A change meant to improve Google Chrome performance will also indirectly impact cryptojacking scripts (in-browser cryptocurrency miners) and will severely reduce their efficiency. According to a design document seen by Bleeping Computer, Google engineers plan to limit the CPU power some types of JS scripts running in the browser’s background […]
Cyber Espionage Group Targets Asian Countries With Bitcoin Mining Malware
Security researchers have discovered a custom-built piece of malware that’s wreaking havoc in Asia for past several months and is capable of performing nasty tasks, like password stealing, bitcoin mining, and providing hackers complete remote access to compromised systems. Dubbed Operation PZChao, the attack campaign discovered by the security researchers […]
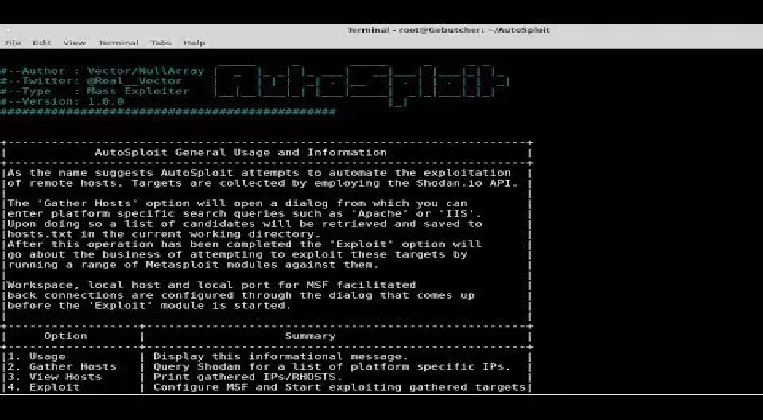
Automated Hacking Tool Autosploit Cause Concerns Over Mass Exploitation
The Autosploit hacking tool was developed aiming to automate the compromising of remote hosts both by collecting automatically targets as well as by using Shodan.io API. Users can define its platform search queries like Apache, IIS and so forth to gather targets to be attacked. After gathering the targets, the tool […]
Malicious Reddit clone fooling users into giving away logins
It recently came to light that cybercriminals have been deceiving ‘Reddit’ users into voluntarily handing over their usernames and passwords. Why would anyone do that of their own free will you might ask? It all comes down to a simple typo – reddit.co instead of reddit.com When users accidentally type […]
Google veut analyser vos habitudes de navigation pour accélérer le chargement des pages web
Un dépôt de brevet de Google mentionne le développement d’un algorithme d’analyse du comportement des utilisateurs et de leurs habitudes de navigation. L’objectif ? Diminuer le temps de chargement des pages web et améliorer la pertinence des résultats. Dans un dépôt de brevet découvert le 1er février, Google décrit un […]
DDoS attacks: How an 18-year-old got arrested for trying to knock out systems
Netherlands police’s high-tech crime unit has arrested an 18-year-old man on suspicion of launching distributed denial-of-service (DDoS) attacks on the Dutch tax authority, tech site Tweakers, and internet service provider Tweak. The police said the teenager, known only as ‘Jelle S’, is also suspected of attacking the online bank Bunq. […]
All Ledger hardware wallets vulnerable to man in the middle attack
Ledger hardware wallet that is currently operating in the cryptocurrency market is vulnerable to cyber attacks. The vulnerability was identified by unknown security researchers in every single hardware wallet that allows cybercriminals to show fraudulent addresses to Ledger users/customers. When funds are requested to these addresses, the cryptocurrency is transferred to […]
Joomla! 3.8.3: Privilege Escalation via SQL Injection
Joomla! is one of the biggest players in the market of content management systems. Its easy installation, usage, and extensibility make it the second most used CMS on the web next to WordPress1. Last year, our PHP static code analysis solution unveiled a rare LDAP injection vulnerability within the 500,000 […]
MacUpdate Hacked to Distribute Mac Cryptocurrency Miner
Another day, another cryptocurrency miner targeting users – This time, MacUpdate site has been hacked to drop cryptocurrency miner on Mac devices. MacUpdate, a well-known software download, and aggregator platform, has become a victim of a hack attack and the service is now distributing cryptocurrency miners to Mac users, revealed […]
Adobe rolled out an emergency patch that fixed CVE-2018-4878 flaw exploited by North Korea
Adobe rolled out an emergency patch that fixed two critical remote execution vulnerabilities, including the CVE-2018-4878 flaw exploited by North Korea. Adobe has rolled out an emergency patch to address two Flash player vulnerabilities after North Korea’s APT group was spotted exploiting one of them in targeted attacks. Last week, […]