Des réclamations de consommateurs déposées par HOP le 18 septembre dernier ont été entendues par le parquet de Nanterre, et ont mené à l’ouverture d’une enquête contre le fabricant américain d’imprimantes Epson, rapporte Euractiv relayant un article du JDLE. Obsolescence programmée, c’est le sujet de l’enquête. Dans le menu, fausse […]
VMWARE ISSUES 3 CRITICAL PATCHES FOR VSPHERE DATA PROTECTION
VMware, a Dell Technologies subsidiary, released several patches Tuesday fixing critical vulnerabilities affecting its vSphere cloud computing virtualization platform. The bugs address three vulnerabilities in VMware’s vSphere Data Protection (VDP), a backup and recovery solution used with its vSphere platform. According to the company, a remote attacker could exploit the […]
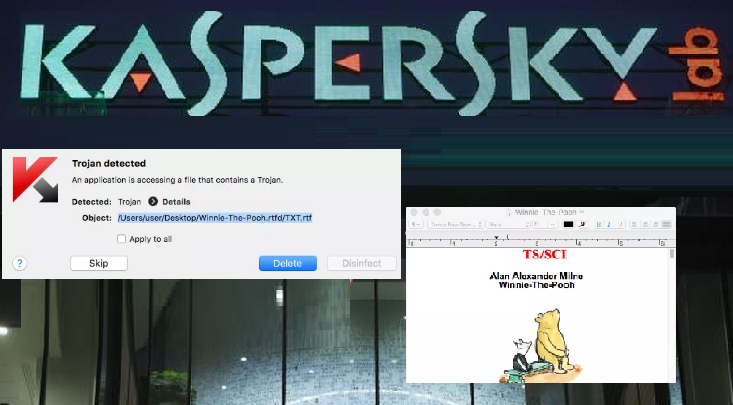
Former NSA hacker reversed Kaspersky Lab antivirus to compose signatures capable of detecting classified documents
Former NSA hacker, demonstrated how to subvert the Kaspersky Lab antivirus and turn it into a powerful search tool for classified documents. The Kaspersky case demonstrated that security software can be exploited by intelligence agencies as a powerful spy tool. Patrick Wardle, chief research officer at Digita Security and former NSA […]
Necurs botnet involved in massive ransomware campaigns at the end of 2017
The Necurs botnet made the headlines at year-end sending out tens of millions of spam emails daily as part of massive ransomware campaigns. Necurs was not active for a long period at the beginning of 2017 and resumed it activity in April. The Necurs botnet was used in the past months to push […]
MACOS LPE EXPLOIT GIVES ATTACKERS ROOT ACCESS
A researcher that goes by the handle “Siguza” released details of a local privilege escalation attack against macOS that dates back to 2002. A successful attack could give adversaries complete root access to targeted systems. Siguza released details of the attack on Dec. 31 via Twitter, wishing followers a “Happy […]
Critical Flaw Reported In phpMyAdmin Lets Attackers Damage Databases
A critical security vulnerability has been reported in phpMyAdmin—one of the most popular applications for managing the MySQL database—which could allow remote attackers to perform dangerous database operations just by tricking administrators into clicking a link. Discovered by an Indian security researcher, Ashutosh Barot, the vulnerability is a cross-site request […]
Cryptomonnaies : le Bitcoin bientôt rattrapé par l’Ether et le Ripple ?
Ethereum, Ripple, Litecoin… La liste des monnaies virtuelles susceptibles de rattraper le Bitcoin en ‘part de marché’ cette année s’allonge. Sur la base d’un cours actuel voisin de 13.500$ sur le ‘BTC’ (données Bitfinex), la capitalisation globale de marché du Bitcoin s’affiche désormais à un peu plus de 230 milliards […]
Google and Facebook are being threatened by Government of U.K for not sharing user data
Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de-radicalization plans, surveillance and other counter-terrorism actions. “If they remain to be less than co-operative, we should look at something like […]
Retour sur les cyberattaques de l’année 2017 et une vision sur l’année 2018
L’année 2017 s’est terminée…et a été comme prévu une année chargée en cybermenaces , une année qui a apporté son lot de menaces et la surveillance sur Internet franchit une nouvelle étape. Janvier 2017 On commence l’année sereinement avec une vague de cyberattaques dans le monde entier. Précisement le 23 janivier, Suite […]
Attention, grosse faille critique sur les smartphones Samsung
Si votre navigateur Samsung Internet n’est pas à jour, il vous faut y remédier de toute urgence. Une faille de sécurité permet le vol de nombreuses données personnelles. C’est une année 2018 qui ne commence pas de la meilleure façon pour Samsung avec la révélation d’une faille critique de […]