Une faille dans un programme de messagerie largement utilisé qui peut exposerons quelques-uns 400,000 serveurs à l’échelle mondiale a été découvert par des chercheurs de sécurité. La vulnérabilité, qui a été identifié comme CVE-2018-6789 réside dans toutes les versions de l’agent de transfert de messages Exim (plus spécifiquement en fonction […]
Memcached DDoS Attacks: 95,000 Servers Vulnerable to Abuse
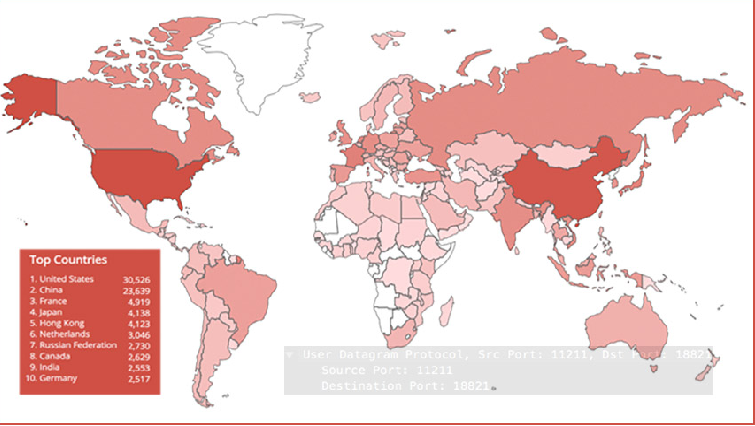
More than 95,000 servers could still be vulnerable to being abused to launch massive distributed denial-of-service attacks. The risk comes via Memcached, an open source utility designed to cache in RAM frequently used web pages. The web page caching utility was never designed to be internet-accessible and requires no authentication to […]
Hidden Cobra Targets Turkish Financial Sector With New Bankshot Implant
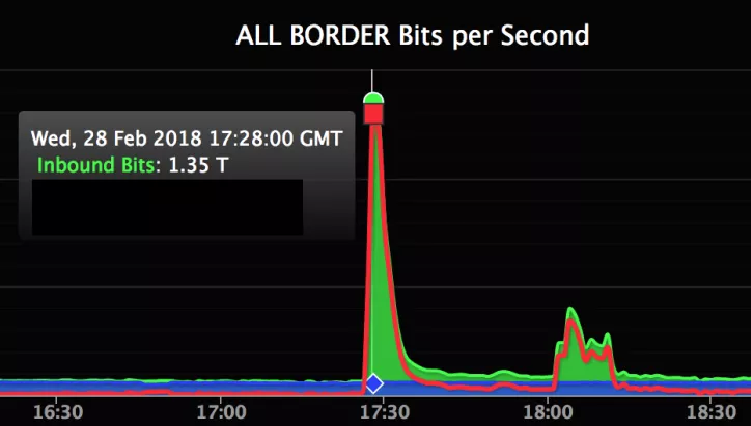
On February 28, the McAfee Advanced Threat Research team discovered that the cybercrime group Hidden Cobra continues to target cryptocurrency and financial organizations. In this analysis, we observed the return of Hidden Cobra’s Bankshot malware implant surfacing in the Turkish financial system. Based on the code similarity, the victim’s business […]
North Korea Suspected in Cyberattack on Turkey
SEOUL—Suspected North Korean hackers blitzed Turkish financial institutions and a government organization last week, seeking intelligence for a future heist, a new report says. The attacks on March 2 and 3, identified by cyber researcher McAfee LLC in a Thursday report, attempted to lure targets with faux links to a popular cryptocurrency […]
Multiples vulnérabilités dans Juniper Junos OS
De multiples vulnérabilités ont été découvertes dans Juniper Junos OS. Elles permettent à un attaquant de provoquer un déni de service à distance, un contournement de la politique de sécurité et une élévation de privilèges. RISQUE(S) Déni de service à distance Contournement de la politique de sécurité Élévation de privilèges […]
The state of Mac malware
Mac users are often told that they don’t need antivirus software, because there are no Mac viruses. However, this is not true at all, as Macs actually are affected by malware, and have been for most of their existence. Even the first well-known virus—Elk Cloner—affected Apple computers rather than MS-DOS […]
Gozi ISFB Remains Active in 2018, Leverages « Dark Cloud » Botnet For Distribution
EXECUTIVE SUMMARY Gozi ISFB is a well-known and widely distributed banking trojan, and has been in the threat landscape for the past several years. Banking trojans are a type of malware that attackers leverage in an attempt to obtain banking credentials from customers of various financial institutions. The source code […]
Cisco Prime Collaboration Provisioning Hard-Coded Password Vulnerability
Summary A vulnerability in Cisco Prime Collaboration Provisioning (PCP) Software could allow an unauthenticated, local attacker to log in to the underlying Linux operating system. The vulnerability is due to a hard-coded account password on the system. An attacker could exploit this vulnerability by connecting to the affected system via […]
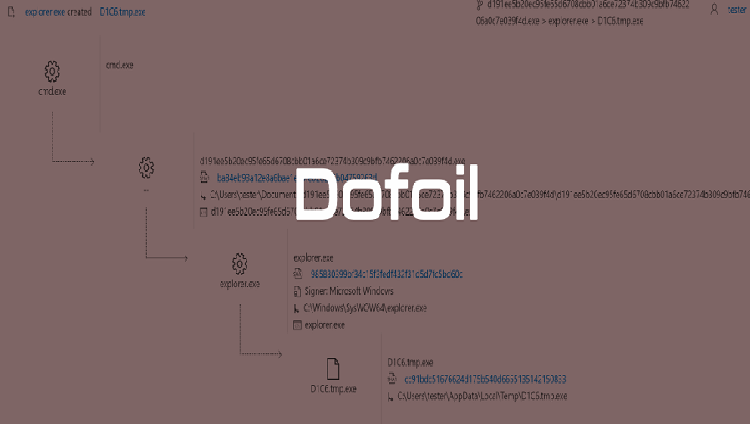
Microsoft Stops Malware Campaign That Tried to Infect 400,000 Users in 12 Hours
Microsoft revealed today that Windows Defender stopped a massive malware distribution campaign that attempted to infect over 400,000 users with a cryptocurrency miner during a 12-hour period on March 6, 2018. The Redmond-based OS maker attributes the detections to computers infected with the Dofoil malware —also known as Smoke Loader— […]
Corero Network discovered a Kill Switch for Memcached DDoS attacks
Corero network security discovers a “kill switch” for memcached DDoS attacks and also reveals memcached exploit can be used to steal or corrupt data Memcached DDoS attacks made the headlines due to the magnitude observed in recent offensives. While two PoC exploits for Memcached DDoS attacks have been released online, experts at security firm Corero […]