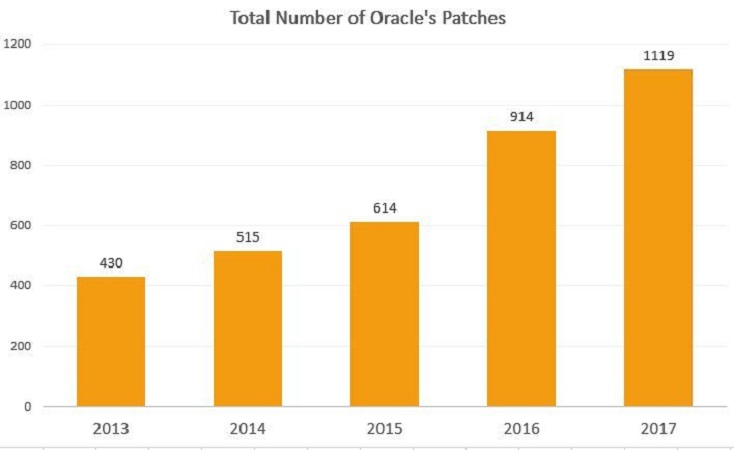
October 2017 Oracle Critical Patch Update addresses 252 Vulnerabilities
Oracle released the October 2017 Critical Patch Update (CPU) that addresses a total of 252 security vulnerabilities that affect multiple products. Most of the vulnerabilities fixed by Oracle could be remotely exploitable without authentication. This is the last Oracle Critical Patch Update of 2017, this year the tech giant already […]
Iranian hackers compromised the UK leader Theresa May’s email
« “Some 9,000 email accounts, including those belonging to Theresa May and other cabinet ministers, were subjected to a sustained attack on June 23. Ninety accounts were compromised.” “Whitehall officials admitted it was inevitable that the hackers had obtained sensitive material,” the Times reported. The investigation is still ongoing, for this […]
Ransomware attack on Toshiba forces it to halt production of NAND Flash
Ransomware attacks forced Toshiba to cease NAND flash memory production, costing the business the equivalent of 400,000TB in SSD storage. In fact, Toshiba downed tools for up to six weeks following the attack, reports DigiTimes. Subsequently, the production loss could trigger a NAND supply crisis. But production has now returned […]